This article is published in partnership with WIRED
Schools have faced an onslaught of cyberattacks since the pandemic disrupted education nationwide five years ago, yet district leaders across the country have employed a pervasive pattern of obfuscation that leaves the real victims in the dark, an investigation by The 74 shows.
Click text highlighted green to read more about specific hacks.
An in-depth analysis chronicling more than 300 school cyberattacks over the past five years reveals the degree to which school leaders in virtually every state repeatedly provide false assurances to students, parents and staff about the security of their sensitive information. At the same time, consultants and lawyers steer “privileged investigations”, which keep key details hidden from the public.
In more than two dozen cases, educators were forced to backtrack months — and in some cases more than a year — later after telling their communities that sensitive information, which included, in part, special education accommodations, mental health challenges and student sexual misconduct reports, had not been exposed. While many school officials offered evasive storylines, others refused to acknowledge basic details about cyberattacks and their effects on individuals, even after the hackers made student and teacher information public.

The hollowness in schools’ messaging is no coincidence.
That’s because the first people alerted following a school cyberattack are generally not the public nor the police. District incident response plans place insurance companies and their phalanxes of privacy lawyers first. They take over the response, with a focus on limiting schools’ exposure to lawsuits by aggrieved parents or employees.
The attorneys, often employed by just a handful of law firms — dubbed breach mills by one law professor for their massive caseloads — hire the forensic cyber analysts, crisis communicators and ransom negotiators on schools’ behalf, placing the discussions under the shield of attorney-client privilege. Data privacy compliance is a growth industry for these specialized lawyers, who work to control the narrative.
The result: Students, families and district employees whose personal data was published online — from their financial and medical information to traumatic events in young people’s lives — are left clueless about their exposure and risks to identity theft, fraud and other forms of online exploitation. Told sooner, they could have taken steps to protect themselves.
Similarly, the public is often unaware when school officials quietly agree in closed-door meetings to pay the cybergangs’ ransom demands in order to recover their files and unlock their computer systems. Research suggests that the surge in incidents has been fueled, at least in part, by insurers’ willingness to pay. Hackers themselves have stated that when a target carries cyber insurance, ransom payments are “all but guaranteed.”
In 2023, there were 121 ransomware attacks on U.S. K-12 schools and colleges, according to Comparitech, a consumer-focused cybersecurity website whose researchers acknowledge that number is an undercount. An analysis by the cybersecurity company Malwarebytes reported 265 ransomware attacks against the education sector globally in 2023 — a 70% year-over-year surge, making it “the worst ransomware year on record for education.”
Daniel Schwarcz, a University of Minnesota law professor, wrote a 2023 report for the Harvard Journal of Law & Technology criticizing the confidentiality and doublespeak that shroud school cyberattacks as soon as the lawyers — often called breach coaches — arrive on the scene.
“There’s a fine line between misleading and, you know, technically accurate,” Schwarcz told The 74. “What breach coaches try to do is push right up to that line — and sometimes they cross it.”
Kept in the Dark: K-12 Cyberattacks in Focus
The 74 tracked more than 300 K-12 school cyberattack incidents over the last five years, offering an unprecedented look into how education leaders react to hackers’ demands — and how students, parents and teachers are routinely left in the dark.
Use the menu below to read more about how incidents unfolded in your own community.
Gadsden Independent School District
Location: Sunland Park, New Mexico
Breach date: February 2020 and August 2024
When the Gadsden Independent School District in New Mexico fell victim to a ransomware attack in mid-August 2024 — right at the beginning of the school year — it offered the community an assurance.
“We are pleased to report that neither student nor employee data has been compromised during this incident,” the district said in a statement to CBS 4. “Protecting our students’ information remains our top priority.”
The district superintendent told the station that officials were able to react quickly to protect data, a similar response to what it gave after a 2020 attack on the school system. That February — seven months after a ransomware gang disabled its email system — school officials announced it suffered a cyberattack.
School officials couldn’t be reached for comment.
Blaine County School District
Location: Hailey, Idaho
Breach date: November 2023
Info exposed: Employees’ names and Social Security numbers
Threat actors with the BlackSuit ransomware gang claimed a cyberattack on the Hailey, Idaho, school district in November 2023.
The district disclosed the “network security incident” a month later, according to the Idaho Mountain Express. Officials told current and former employees in an email threat actors may have gained access to their names and Social Security numbers. School officials couldn’t be reached for comment.
Danbury Public Schools
Location: Danbury, Connecticut
Breach date: July 2023
Info exposed: Employees’ names, mailing addresses, bank account information and Social Security numbers
Danbury Public Schools appeared on the dark web leak sites of two ransomware groups in the summer of 2023 but the school district did not respond to public records requests that The 74 submitted in mid-July 2023.
However, a month after the district was listed on the dark web, it disclosed a “hacking” incident to the Maine attorney general’s office. In a data breach notice in early August 2023, which was filed by an attorney with the law firm Lewis Brisbois Bisgaard & Smith, Danbury schools notified nearly 10,000 people — just seven of them Maine residents — that their information had been exposed.
The “cybersecurity attack,” a letter to victims noted, exposed victims’ names, mailing addresses, bank account information and Social Security numbers. School officials couldn’t be reached for comment.
Hoosick Falls Central School District
Location: Hoosick Falls, New York
Breach date: August 2023
The Hoosick Falls school district appeared on the 8Base ransomware gang’s leak site in August 2023. The 74 didn’t identify additional Information about the incident and officials couldn’t be reached for comment.
Mars Area School District
Location: Mars, Pennsylvania
Breach date: Between January 2022 and September 2022
Info exposed: Social Security numbers, driver’s licenses, health insurance and banking information and medical records
The Mars school district appeared on the Vice Society ransomware gang’s leak site in October 2022 and the district announced in a statement that it was experiencing a “data security incident” and that certain data “was leaked online as a result” but that they didn’t know for certain what types of records had been exposed.
Transparency came via public disclosure across state lines — through breach notices submitted to state regulators in Montana and Massachusetts.
At least seven months after school officials discovered the attack, the district disclosed in a notice on its website that “a recent security incident” may have exposed personal information, including health records. The April 24, 2023, letter notes the district notified law enforcement officials and hired third-party cybersecurity professionals to investigate the incident, which occurred between Jan. 27 and Sept. 26, 2022. Leaked information included Social Security numbers, driver’s licenses, health insurance and banking information and medical records.
School officials couldn’t be reached for comment.
Clifton Public Schools
Location: Clifton, New Jersey
Breach date: August 2023
The Clifton school district appeared on the Akira ransomware gang’s leak site in August 2023, where the hackers taunted school administrators.
“The leadership of this district has priced their school information too cheaply, which is the reason their internal information is here,” the group wrote on its dark web blog. “As always, 60 GB (gigabytes) of school documents with detailed personal information will be posted here.”
Details about the beach and the district’s response, however, remain unknown. School officials couldn’t be reached for comment.
Edmonds School District
Location: Lynnwood, Washington
Breach date: January 2023
Info exposed: Names, Social Security, driver’s license and passport numbers, financial and health insurance information and medical records
When threat actors with the Akira ransomware gang claimed in August 2023 the Edmonds, Washington, school district had become its latest cyberattack target, the development may have felt to locals like déjà vu.
Just six months earlier, in February 2023, the district announced that a “data event” was to blame for a two-week internet blackout in late January. District spokesperson Harmony Weinberg told The 74 in September 2023 the district was not the target of a second cyberattack and was “aware of a public allegation by the group believed to be responsible for our winter 2023 data security incident.”
On its dark web leak site, threat actors claimed they took 10 gigabytes of data and that the district “seems not to be very interested in saving it.”
“So we are ready to share it with everyone interested,” the group wrote.
The district ultimately notified 145,844 people that hackers stole their personal information, according to regulatory notices submitted in Washington and several other states. Exposed information included names, Social Security numbers, driver’s license numbers, financial information, passport numbers, health insurance information and medical records, according to a notice third-party law firm Mullen Coughlin submitted to the Washington attorney general’s office in January 2024 — a year after the attack.
The district’s investigation ended in September 2023, according to one of three breach notices the district submitted to the Maine attorney general’s office. The January 2024 notice states the additional letters were sent after the district used “the assistance of a third party to locate a mailing address for additional individuals.”
School officials couldn’t be reached for comment.
Renton School District
Location: Renton, Washington
Breach date: August 2023
Info exposed: Names, Social Security numbers, banking information, dates of birth and health insurance and medical information
Threat actors with the ransomware gang Akira listed the Renton school district on their leak site in August 2023, with a threat to leak 200 gigabytes of stolen records, including medical information.
Information about a cyberattack at the district is limited — aside from data breach notices in several states. In a breach notice to the Maine attorney general’s office, the district disclosed that it suffered a “hacking” incident. On Aug. 3, the district “experienced a network disruption” that rendered its systems inoperable due to “a sophisticated cyber-attack.” Nearly seven months later, on Feb. 29, 2024, school officials began informing individual victims that their Social Security numbers had been exposed in the breach.
In a disclosure to the Washington state attorney general’s office, the district acknowledged that 771 state residents had their information stolen, including their names, Social Security numbers, banking information, dates of birth and health insurance and medical information. The total number of affected individuals, according to the disclosure in Maine, was 30,373.
School officials couldn’t be reached for comment.
Van Buren Public Schools
Location: Belleville, Michigan
Breach date: December 2023
When threat actors with the ransomware gang Akira listed the Van Buren district on their leak site in January 2024, the criminals claimed they had the “juiciest information” about students, parents and educators.
