Get stories like this delivered straight to your inbox. Sign up for The 74 Newsletter
Kept in the Dark is an in-depth investigation into more than 300 K-12 school cyberattacks over the last five years, revealing the forces that leave students, families and district staff unaware that their sensitive data was exposed. Use the search feature below to learn how cybercrimes — and subsequent data breaches — have played out in your own community. Here’s what we uncovered about a massive attack on Minneapolis Public Schools.
Four days after an attack by a notorious ransomware gang disrupted the Minneapolis, Minnesota, school district’s computer network, accessing reams of students’ and educators’ sensitive information, officials contacted the FBI and laid out what happened.
The district “immediately initiated an investigation” after its Feb. 17, 2023, discovery that school system files had been encrypted by ransomware, officials told the federal law enforcement agency. A day later, Minneapolis schools hired a third-party forensics investigation firm to negotiate the hacker’s demand for $4.5 million in bitcoin.
Yet when school officials notified students and parents, they vaguely described what happened as an “encryption event” and offered a drastically different story than the one in their Feb. 21 report to the FBI. According to records obtained by The 74 through public records requests, the district told families in a Feb. 24 email that its investigation “has found no evidence that personal information was compromised.”
The statement was sent after cybersecurity experts advised district communications staff that “sharing the least amount of information” as possible was “in the best interest” of district security.

Threat actors with the ransomware gang Medusa — known for encrypting and stealing sensitive records from cyberattack victims and then threatening to publish them in what’s known as a “double-extortion” scheme — took credit for the attack. Medusa ultimately published a trove of sensitive school district files online. The leaked documents detail campus sexual misconduct cases, child abuse inquiries, student mental health crises and suspension reports.
Minneapolis school leaders didn’t acknowledge for nearly two weeks after the attack that sensitive records may have been compromised — and waited months to notify breach victims directly by letter.
The district didn’t respond to requests for comment.
As Minneapolis recovered from the attack, records show, it turned first to its insurance provider and cybersecurity lawyers, who were paid as much as $370 an hour to negotiate with the hackers, investigate the breach and keep information about the incident outside of public view.
An insurance company, which held a $1 million liability policy on the district with a $100,000 deductible, was the first point of contact in the event of a cyberattack, according to a school system incident response plan obtained by The 74. The cyber insurance provider will “facilitate breach counsel and forensic investigation teams,” the plan notes, and deploy “experienced negotiators” to communicate directly with the hackers. The policy also states it would cover the district’s liability for bad press, fines and “regulatory proceedings” related to a cyberattack.
“The insurer will typically have an approved panel vendor list for breach counsel, computer forensics and incident response teams,” the plan notes.
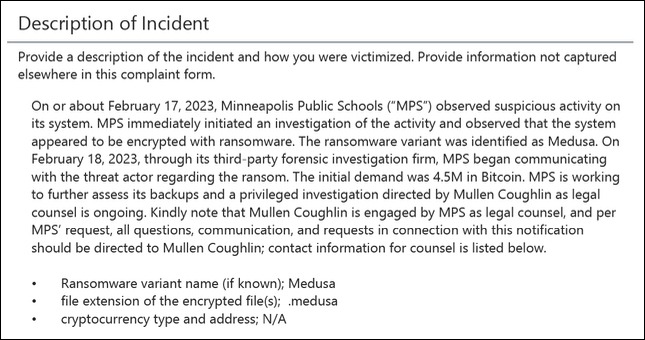
Attorneys with the leading cybersecurity and data privacy law firm Mullen Coughlin were hired to carry out a “privileged investigation,” according to its report to the FBI, with the firm relaying that information about the attack should not be released publicly.
“Per [Minneapolis Public Schools’] request, all questions, communications and requests in connection with this notification should be directed to Mullen Coughlin,” according to the notification to the FBI, which was signed by an associate attorney with the third-party law firm. Mullen Coughlin didn’t respond to The 74’s request for comment.
Forensic investigation work was conducted by the cybersecurity incident response company Tracepoint, a subsidiary of the government and military contractor Booz Allen Hamilton, which Bloomberg News has dubbed “the world’s most profitable spy organization.” The researchers prepared “a report detailing the forensic analysis process and analysis” at Mullen Coughlin’s direction, records show. On March 14, 2023, the researchers held a meeting with district administrators where they went “through the list of what TA [the threat actor] might’ve accessed,” and answered questions.
The data leak had a direct, detrimental impact on breach victims, records show. In an email to the district in March, one educator reported that someone withdrew more than $26,000 from their bank account. Another person got a direct Twitter message from the “Medusa contact team,” urging the person to respond to the threat actors immediately or else “we will ensure your popularity.”

In March, Medusa ransomware actors posted the district’s stolen files online after the school system did not pay what the cybercriminals said on a leak site was a $1 million ransom — a markedly lower figure than the $4.5 million the district reported to the FBI. The breached files, according to an analysis by The 74, include confidential and highly sensitive records about individual students and teachers.
It wasn’t until September 2023 — seven months after the attack — that 105,617 people were notified the “hacking” incident exposed their sensitive information, according to a data breach notice sent to the Maine attorney general’s office. The notice states that the process to identify that information had been completed in July — a month and a half before officials notified victims.
“Although it has been difficult to not share more information with you sooner,” the letter to victims notes, “the accuracy and the integrity of the review were essential.”
As of Dec. 1, 2024, all schools in Minnesota are now required to report cyberattacks to the state but that information will be anonymous and not shared with the public.
Get stories like these delivered straight to your inbox. Sign up for The 74 Newsletter