The extent of the December 2023 attack remains unknown, yet district officials have sought to frame their response as a success, telling the community during a January 2024 school board meeting that students’ information was secured and that they did not pay a ransom.
School officials couldn’t be reached for comment.
Castilleja School
Location: Palo Alto, California
Breach date: January 2024
The Akira ransomware gang listed the private all-girls Castilleja School in Palo Alto on its leak site in January 2024, claiming it had stolen 10 gigabytes of documents including students’ sensitive information.
In response to an inquiry from The 74, the school’s spokesperson provided a letter it sent to parents about the attack, which notes that it affected files “from College Counseling, Advancement and Food Services as well as some teaching materials.”
In the immediate aftermath, the letter states, officials contacted their insurance provider and hired third-party attorneys to assist. They also reported the attack to the FBI.
“Living in Silicon Valley, we may be especially aware of how common this type of criminal activity is becoming with attacks at companies and other schools,” Acting Head of School Kathy Layendecker wrote in the letter. “At the same time, hearing about attacks is not the same as learning that our own community has been impacted. Please use your discretion and share this with your child as a teachable moment if that feels appropriate for your family.”
School District of Nekoosa
Location: Nekoosa, Wisconsin
Breach date: February 2024
The Akira ransomware gang named the Nekoosa school district on its leak site in February 2024, claiming it had stolen personal information of students and staff, including their addresses, phone numbers “and so on.”
The 74 didn’t identify additional Information about the incident and school officials couldn’t be reached for comment.
Plainedge Public Schools
Location: Massapequa, New York
Breach date: June 2022
Info exposed: Names, phone numbers, email addresses and government IDs
The Alphv ransomware gang listed the Massapequa school district on its leak site in June 2022. A month later, the district disclosed in a notice to the state education department that 99 employees had been affected, according to reporting by Newsday. Officials disclosed that hackers had stolen employees’ names, phone numbers, email addresses and government IDs. School officials couldn’t be reached for comment.
The Walker School
Location: Marietta, Georgia
Breach date: October 2023
Info exposed: Names, addresses and Social Security numbers
The metropolitan Atlanta private school, which was listed on two ransomware gangs’ leak sites in November 2023, disclosed in out-of-state breach notices that it fell victim to a hack.
Officials discovered the hack in November and 1,493 data breach victims were notified later that month, according to a notice filed with the Maine attorney general’s office. The “recent data security incident,” the notice states, exposed people’s names, addresses and Social Security numbers.
A sample letter submitted to the Massachusetts AG’s office appeared to further expose a data breach victim: Unlike the letter submitted in Maine, officials did not redact the individual’s name and Boston address.
School officials couldn’t be reached for comment.
Mooresville Consolidated School Corporation
Location: Mooresville, Indiana
Breach date: May 2022
When threat actors with the BianLian ransomware gang posted the Mooresville school district on its leak site, district officials announced in a statement that they had experienced “a computer network disruption.”
The group claimed it stole the records of more than 4,000 students, according to the Reporter-Times, including phone numbers, email addresses and Social Security numbers.
Though limited public information about the incident exists, a spreadsheet on the Indiana Attorney General’s Office website notes the district sent data breach notices to affected individuals in mid-October, some five months after the incident occurred. In total, 417 individuals were affected by the breach, according to the disclosure report.
School officials couldn’t be reached for comment.
Vanoss Public Schools
Location: Ada, Oklahoma
Breach date: November 2022
Threat actors with the BianLian ransomware gang listed the Ada school district on its leak site in November 2022. The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Deer Lakes School District
Location: Cheswick, Pennsylvania
Breach date: May 2023
Threat actors with the BianLian ransomware gang listed the Cheswick school district on its leak site in May 2023, three months after school leaders announced it had fallen victim to a “cyber incident.”
Though the extent of the hack and a potential data breach remain unclear, the district spent $2,400 on “threat actor communications” between March and May 2023, according to data collected by the government procurement database GovSpend. The expenditure suggests the district hired consultants to negotiate with hackers.
School officials couldn’t be reached for comment.
Henry County Schools
Location: McDonough, Georgia
Breach date: November 2023
School district officials disclosed they spent more than $700,000 to recover from a November 2023 ransomware attack carried out by “a group of criminals operating outside of the United States.”
The district appeared on the BlackSuit ransomware gang’s leak site in December, and although the incident disrupted the district’s computer network for more than a month, the superintendent said that students’ information was not compromised.
School officials couldn’t be reached for comment.
Kershaw County School District
Location: Camden, South Carolina
Breach date: January 2024
The Kershaw County School District was listed on the BlackSuit ransomware gang’s leak site in January 2024, when threat actors claimed they had stolen 17.5 gigabytes of sensitive district files.
The 74 didn’t identify additional information about the incident. School officials couldn’t be reached for comment.
Groveport Madison Schools
Location: Groveport, Ohio
Breach date: December 2023
In the first week of December 2023, the Groveport school district was hit with a cyberattack that prompted weeklong internet outages that, according to The Columbus Dispatch, forced educators to teach students “the old-fashioned way, with books and paper.”
The ransomware gang BlackSuit, which claimed the district as a victim on its leak site, hacked into the security cameras and printers at its only high school, a district spokesperson told the newspaper. The threat actor contacted teachers directly and alerted them to vulnerabilities in the district’s computer firewall. The spokesperson said district leaders reported the incident to federal law enforcement.
The extent to which sensitive data were exposed in the breach remains unknown. Officials declined to comment.
South St. Paul Public Schools
Location: South St. Paul, Minnesota
Breach date: March 2024
Threat actors with the BlackSuit ransomware group posted the South St. Paul school district on their leak site in March 2024, though the extent to which any sensitive information was disclosed remains unknown.
That same month, district officials announced to parents and staff that technical difficulties “may disrupt certain services,” due to “unauthorized activity within our computer network.”
Officials told the public they “engaged a third-party cybersecurity firm to assist us with systems recovery and investigate the cause and scope of the unauthorized activity.”
School officials couldn’t be reached for comment.
St. Paul Public Schools
Location: St. Paul, Minnesota
Breach date: February 2023
Info exposed: Student names, email addresses
The St. Paul school district fell victim in a “data security incident” in February, 2023, the district announced in September — more than half a year after the hack exposed the names and email addresses of 43,727 students.
No other information was exposed in the breach, a district spokesperson told the Twin Cities Pioneer Press.
In response to an inquiry from The 74, a district spokesperson said the district “has further strengthened its cybersecurity measures and has not experienced any subsequent incidents or data breaches” since the attack.
School officials couldn’t be reached for comment.
Chambersburg Area School District
Location: Chambersburg, Pennsylvania
Breach date: August 2023
Info exposed: Special education records and Social Security numbers
After an August 2023 ransomware attack forced the Chambersburg school district to close for three days, district parents were upset.
Not only were campuses shuttered less than a week into the new academic year, parents said that school officials had kept them in the dark about what they called “temporary network disruptions” — including whether students’ sensitive information had fallen into the hands of criminals.
A student portal that school administrators instructed families not to use, one parent said during an August school board meeting, contained childrens’ names, home addresses and photographs.
“It could be pedophiles getting our address,” the parent said, according to ABC 27. “They know what they look like. Every single student has their picture on this.”
On Aug. 31, the district acknowledged the disruptions were the result of a “ransomware event,” but maintained that it couldn’t disclose information whether it paid off the hackers or the type of records that had been leaked. Chambersburg appeared on the ransomware gang BlackByte’s dark web leak site in September.
In a Q&A on the district’s website, then-acting Superintendent Larry Redding said they hired data privacy attorneys from the firm Mullen Coughlin and that lawyers advised them against discussing potential ransom payments “to protect the integrity of the various ongoing investigations.”
In October, two months after the attack, the district disclosed on its website that a third-party forensics team had completed a “legally privileged investigation” into the attack and although Chambersburg successfully defended itself “against demands from the threat actors,” they made off with sensitive data before officials “discovered and contained this event.”
“During the first days of the cyber-attack, we notified our school insurance personnel and immediately began to strictly adhere to their expert guidance to ensure compliance with both legal and procedural requirements,” Redding wrote in the statement.
He then addressed parents’ unhappiness head-on:
“While many people were frustrated by the lack of information for public consumption, during all phases of the process we worked with our legal counsel and specialist vendors to obtain accurate and thorough information that would allow us to best inform the community,” he wrote, adding that affected parties would soon receive breach notices. “School district employees from 2008 to the current year and a very small group of students with individualized educational plans are those groups most likely affected.”
Though the district is located in Pennsylvania, the most comprehensive disclosure about the data breach is available from an out-of-state entity: the Maine attorney general’s office. The district reported that an “unknown actor” had gained access to the sensitive information of 4,265 people, including employees’ Social Security numbers.
“Certain current and former students may have been impacted by this event,” the district wrote in the disclosure letter.
In response to an inquiry from The 74, current Superintendent Chris Bigger said cyberattacks that lead to state and federal investigations “make it challenging to navigate public sharing.”
“The authorities decide when and how to communicate during the event/incident,” Bigger wrote in an email. The schools chief, who took over as superintendent about three months after the attack, said he was impressed by how quickly Chambersburg was able to recover thanks to system backups.
“Schools are asked to allocate more resources to issues outside the classroom each and every year making it difficult to maintain our focus on teachers and the students,” Bigger said. “I believe much more needs to be done to the bad actors who work tirelessly to do bad things and disrupt our precious schools.”
Montour School District
Location: Mckees Rocks, Pennsylvania
Breach date: August 2022
The Montour School District in suburban Pittsburgh was listed on the Hive ransomware gang’s leak site in August 2022, right as kids returned to campus for a new academic year. The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Mansfield Independent School District
Location: Mansfield, Texas
Breach date: January 2022
Info exposed: Student and staff names, addresses, Social Security numbers and state-issued IDs. Also affected were staff banking and health insurance information, driver’s license numbers and medical records
After the Hive ransomware gang posted the Mansfield district on its dark web leak site in October 2022, the district sent out a warning to students, parents and educators: Don’t engage with criminals.
Members of the community, the district disclosed in a statement, were getting emails from an “unauthorized actor” claiming they had obtained sensitive data from the school district’s servers in the wake of a hacking incident that exposed the personal information of nearly 130,000 people.
“Do not respond to these communications or any other attempted outreach by the unauthorized actor,” the district wrote. “These are criminals, and any response is likely to lead to additional harassment and/or attention from the unauthorized actor.”
In a breach notice on the district website, officials said they became aware of “irregular activity within our computer network” in August 2022, and concluded an investigation into the matter a month later. The district hired attorneys with the firm Mullen Coughlin, according to procurement data collected by the firm GovSpend, and sent notices to victims informing them their information had been stolen.
Sensitive data exposed in the breach included student and staff names, addresses, Social Security numbers and state-issued IDs. Also affected were staff banking and health insurance information, driver’s license numbers and medical records.
The extent of the hack was disclosed in a breach notice to the Maine attorney general’s office, which revealed that officials had discovered the incident nine months after the hackers had infiltrated the district’s systems.
The January 12, 2022, breach, the district disclosed, affected 129,593 people including seven Maine residents. In its notice to victims, officials acknowledged that an investigation into the “irregular activity” determined they had become the victim of a ransomware attack.
School officials couldn’t be reached for comment.
Norman Public Schools
Location: Norman, Oklahoma
Breach date: November 2022
Info exposed: Driver’s license numbers, Social Security numbers and student records
After the Hive ransomware gang posted the Norman school district on its leak site in November 2022, local media outlets were put on notice.
In an email to local press, threat actors claimed they stole reams of sensitive information, including Social Security numbers, emails, home addresses, phone numbers and insurance records.
In a statement that was posted to the district website but has since been removed, Norman school officials acknowledged that Social Security numbers may have been compromised.
Several months later, in January 2023, the district confirmed that individuals’ personal information had been compromised, including staff members’ driver’s license numbers and “certain information related to current and former students.”
A comprehensive rundown of the types of records that were stolen, however, was never disclosed publicly.
“NPS is placing notations in the electronic records in Infinite Campus for potentially impacted students,” the district wrote in a statement referring to using its digital student information management system to notify potential victims. “Those notations will describe the type of information that was potentially viewed or taken.”
The district’s most recent statement in March 2023 says it was offering identity theft protection services as a result of the “malicious ransomware attack.”
School officials couldn’t be reached for comment.
Gallup-McKinley County Schools
Location: Gallup, New Mexico
Breach date: April 2023
When hackers targeted the Gallup-McKinley school district, its IT department was understaffed.
That’s according to a case study by the cybersecurity company Malwarebytes, which noted there were “only five technicians, one network engineer and one network administrator to manage all of the endpoints” of the more than 12,000-student school district.
Still, the report notes, Gallup-McKinley successfully defended itself against a ransomware attack.
Public records reveal the district never notified the public about the attack, even after threat actors with the Hunters ransomware gang listed the school system on its leak site in January 2024.
Public records obtained by The 74 reveal the district suffered a ransomware attack in April 2023 — and that district officials responded swiftly to keep the event out of public view.
Early that month, emails reveal Gallup-McKinley began working with its insurance provider, cybersecurity consultants and a third-party law firm to investigate the attack and identify its legal obligation to notify victims.
The documents disclose that the district faced business pressures to select the vendors that insurers preferred. In an email, Jo Anne Roque, the vice president of risk services account management at Poms & Associates Insurance Brokers, recommended “working with the carriers preferred vendors that will increase the limit of breach services available.”
“The final decision is up to the District on selecting privacy counsel and while Beazley highly recommends BakerHostetler due to their expertise in this area, an alternative counsel on the carrier panelist is available,” Roque wrote. “However, if a firm is selected outside of the carrier network, the amount of services would be reduced from $1M to $500,000.”
Contracting a privacy attorney was necessary, Roque wrote, to shield from public view any findings by the company Kroll, which conducts forensic investigations and intelligence gathering.
“Without privacy counsel in place, public records would be accessible in the event of an information leak,” she noted. She added that these lawyers specialize in state reporting laws, provide public relations assistance and defense against potential lawsuits.
In an April 13 email, Roque told district IT director Bart Stanley the school system was “in good hands” receiving investigative services from Kroll and legal assistance from lawyers at the firm BakerHostetler.
Under New Mexico’s Inspection of Public Records Act, The 74 sought all district notifications to students, parents, state regulators — and law enforcement — about the attack. Gallup-McKinley responded that “no documents exist.” School officials couldn’t be reached for comment.
Cleveland City Schools
Location: Cleveland, Tennessee
Breach date: August 2023
Info Exposed: Students’ names, birth dates, ethnicities and academic performance
The Cleveland City school district announced in an August 2023 news release that “less than 5% of all devices connected to (its) network” had been affected in a ransomware attack. There was “no indication of any compromise” of personal information, the district assured at the time, adding that it was working with federal law enforcement to investigate.
Two months later, in October 2023, threat actors with the group Inc Ransom posted the Tennessee district to their leak site. A review by The 74 identified leaked records that included in-depth information about students, including their names, birth dates, ethnicities and academic performance. A separate folder contained pictures of elementary-aged children in caps and gowns.
School officials couldn’t be reached for comment.
Decatur Independent School District
Location: Decatur, Texas
Breach Date: September 2023
Info exposed: Names, Social Security numbers and banking information
The Decatur school district acknowledged in September 2023 that a cyberattack led to district internet disruptions — but maintained that the “cybersecurity incident” did not involve sensitive records.
“At this time, we have no evidence that any data has been accessed, acquired or misused,” the district communications director said in a statement to the Wise County Messenger.
Threat actors with the group Inc Ransom took credit for the attack, posting Decatur Independent to its leak site in November 2023. It was four months after the leak — and six months after its initial assurances — that the district sent letters to victims notifying them that their information had, in fact, been stolen by an “unknown actor.”
A review of the breached files by The 74 uncovered records with Social Security numbers and individuals’ banking information. School officials couldn’t be reached for comment.
Waterford Country School
Location: Quaker Hill, Connecticut
Breach date: September or October 2023
Info exposed: Names, addresses, birth dates, driver’s license, government and student IDs, Social Security numbers and financial account, health insurance and medical information.
In an August 2024 notice, the Waterford Country School, a private boarding school which serves some 65 children with disabilities, disclosed on its website that a “ransomware incident” had exposed students’ sensitive information — nearly a year earlier.
The notice says the cyberattack, which occurred in September or October 2023, leaked names, addresses, birth dates, driver’s license and Social Security numbers, medical information and other sensitive records.
While data breach victims like students and educators are generally offered credit monitoring services in the wake of a ransomware attack on a school, it is unclear whether the tool was offered at Waterford. The notice advises the school community to “remain vigilant.”
“Waterford Country School understand [sic] the inconvenience or concern this incident may cause [sic] is committed to ensuring the security of all information in its control and has taken steps to strengthen its security posture,” the letter noted.
The school appeared on the dark web leak site for threat actors with Inc Ransom in January 2024, more than a half a year before education officials acknowledged sensitive information had been exposed.
School officials couldn’t be reached for comment.
Orange Public Schools
Location: Orange, New Jersey
Breach date: February 2024
Info exposed: Special education records, birth certificates, medical information, passports and driver’s licenses
Threat actors with the group Inc Ransom claimed responsibility for an attack on the Orange public schools, posting the district to its leak site on Valentine’s Day 2024.
An analysis by The 74 of the site suggests the breach exposed a massive volume of sensitive information about students, including comprehensive special education records, birth certificates, medical information, passports and other sensitive files.
One record viewed by The 74 included a father’s passport, a mother’s driver’s license, a mortgage statement and a shut-off notice from a utility company. School officials couldn’t be reached for comment.
Delano Union School District
Location: Delano, California
Breach Date: November 2021
Info breached: Names, Social Security numbers
The Delano Union School District in California suffered a “data security incident” in November 2021, according to a breach notice filed with the California Attorney General’s office in May 2023 — a year and a half later.
Though the notice indicates that staff “detected unusual activity within its digital environment” and that an investigation determined sensitive data “may have been accessed or acquired by an unknown actor,” it doesn’t disclose that a cyberattack had occurred. It does note, however, that “certain personal information may have been involved in this incident,” including names and Social Security numbers.
In November 2021, the same month as the “data security incident,” the district spent $157,000 on “cybersecurity consulting services” from Coveware, a cybersecurity company that specializes in negotiating with hackers and paying ransoms.
A Nov. 8, 2021, report to the FBI, obtained by The 74 through a public records request, disclosed that the district fell victim to a cyberattack by the Pysa ransomware gang. An attorney declined to disclose records related to the district’s interactions with Coveware, citing attorney-client privilege. School officials couldn’t be reached for comment.
Delano Joint Union High School District
Location: Delano, California
Breach date: April 2024
Info exposed: Names, addresses, tax records, immunization records and injury reports
Threat actors with the Inc Ransom cybergang took credit in April 2024 for a cyberattack on the Delano Joint Union High School District in California.
An analysis by The 74 of Inc Ransom’s leak site revealed the breach included reams of sensitive information from Delano, including names, addresses, tax records, students’ immunization records, and injury reports. In a 2023 suspected child abuse report, a school principal reported to the police that an instructional aide hit a student. Other breached reports include students’ in-depth psychological evaluations.
In response to a public records request by The 74, the district provided an April 2024 email from the California Cyber Security Integration Center notifying school officials of “a potential ransomware attempt against” the district.
An attorney working for the district told The 74 there were no records notifying the public about the incident. School officials couldn’t be reached for comment.
Rockford Public Schools
Location: Rockford, Michigan
Breach date: May 2024
Info breached: Names, birth dates, addresses, passports, driver’s licenses and student disciplinary records
Something peculiar alerted Rockford, Michigan, school district officials that they had become the targets of a ransomware attack.
In May 2024, the school system was presented with “random messages that popped up on some printers throughout the district,” the superintendent told Fox 17.
“Your data is stolen and encrypted,” the ransom note read. “If you don’t pay the ransom, the data will be published on our TOR darknet sites. The sooner you pay the ransom, the sooner your company will be safe.”
The superintendent told the local press they notified the FBI and hired consultants to investigate the incident. Although they were still investigating a potential data breach, the educator said the compromise was likely limited in size since just a few printers received the ransom note.
A month later, in June 2024, Inc Ransom threat actors took credit for the attack, listing the school system on its dark web leak site and countering the district’s claims.
“We have more than 1.5 TB (terabytes) of data in our hands,” they claimed, including student data, passports “and much, much more.”
An analysis by The 74 of the threat actor’s leak site indicates the hack exposed reams of sensitive information, including students’ names, birth dates and contact information. Security reports offer narrative descriptions of student disciplinary incidents, including one where two students were suspended for 10 days after they got caught getting drunk inside a campus building during a high school football game.
Another outlined a mother’s complaint that her son was getting bullied at school and a third involved a fistfight between two girls.
School officials couldn’t be reached for comment.
San Benito Consolidated Independent School District
Location: San Benito, Texas
Breach Date: November 2022
Threat actors with the Karakurt ransomware gang claimed in November 2022 a cyberattack on the San Benito, Texas, school district prompting school officials to send breach notices to 21,653 victims two months later.
On the dark web, threat actors claimed they had stolen 180 gigabytes of data including “lots of student info,” but it wasn’t until the middle of winter break — on Dec. 30 — that employees and students were mailed breach notices. Of the victims, 12,080 were students, according to the Valley Morning Star.
The news outlet reported on victims who had spoken out about the district’s delayed response. In some cases, notices were mailed to victims’ previous addresses.
“People are complaining they weren’t notified on time,” said Ida Rodriguez, a retired assistant principal. “Someone really dropped the ball. What a mess.”
School officials couldn’t be reached for comment.
River City Science Academy
Location: Jacksonville, Florida
Breach date: January 2023
The River City Science Academy, a charter school in Jacksonville, Florida, became the target of a Karakurt ransomware attack in January 2023.
That month, the cybergang listed the school on its leak site, where it claimed to have access to 63 gigabytes of data including financial records and personal information about students.
In response to an inquiry from The 74, officials said the school “acted promptly to assess and mitigate risks, always prioritizing the safety and privacy of our students, families and employees.”
“Our approach included close coordination with cybersecurity experts, legal counsel, and relevant authorities including law enforcement to ensure we responded in a manner that fully complies with state and federal regulations,” according to their statement.
York County School of Technology
Location: York, Pennsylvania
Breach date: April 2023
Info exposed: Names, birth dates, health records and Social Security and driver’s license numbers
The York County School of Technology acknowledged in a statement on its website, which is no longer publicly available, that it was the victim of a “data security incident” in April 2023 that led to the exposure of sensitive information.
Officials notified victims in April 2024, a year after the incident occurred. Meanwhile, the cybergang Karakurt took credit for the attack in May 2023, claiming to have stolen 368 gigabytes of data, including driver’s licenses, Social Security numbers and financial records.
In its breach notice, the district acknowledged that “a limited amount of information” may have been accessed, including health records, birth dates and Social Security and driver’s license numbers. Although the notice online states that the records were “acquired by an unauthorized individual,” it didn’t disclose the records were acquired as a result of a cyberattack.
A data breach notice filed with the Maine attorney general’s office, however, offers clarity. The letter, filed by attorneys with the firm McDonald Hopkins, states a “hacking” incident had exposed the records of 30,914 people, including just one Maine resident.
School officials couldn’t be reached for comment.
Eastside Union School District
Location: Lancaster, California
Breach date: May 2023
Info exposed: Names, birth dates, Social Security numbers
Ten months after the Lancaster, California school district fell victim to a cyberattack, it informed thousands of people their information had been exposed.
The incident unfolded in May 2023, according to a data breach notice that the district uploaded to its website and that was provided to the California attorney general’s office.
A month later, in June 2023, threat actors with the Karakurt gang posted the district to its dark web leak site, claiming they stole 18 gigabytes of records that included personal information “and so on.”
The incident was also reported to the Maine attorney general’s office where school officials notified 3,592 people — just one of them a Maine resident — that their information had been compromised in a “hacking” incident, including their names, birth dates and Social Security numbers. Those notices were not sent out until March 2024.
School officials couldn’t be reached for comment.
White Settlement Independent School District
Location: White Settlement, Texas
Breach Date: February 2023
Info exposed: Passport, employees’ personal information
On two separate occasions — in February and June 2023 — threat actors with the LockBit ransomware group claimed attacks on the White Settlement, Texas, school district.
A review of the LockBit leak site by DataBreaches.Net, a blog that tracks and reports on data breaches globally, suggests that hackers were able to access records dating back nearly a decade, including a passport and files with employees’ personal information.
The district sent a statement to the school community, and shared it with DataBreaches.Net, stating that school officials were “recently informed by Homeland Security that the district experienced a possible cyberattack.”
“The district discovered that the only compromised documents belonged to some staff members and were housed in a shared folder,” the statement continued.
School officials couldn’t be reached for comment.
The Christian School Association of Greater Harrisburg
Location: Harrisburg, Pennsylvania
Breach Date: May 2023
The Christian School Association of Greater Harrisburg, a network of K-12 schools, was listed on the LockBit ransomware gang’s leak site in May 2023.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Pittsburg Unified School District
Location: Pittsburg, California
Breach date: June 2023
Threat actors with the LockBit ransomware gang listed the Pittsburg, California, school district on its dark web leak site in June 2023 — years after district officials disclosed an attack but reported that sensitive information was never exposed.
In a January 2020 Facebook post, the school district superintendent announced a cyberattack had shut off the internet, requiring “teaching and learning like ‘back in the day’” without laptops. The district hired specialized attorneys, it announced, but had not yet identified a breach of sensitive records.
The district did not report a data breach to the California attorney general’s office, according to state records. School officials couldn’t be reached for comment.
Point Pleasant Borough School District
Location: Point Pleasant, New Jersey
Breach Date: August 2023
Threat actors with the LockBit ransomware gang listed the Point Pleasant, New Jersey, school district on its dark web leak site in August 2023.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
University Prep
Location: Denver, Colorado
Breach date: August 2023
The University Prep charter school network in Denver was listed on the LockBit ransomware gang’s dark web leak site in August 2023.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Hillsborough County Public Schools
Location: Tampa, Florida
Breach Date: September 2023
Info exposed: Names, birth dates, Social Security numbers and school nurse visit records
The Tampa, Florida, school district experienced network disruptions for several days during a September 2023 cyberattack that school officials acknowledged leaked students’ sensitive information.
On Sept. 22, the district sent breach notices to more than 250 students, notifying them that hackers gained access to their names, birth dates, Social Security numbers and school nurse visit records.
When district officials first notified the public about the breach on Sept. 5, they said external cybersecurity professionals had been hired to conduct an investigation and that they had “no indication that there was any unauthorized access to data stored in our student information system.”
On Sept. 15, the district — the nation’s eighth largest — made an appearance on the LockBit ransomware gang’s leak site.
In response to an inquiry from The 74, the district said in a statement it took “immediate response measures after learning of the cybersecurity incident,” including a notice to law enforcement. It also commissioned third-party cybersecurity consultants “to support work to investigate and restore full operation of our affected devices.”
Student breach victims were notified “by email, mail and a telephone call,” according to the statement, and “we set up a special hotline for affected families to answer questions.”
Faith Family Academy – Oak Cliff
Location: Dallas, Texas
Breach Date: September 2023
Oak Cliff Faith Family Academy, a private school in Dallas, was listed on the LockBit ransomware gang’s dark web leak site in September 2023.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Fauquier County Public Schools
Location: Warrenton, Virginia
Breach Date: September 2023
Info exposed: Names, medical and financial information, Social Security numbers and driver’s licenses
When Warrenton, Virginia, school officials first acknowledged that Fauquier County Public Schools was the victim of a ransomware attack, they offered the public an assurance.
The district acknowledged in October 2023 that it had been the target of a cyberattack in September but said its impact was minimal. That same month, Fauquier County Public Schools
appeared on the LockBit ransomware gang’s leak site.
“At this time, we do not believe that any personal student or staff information has been compromised,” a district spokesperson told Fauquier Now, a local news outlet. “However, law enforcement agencies are continuing their investigation.”
The district declined to comment on whether it paid a ransom or on the extent of a potential data breach, citing the active investigation.
Third-party attorneys hired by the district offered a different story — in Maine. In a mid-October breach notice with the Maine attorney general’s office, the district acknowledged a ransomware attack exposed the sensitive information of 13,919 people, including two Maine residents. Breached records “used to facilitate a safe and effective learning environment” included names, Social Security numbers, driver’s licenses and medical and financial information.
School officials couldn’t be reached for comment.
Foley Public Schools
Location: Foley, Minnesota
Breach Date: November 2023
Foley Public Schools in Minnesota was listed on the LockBit ransomware gang’s dark web leak site in November 2023.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Milton Town School District
Location: Milton, Vermont
Breach Date: December 2023
Info exposed: Social Security numbers, driver’s licenses and financial records
In December, 2023, threat actors with the LockBit ransomware group claimed a cyberattack on the Milton, Vermont school district — an incident that school officials disclosed to state regulators two months later.
In the attack’s immediate aftermath, the district announced that it was collaborating with its insurance provider and federal law enforcement to investigate the breach. School officials said in a press release that students’ information was unaffected.
In February 2024, Milton schools submitted a breach notice to the Vermont attorney general’s office, notifying an unknown number of victims that “an unauthorized party” had access to their sensitive information, including Social Security numbers, driver’s licenses and financial information. School officials couldn’t be reached for comment.
Groton Public Schools
Location: Groton, Connecticut
Breach Date: February 2024
Info exposed: Social Security numbers
After internet outages affected the Groton, Connecticut, school district in February 2024, officials responded quickly, announcing they were hit by a “cyber-attack” and had already “identified where the attack came from and have 90% of our systems operational.”
That same month, threat actors with the LockBit ransomware gang claimed the district as a victim on its dark web leak site.
A data breach notice filed a month later — in Maine — by attorney Dominic Paluzzi of the firm McDonald Hopkins, made clear the attack’s impact on the school community, leading to the exposure of an unknown number of Social Security numbers.
A March 29 letter to breach victims included in the notice to the Maine AG’s office described the attack as a “data security incident” that may — or may not — have included “their sensitive information.”
“The investigation was not able to confirm with one hundred percent certainty your personal information was involved,” the letter states. “As a result, we are proactively notifying you and all current employees out of an abundance of caution.” School officials couldn’t be reached for comment.
D’Hanis Independent School District
Location D’Hanis, Texas
Breach date: March 2024
Threat actors with the LockBit ransomware gang claimed on its dark web leak site a March 2024 attack on the D’Hanis, Texas, school district.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
The Colonial School District
Location: Plymouth Meeting, Pennsylvania
Breach Date: May 2024
Threat actors with the LockBit ransomware gang claimed on its dark web leak site a May 2024 attack on the Plymouth Meeting school district.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Eden Valley-Watkins School District
Location: Eden Valley, Minnesota
Breach Date: May 2024
Threat actors with the LockBit ransomware gang claimed on its dark web leak site a May 2024 attack on the Eden Valley school district.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Hesperia Unified School District
Location: Hesperia, California
Breach Date: May 2024
Info exposed: Names, driver’s license and Social Security numbers, health insurance records and medical information
The Hesperia, California, school district fell victim to a LockBit ransomware attack in May 2024, which officials told victims was a “security incident” that “may have involved some of your information.”
The district disclosed the incident to the California attorney general’s office in June 2024, more than a month after the attack was first discovered. In a letter to an unknown number of victims, officials disclosed that accessed files included names, driver’s license and Social Security numbers, health insurance records and medical information.
School officials couldn’t be reached for comment.
Pueblo County School District
Location: Pueblo, Colorado
Breach date: April 2024
Info exposed: Student and staff records from 1991-2006
Threat actors with the LockBit ransomware gang claimed on its dark web leak site a May 2024 attack on the Pueblo, Colorado, school district.
Two months later, in July 2024, district officials announced in a news release a ransomware attack that may have compromised the information of former students — dating back more than two decades.
The district acknowledged the cybersecurity company Sophos had alerted it to the attack in April — and that its notice to the public was slow, according to The Pueblo Chieftain.
“I realize that the putting out of this information seems like it’s a little bit late, but we weren’t allowed to get this information out,” the superintendent said during a June press conference. Because federal authorities were assisting them, “it wasn’t something that we could have just immediately released.”
School officials couldn’t be reached for comment.
Englewood Public School District
Location: Englewood, New Jersey
Breach date: May 2024
Threat actors with the LockBit ransomware gang claimed on its dark web leak site a May 2024 attack on the Englewood, New Jersey, school district.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Ewing Marion Kauffman School
Location: Kansas City, Missouri
Breach date: May 2024
Info exposed: Social Security numbers
Threat actors with the LockBit ransomware gang claimed on its dark web leak site a May 2024 attack on the Ewing Marion Kauffman School in Kansas City, Missouri.
The charter school acknowledged that month that it was the target of a cyberattack, telling local reporters that officials with a third-party cybersecurity firm were investigating the extent of the breach.
The incident led to a data breach, according to a notice filed with the Massachusetts consumer affairs office that same month, which discloses that hackers had gained access to Social Security numbers.
School officials couldn’t be reached for comment.
Marlboro Township School District
Location: Marlboro, New Jersey
Breach date: September 2023
Threat actors with the LostTrust ransomware gang claimed on its dark web leak site a September 2023 attack on the Marlboro, New Jersey, school district.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Immanuel Christian School
Location: Springfield, Virginia
Breach date: September 2023
Threat actors with the LostTrust ransomware gang claimed on its dark web leak site a September 2023 attack on the Immanuel Christian School. Former Vice President Mike Pence’s wife Karen taught at the private religious school in Springfield, Virginia.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Morgan County School District
Location: Fort Morgan, Colorado
Breach date: December 2022
The Fort Morgan, Colorado, school district was forced to cancel classes for a day in December 2022, with officials disclosing on Facebook that a cybersecurity incident had caused the disruption. School officials couldn’t be reached for comment.
Merced City School District
Location: Merced City, California
Breach date: September 2023
Threat actors with the LostTrust ransomware gang claimed in September 2023 a ransomware attack on the Merced City School District, posting it on its dark web leak site.
Three months later, the district sent breach notices to victims, noting in a December 2023 letter that it “became aware of suspicious activity in our computer network” in late November. The threat actor “downloaded certain information” from the district, but a letter shared with the California attorney general’s office didn’t disclose what specific records had been stolen.
School officials couldn’t be reached for comment.
Minneapolis Public Schools
Location: Minneapolis, Minnesota
Breach date: February 2023
Info exposed: Names, addresses, Social Security numbers, medical information, special education records, disciplinary records
Four days after an attack by a notorious ransomware gang disrupted the Minneapolis, Minnesota, school district’s computer network, accessing reams of students’ and educators’ sensitive information online, officials contacted the FBI and laid out what happened.
The district “immediately initiated an investigation” after its Feb. 17 discovery that school system files had been encrypted by ransomware, officials told the federal law enforcement agency. A day later, Minneapolis schools hired a third-party forensics investigation firm to negotiate the hacker’s demand for $4.5 million in bitcoin.
Yet when school officials notified students and parents, they vaguely described what happened as an “encryption event” and offered a drastically different story than the one in their Feb. 21 report to the FBI. According to records obtained by The 74 through public records requests, the district told families in a Feb. 24 email that its investigation “has found no evidence that personal information was compromised.” The statement was sent after cybersecurity experts advised district communications staff that “sharing the least amount of information” as possible was “in the best interest” of district security.
Threat actors with the ransomware gang Medusa — known for stealing sensitive records from cyberattack victims and using them as leverage in a brazen “double-extortion” scheme — took credit for the attack and, ultimately, published a trove of sensitive school district files online. Minneapolis school leaders didn’t acknowledge for nearly two weeks after the attack that sensitive records may have been compromised — and waited months to notify breach victims directly by letter.
The district didn’t respond to requests from The 74 for comment.
As Minneapolis recovered from the attack, records show, it turned first to its insurance provider and cybersecurity lawyers, who were paid as much as $370 an hour to negotiate with the hackers, investigate the breach and keep information about the incident outside of public view.
An insurance company, which held a $1 million liability policy on the district with a $100,000 deductible, was the first point of contact in the event of a cyberattack, according to a school system incident response plan obtained by The 74. The cyber insurance provider will “facilitate breach counsel and forensic investigation teams,” the plan notes, and deploy “experienced negotiators” to communicate directly with the hackers. The policy also states it would cover the district’s liability for bad press, fines and “regulatory proceedings” related to a cyberattack.
“The insurer will typically have an approved panel vendor list for breach counsel, computer forensics and incident response teams,” the plan notes.
Attorneys with the leading cybersecurity and data privacy law firm Mullen Coughlin were hired to carry out a “privileged investigation,” according to its report to the FBI, with the firm requesting that information about the attack not be released publicly.
“Per MPS’ request, all questions, communications and requests in connection with this notification should be directed to Mullen Coughlin,” according to the notification to the FBI, which was signed by an associate attorney with the third-party law firm.
Forensic investigation work was conducted by the cybersecurity incident response company Tracepoint, a subsidiary of the government and military contractor Booz Allen Hamilton, which Bloomberg News has dubbed “the world’s most profitable spy organization.” The researchers prepared “a report detailing the forensic analysis process and analysis” at Mullen Coughlin’s direction, records show. On March 14, 2023, the researchers held a meeting with district administrators where they went “through the list of what TA [the threat actor] might’ve accessed,” and answered questions.
The data leak had a direct, detrimental impact on breach victims, records show. In an email to the district in March, one educator reported that someone withdrew more than $26,000 from their bank account. Another person got a direct Twitter message from the “Medusa contact team,” urging the person to respond to the threat actors immediately or else “we will ensure your popularity.”
In March, Medusa ransomware actors posted the district’s stolen files online after the school system did not pay what the cybercriminals said on a leak site was a $1 million ransom — a markedly lower figure than the $4.5 million the district reported to the FBI. Breached files, according to an analysis by The 74, included confidential and highly sensitive records about individual students and teachers, including those outlining campus rape cases, child abuse inquires, student mental health crises and suspension reports.
It wasn’t until September 2023 — seven months after the attack — that 105,617 people were notified the “hacking” incident exposed their sensitive information, according to a data breach notice sent to the Maine attorney general’s office. The notice states that the review to identify sensitive information had been completed in July — a month and a half before officials notified victims.
“Although it has been difficult to not share more information with you sooner,” the letter to victims notes, “the accuracy and the integrity of the review were essential.”
As of Dec. 1, all schools in Minnesota are now required to report cyberattacks to the state but that information will be anonymous and not shared with the public.
Uniondale Union Free School District
Location: Uniondale, New York
Breach date: April 2023
Info exposed: Student and employee email addresses, home addresses and phone numbers
Threat actors with the Medusa ransomware gang claimed an attack on the Uniondale, New York, school district, listing the school system on its leak site in April 2023.
In a letter that month on the district website, officials announced “a potential breach” that was “most likely the dark web cybercrime group known as Medusa.”
“Over the past several months, this group has claimed responsibility for cyberattacks against multiple public school districts across the country, demanding ransom for the return of stolen data,” the superintendent wrote.
The affected data likely included student and employee email addresses, home addresses and phone numbers — information that Medusa posted on the dark web as evidence that they leveled a successful attack on Uniondale schools, the letter states. The superintendent goes on to offer an assurance: “More sensitive student data, as well as district financial information, which are housed on third-party servers, do not appear to be at risk.”
School officials couldn’t be reached for comment.
St. Landry Parish School Board
Location: Opelousas, Louisiana
Breach date: July 2023
Info exposed: Names, addresses, contact information, Social Security numbers, special education records, disciplinary records, health insurance and financial information
The school district in Louisiana’s St. Landry Parish waited five months to notify people that their Social Security numbers and other sensitive information were made public after it fell victim to a July 2023 ransomware attack — long after state law mandates and only after a newspaper investigation prompted an inquiry from the Louisiana attorney general’s office.
A December 2023 investigation by The 74 and The Acadiana Advocate contradicted school district assertions that no sensitive information about students, employees or business owners had been exposed online after the attack.
Stolen files, the investigation found, include thousands of health insurance records with the Social Security numbers of at least 13,500 people, some 100,000 sales tax records for local and out-of-state companies and several thousand student records, including home addresses and special education status.
Four months after the attack, more than a dozen breach victims told reporters they were unaware their information was readily available online.
“They want to brush everything under the rug,” said Heather Vidrine, a former St. Landry teacher whose information was exposed in the breach. “The districts don’t want bad publicity.”
Threat actors with the Medusa ransomware gang claimed a cyberattack on the St. Landry school system in July 2023, and the district reported it to the local press and police within days. Cybercriminals published reams of stolen files after the district did not pay its $1 million ransom demand, yet district leaders denied the breach affected sensitive records even after reporters presented them with extensive evidence to the contrary.
After notifying state police about the attack, district officials were never told about the nature of the data that was stolen or if anything was stolen at all, Tricia Fontenot, the district’s supervisor of instructional technology, said. In the face of cyberattacks, districts routinely hire cybersecurity consultants and attorneys to review the extent to which any sensitive information was exposed and to comply with state data breach notification laws.
“We never received reports of the actual information that was obtained,” she said in November 2023. “All of that is under investigation. We have not received anything in regards to that investigation.”
Just hours after the newspaper investigation revealed the data breach, a consumer protection lawyer with the state attorney general’s office was on the phone with the district, questioning them “directly in response to the article” and informing them of their data breach notification obligations under state law, emails obtained by The Advocate reveal.
Under Louisiana’s breach notification law, schools and other entities are required to notify affected individuals “without unreasonable delay,” and no later than 60 days after a breach is discovered. Entities that fail to alert the state attorney general’s office within 10 days of notifying affected individuals can face fines up to $4,000 for each day past the 60-day mark.
School board attorney Courtney Joiner responded a day later, saying they were working “to address the notice issue without further delay.”
In a Dec. 21, 2023, letter, Superintendent Milton Batiste III acknowledged to an undisclosed number of victims that their “sensitive information may have been obtained by an unknown malicious third-party,” records show. Officials didn’t send a formal notice to the attorney general’s office until Jan. 10.
Math teacher Donna Sarver was among the district educators who received the data breach notification. She blasted school leaders for sending the letter “well after the fact” she and her colleagues had been victimized.
“I really thought it was too little, too late,” she told reporters. “This should have happened much earlier.”
School officials couldn’t be reached for comment for this story.
Emerson Public Schools
Location: Emerson, New Jersey
Breach date: August 2023
Threat actors with the Medusa ransomware gang claimed an August 2023 cyberattack on the Emerson, New Jersey, school system posting the district on its leak site.
The attack unfolded on the same day that education and technology leaders met at the White House for a summit to address cyberattacks on public schools.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Hopewell Area School District
Location: Aliquippa, Pennsylvania
Breach date: October, 2023
Info exposed: Children’s photographs and educators’ names, addresses, email addresses and salaries
School officials at the Hopewell Area School District in Aliquippa, Pennsylvania, told local reporters in October 2023 that they had become the victim of “a sophisticated ransomware attack by unknown criminal actors.”
A month later, threat actors with the Medusa ransomware gang posted the district on its leak site which, according to SuspectFile, exposed about 120 gigabytes of stolen records with sensitive information, including photographs of children and educators’ names, addresses, email addresses and salaries.
The 74 was unable to identify any data breach notices that the district sent to victims of the incident. School officials couldn’t be reached for comment.
Great Valley School District
Location: Malvern, Pennsylvania
Breach date: November 2023
Info exposed: Names, medical information and Social Security and driver’s license numbers
Threat actors with the Medusa ransomware gang took credit in November 2023 for a cyberattack on the Great Valley School District in Malvern, Pennsylvania.
On the dark web, hackers demanded a $600,000 ransom and posted sensitive student and employee records in a bid to coerce payment, according to DataBreaches.Net, a blog that tracks and reports on data breaches globally.
By the end of the month, district officials posted — but have since removed — a statement acknowledging third-party consultants “determined that the information potentially accessible during the event may have included personal information.”
Affected information, the district said, included names, medical information and Social Security and driver’s license numbers.
Stolen files, according to researchers at the website SuspectFile, presented a mystery. Records allegedly stolen from the Pennsylvania school district included medical and financial records for an 88-year-old woman from Bradenton, Florida.
“Why were these data,” the website questioned, “on the servers of the Great Valley School District?”
School officials couldn’t be reached for comment.
Campbell County Schools
Location: Alexandria, Kentucky
Breach date: December 2023
Info exposed: Social Security numbers and financial information
Threat actors with the Medusa ransomware gang claimed in December 2023 a cyberattack on the Campbell County school district in Alexandria, Kentucky, an incident that school officials acknowledged exposed sensitive information.
Affected records, the district identified a week after its appearance on Medusa’s blog, contained employees’ confidential information, including Social Security numbers and financial information.
School officials couldn’t be reached for comment.
Glendale Unified School District
Location: Glendale, California
Breach date: December 2023
Info exposed: Employees’ names, addresses, birth dates, Social Security and driver’s license numbers and financial information
Teachers at the Glendale, California school district were reportedly the victims of tax fraud after threat actors with the Medusa ransomware gang claimed a cyberattack on the district in December 2023.
More than 230 educators were required to verify their identity with the Internal Revenue Service after someone fraudulently filed their taxes.
The district faced criticism that its announcement of the incident was too slow. In early December, the district began to experience initial results of the attack and notified educators to stay logged out of their Chromebooks. A month later, in January 2024, school officials announced that the attack exposed the sensitive records of current employees and former employees and students.
In a breach notice filed with the California state attorney general’s office, the district said the affected information included employees’ names, addresses, birth dates, Social Security and driver’s license numbers and financial information.
In response to an inquiry from The 74, the district declined to comment citing pending litigation.
Hinsdale School District
Location: Hinsdale, New Hampshire
Breach date: November 2023
The Hinsdale, New Hampshire, school district was the victim of a cyberattack in November 2023. A month later, in December, 2023, threat actors with the Medusa ransomware gang posted the school district on its leak site.
It wasn’t until June 2024 that a breach notice was submitted to the New Hampshire attorney general’s office by lawyers with the firm McDonald Hopkins. The district “experienced a network security incident” in early December, according to the notice, and school officials began “working very closely with external cybersecurity professionals” to investigate the incident. In May 2024, the investigation revealed “a limited amount of information may have been accessed by an unauthorized individual.”
Though the notice states that the breach affected 89 New Hampshire residents — and notices were filed in other states including with the Montana Office of Consumer Protection — the letters were redacted to withhold the specific types of information revealed in the breach.
A month later, in July 2024, the district filed an amended breach notice with the New Hampshire attorney general’s office, disclosing an additional 647 New Hampshire residents had been affected.
School officials couldn’t be reached for comment.
Traverse City Area Public Schools
Location: Traverse City, Michigan
Breach date: March 2024
Info exposed: Educator personal information
Threat actors with the Medusa ransomware gang took credit in April 2024 for a cyberattack on the Traverse City, Michigan school district, claiming a massive data breach of 1.2 terabytes of stolen district records.
The district acknowledged the March attack, which led to network disruptions and forced school closures, that same month, announcing it hired third-party consultants to investigate the breach and that its insurance provider had been alerted.
“We don’t have any information that shows of any kind of breach of any personal information or anything,” Superintendent John VanWagoner told a local television station that month.
In June 2024, the Traverse City Record-Eagle reported that the breach included employees’ sensitive information after Medusa sought a $500,000 ransom from the district. A month earlier, according to the newspaper, a district employee informed officials that her husband found personal information about district staff on the dark web. District officials referred him to a cybersecurity firm investigating the breach under a retainer by the district’s insurance provider.
Two weeks later, 932 employees received emails alerting them that the hack had exposed their personal information, but further details were not reported. VanWagoner told the newspaper only he was authorized to speak publicly about the hack.
In an interview with The 74 in November, VanWagoner said the attack brought confusion and uncertainty, and that the district’s insurance company and third-party lawyers offered little guidance. The insurance company presented it with the choice of several cybersecurity firms that it could hire to recover from the attack, he said, but “I didn’t know where to go to vet if they were any good or not.”
He said it was a member of the community — not one of its consultants — who first alerted district officials about the extent of the breach.
“We were literally taking that right to the cyber companies and going, ‘Hey, they’re finding this, can you confirm this so that we can get a message out?’” he told The 74. “That is what I probably would tell you is the most frustrating part is that you’re relying on them and you’re at the mercy of that a little bit.”
River Delta Unified School District
Location: Rio Vista, California
Breach date: December 2023
Threat actors with the Meow ransomware gang claimed in February 2024 a cyberattack on the Rio Vista, California, school district, posting the district on its leak site.
But a data breach notice submitted to California regulators in September 2024 acknowledges the breach transpired two months earlier, in December 2023. The notice, which was submitted to the California attorney general’s office nine months after the incident transpired, cites that sensitive information was stolen but didn’t specify the types of files that were stolen.
School officials couldn’t be reached for comment.
Lower Yukon School District
Location: Mountain Village, Alaska
Breach date: August 2023
Alaska’s Lower Yukon School District experienced a ransomware attack in August 2023. Threat actors with the No Escape ransomware group took credit for the attack, posting the district on its dark web leak site.
“Your confidential documents, personal data and sensitive info has been downloaded,” the group wrote in a ransom note obtained by The 74. “Published information will be seen by your colleagues, competitors, lawyers, media and the whole world.”
District records were published on the dark web after officials did not pay a $300,000 ransom. A review of the breached files by The 74, however, failed to turn up any sensitive information about students or educators.
In an interview, the district’s IT director told The 74 that Lower Yukon officials were instructed by their insurance provider to avoid using the word “breach” when discussing the incident with the public.
Buffalo School District
Location: Buffalo, New York
Breach date: March 2021
Info exposed: Social Security numbers, students’ names, race and ethnicity records; special education records, home addresses and direct deposit records
Threat actors with the Pysa ransomware group claimed a March 2021 cyberattack on the Buffalo, New York, school district that exposed employees’ Social Security numbers and other sensitive information to the dark web.
The district acknowledged a March 2021 data breach in a notice to the Maine attorney general’s office, which notes that school officials discovered the attack that month but didn’t notify affected victims until May, two months later. The incident exposed the sensitive information of 14,039 people, the Maine disclosure notes, after the district experienced a “cybersecurity outage as a result of a ransomware attack,” that accessed Social Security numbers, demographic information and direct deposit records.
Though the district never paid a ransom, according to The Buffalo News, it spent $10 million in response, primarily for IT consultants.
Buffalo school officials notified some 110,000 people that their information may have been exposed, according to the district, including former teachers and current and former students. What information was ultimately compromised, however, remains a mystery with disgruntled community members urging greater transparency.
Just days after the attack, the superintendent sent a letter to employees stating that an initial investigation did not determine “There has been an exposure of personally identifiable information.”
The district reversed that statement in May, acknowledging the breach included personally identifiable information about students, including their name, gender, race and ethnicity, special education status and primary language spoken at home. It also exposed parents’ names and home addresses.
District spending records captured in the GovSpend government procurement database suggest Buffalo schools suffered a second cyberattack in early 2024. In March, the district spent more than $34,000 for the “estimated cost to address cyber incident” and for the “estimated cost of printing & mailing cyber incident response.”
School officials couldn’t be reached for comment.
Gering Public Schools
Location: Gering, Nebraska
Breach date: March 2020
Info exposed: Social Security numbers, financial account and health insurance information, medical and special education records; student names, birth dates and addresses
Threat actors with the Pysa ransomware gang claimed a cyberattack on the Gering, Nebraska, school district, which acknowledged in March 2021 that sensitive information had been exposed.
The incident transpired a year earlier, in March 2020, according to an alert to the consumer protection office in Montana. The breach notice submitted to victims in March 2021 notes that the district hired third-party consultants to investigate the incident, determining that an “unauthorized party” had access to Social Security numbers, financial account information, health insurance records and medical documents.
The Pysa attack leaked sensitive files about students that were not disclosed in the breach notice, including their demographic information and special education records, according to review of the cyber gang’s dark web leak site by DataBreaches.Net, a blog that tracks and reports on data breaches globally.
School officials couldn’t be reached for comment.
Brookfield Public Schools
Location: Brookfield, Connecticut
Breach date: September 2021
Threat actors with the Pysa ransomware group claimed a cyberattack on the Brookfield, Connecticut, school district, posting the school system to its leak site in September 2021.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
St. Mary School Hyde Park
Location: Cincinnati, Ohio
Breach date: September 2021
Threat actors with the Pysa ransomware group claimed a cyberattack on St. Mary School Hyde Park in Cincinnati, Ohio, posting the Catholic school on its leak site in September 2021.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Burnham Wood Charter Schools
Location: El Paso, Texas
Breach date: March 2024
Threat actors with the Qilin ransomware gang claimed a cyberattack on Burnham Wood charter school network in El Paso, Texas, posting the network on its leak site in March 2024.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Altoona Area School District
Location: Altoona, Pennsylvania
Breach date: December 2021
Info exposed: Social Security numbers, medical records, students’ birth dates and addresses
Threat actors with the Quantum ransomware group claimed a cyberattack on the Altoona, Pennsylvania, school district, posting the district on its leak site in February 2022.
A month later, in mid-March 2022, the district superintendent spoke out about a “cyber security incident” that had actually unfolded months earlier — in December 2021. In March, district employees informed education leaders that they received alerts from credit monitoring services notifying them that their Social Security numbers and medical information had been exposed on the dark web, according to news station WJAC. Students’ birth dates and home addresses were also exposed in the incident.
In an April 2022 breach notice with the U.S. Department of Health and Human Services, the district acknowledged that 9,196 people enrolled in the Altoona school district’s health plan had their sensitive information exposed.
The district also disclosed the incident to the Indiana attorney general’s office in April 2022, informing regulators that 17,596 people had become data breach victims after suffering the attack on Nov. 30, 2021.
School officials couldn’t be reached for comment.
Camden City School District
Location: Camden, New Jersey
Breach date: March 2021
Info exposed: Social Security numbers
The Camden, New Jersey, school district spent hundreds of thousands of dollars on third-party cybersecurity lawyers after a cyberattack forced the district into remote learning and the Quantum cybercrime syndicate posted the district to its leak site in April 2022.
Yet educators went 13 months without knowing their personal information had been exposed on the dark web, according to documents obtained by The 74 through a public records request.
Among district expenditures were those paid to Mullen Coughlin, the “legal vendor assigned by district insurance carrier” in response to a March 2022 cyberattack, according to GovSpend, a database that tracks government procurement.
In the attack’s immediate aftermath, the district emailed its employees and disclosed that it “recently discovered anomalous activity in our network” but that officials had “not confirmed what data was impacted as a result.”
More than a year later, in April 2023, current and former district employees received letters informing them that their Social Security numbers and other sensitive information had been leaked. That 13-months-later breach notice seemed to send some school officials into a panic — and prompted a district apology.
“I respectfully apologize for the angst this has caused those of you who received the notice,” the district’s business administrator wrote in an email, adding that it was the Mullen Coughlin attorneys assigned to Camden schools by its cybersecurity insurance provider who had sent the letters. “Unfortunately, they were sent without my knowledge which resulted in me not being able to preemptively advise each of you about the notice and what it meant.”
There had been “no new cyber security breach,” the email explains. Rather, the third-party consultants investigating the breach prepared notices based on the names and emails that appeared in the leaked data.
“I recognize these notices are coming significantly late, and at a time when many may have forgotten about that week in March 2022,” the email states. “The reason for this is that it has taken time for the cyber firms to review and evaluate the data which they were able to obtain.”
School officials couldn’t be reached for comment.
Lumberton Independent School District
Location: Lumberton, Texas
Breach date: June 2023
Info exposed: Social Security numbers, names, birth dates and financial account information
More than 1,300 people had their sensitive information exposed in a data breach after the Lumberton, Texas, school district became the victim of a ransomware attack.
Officials first disclosed the incident in June 2023, announcing an investigation with third-party cybersecurity consultants and a commitment to “satisfying any resulting regulatory and legal obligations” should a data breach be identified.
Threat actors with the Rhysida ransomware gang took credit for the attack, posting the district on its leak site in July 2023. An analysis of the leaked data by The 74 revealed reams of Social Security cards, driver’s licenses and contact information for district employees.
Months later, in September 2023, Lumberton school officials acknowledged the breach in a notice to the Texas attorney general’s office. That same month, third-party attorneys hired by the district notified the Maine attorney general’s office of a “network disruption” that leaked Social Security numbers, names, birth dates and financial account information.
The regulatory notice discloses that the “hacking” incident occurred in June 2023 but the breach wasn’t “discovered” until September, less than a month before victims were notified of the attack.
School officials couldn’t be reached for comment.
Prince George’s County Public Schools
Location: Upper Marlboro, Maryland
Breach date: August 2023
Info exposed: Names, medical and health insurance information, Social Security, driver’s license and passport numbers, login credentials and financial information
The sensitive records of more than 100,000 people were exposed on the dark web after Maryland’s Prince George’s County Public Schools fell victim to a ransomware attack in August 2023.
Yet the school district in suburban Washington, D.C., didn’t notify the 117,785 data breach victims that their Social Security numbers and other sensitive information had been exposed until March 2024 — some seven months later.
In a breach notice submitted to the Maine attorney general’s office, the district said it discovered on August 14, 2023, that its systems had been “encrypted with ransomware,” and an investigation by third-party cybersecurity contractors concluded by mid-January that sensitive information had been exposed.
Threat actors with the Rhysida ransomware gang claimed responsibility for the attack, listing the district on its dark web leak site and threatening to publish the stolen files unless the district paid it some $375,000 in bitcoin. Threat actors ultimately uploaded the entire collection of stolen records after offering an initial preview of files in its possession, including birth certificates and passports.
Records obtained by The 74 through a public records request show the district retained attorneys with the cybersecurity and privacy law firm Mullen Coughlin “via the district’s cyber insurance program.” The district participates in a self-insurance program managed by Prince George’s County government.
Mullen Coughlin became a primary point of contact for other consultants hired to investigate and recover from the event, records show, and was paid more than $50,000 for its role. The consulting firm Charles River Associates submitted invoices totaling some $243,000, for “data mining, analysis, forensics and incident response.”
A school district attorney denied The 74’s public records request for communications between the district and Mullen Couglin, citing attorney-client privilege.
Meanwhile, school officials have sought to withhold certain records related to the cyberattack. A request by the state teachers union’s attorney for certain records related to the attack in December 2023 was rejected. Prince George’s didn’t put out a request for proposal for “cybersecurity services,” the district wrote in a response letter, because they were “provided pursuant to the existing cyber policy in the district’s self-insurance program.”
The district declined to release any investigative findings into the attack because their disclosure, it wrote, “could have a negative impact on the ongoing investigation and forensic analysis.”
A district lawyer told The 74 a complete accounting on the sensitive records exposed in the breach included names, medical and health insurance information; Social Security, driver’s license and passport numbers; login credentials and financial information.
In response to a later inquiry by The 74, a district spokesperson said it “communicated frequently during the February 2024 cyber incident,” a reference to the date of the breach notice, “and provided our school community with updated information throughout the process.”
“Communication included information provided by a third-party cyber forensic investigation about the scope and type of impacted data,” the statement to The 74 adds.
Adams-Friendship Area School District
Location: Friendship, Wisconsin
Breach date: November 2022
Info exposed: Names, addresses, birth dates, Social Security numbers, health insurance records and financial account information
Threat actors with the Royal ransomware group claimed a cyberattack on the Friendship, Wisconsin, school district, posting the district to its leak site in December 2022.
The district submitted a January 2023 breach notice to the Indiana attorney general’s office, disclosing that the sensitive information of 1,366 people was exposed. The “ransomware incident,” according to a breach notice with Montana regulators, exposed individuals’ names, addresses, birth dates, Social Security numbers, health insurance records and financial account information.
School officials couldn’t be reached for comment.
Tucson Unified School District
Location: Tucson, Arizona
Breach date: January 2023
Info exposed: Social Security numbers
Nearly 30,000 people had their sensitive information leaked to the dark web after a January 2023 ransomware attack targeted the Tucson, Arizona, school district where officials initially told the public that their private records had not been stolen by hackers.
Parents expressed frustration with the district’s lack of transparency. Tucson school leaders later announced that recovery costs would be in the millions and requested an “at least 20 percent” increase in its budget.
The Arizona attack, which the Royal ransomware gang took credit for orchestrating, led to a data breach notice on the opposite side of the country — with the Maine attorney general’s office. The notice, filed by Dominic Paluzzi of the McDonald Hopkins law firm, was sent to victims in August 2023 — eight months after the incident crippled the district.
Though the letter never uses the word “ransomware,” it acknowledges the district suffered a “cyber incident” similar to those nationwide that exposed people’s Social Security numbers.
“It is estimated that at least 48 other school districts have experienced this situation since the beginning of the year, and we are fortunately able to learn from our shared experience to make ever-better provisions for the safety of our information technology systems,” the letter states.
School officials couldn’t be reached for comment.
Dallas School District
Location: Dallas, Oregon
Breach date: January 2023
Threat actors with the Royal ransomware group claimed an attack on the Dallas, Oregon, school district, posting the school system to its leak site in February 2023.
However, the district didn’t disclose the breach with state regulators, in Oregon or elsewhere, until June 2023. A breach notice submitted to Montana’s consumer protection office notes that threat actors launched the attack in January 2023, leading to an investigation by third-party consultants that concluded in May. The letter was redacted and the types of sensitive records exposed remains unknown.
School officials couldn’t be reached for comment.
Lake Dallas Independent School District
Location: Lake Dallas, Texas
Breach date: April 2023
Info exposed: Social Security and driver’s license numbers, medical records and health insurance information
When the Royal ransomware gang posted the Lake Dallas, Texas school district to its leak site in April 2023, threat actors mocked the school system for claiming it offered “a progressive, innovative atmosphere.”
A cyberattack that resulted in the leak of hundreds of Social Security numbers and passports, the group wrote on its leak site, “is the result of being non-progressive in cybersecurity.”
“Enjoy!”
A May 2023 breach notice to the Texas attorney general’s office notes that 21,982 state residents were affected in the incident. Exposed data, it states, includes victims’ Social Security and driver’s license numbers, medical records and health insurance information.
School officials couldn’t be reached for comment.
Nashua School District
Location: Nashua, New Hampshire
Breach date: April 2023
Info exposed: Names, Social Security numbers, birth dates, health insurance and financial account information and medical records
When threat actors with the Royal ransomware gang claimed a cyberattack on the Nashua, New Hampshire school district in May 2023, they announced on their leak site that “a crazy amount of databases will be uploaded” if school leaders didn’t pay the ransom.
A February 2024 breach notice submitted to state regulators by attorneys with the firm Mullen Coughlin made clear the extent of the attack’s effects on individuals. The document states that school officials first discovered unusual activity on their computer network in April 2023 — 10 months before the breach notice became public. Exposed information, the notice discloses, includes names, Social Security numbers, birth dates, health insurance and financial account information.
In total, according to a breach notice submitted in Maine, the “hacking” incident exposed the sensitive records of 9,829 people.
Asked by The 74 about the delay in the breach notice, Superintendent Mario Andrade said in an email “I think it would be prudent to contact Mullen Coughlin as to the delay in the filing.”
“I can’t speak to what factors necessitated their delay,” the email continued. “ The law firm provided guidance after the cyberattack and assisted us in filing the proper legal notifications to all parties.”
Penncrest School District
Location: Saegertown, Pennsylvania
Breach date: May 2023
In May 2023, threat actors with the Royal ransomware gang claimed a cyberattack on the Saegertown, Pennsylvania, school district.
In response, the district acknowledged on its website that month that it was working with third-party cybersecurity consultants to investigate the ransomware attack and that they had not “identified evidence of any data loss, data access or data theft as a result of this event.”
In response to an inquiry from The 74, Superintendent Shawn Ford said in an email that “the people who dealt with the cyber attack are no longer employed in the district,” and declined to comment further.
Braintree Public Schools
Location: Braintree, Massachusetts
Breach date: July 2023
Threat actors with the Royal ransomware gang claimed in July 2023 a cyberattack on the Braintree, Massachusetts, school district. When threat actors first listed the district on its leak site, the cybercriminals offered a 140-terabyte download file.
By the end of the month, and ahead of an August White House summit on K-12 school cybersecurity, hackers released a press release claiming it made an “executive decision” on a “purely voluntary basis” not to publish the district’s data and would not require a ransom payment.
“We acknowledge that such a decision is not merely a matter of policy or compliance, but a fundamental act of respect for every student and teacher whose information we now steward,” according to the statement, which characterizes the threat actors as having “ethical boundaries” unlike their competitors.
School officials couldn’t be reached for comment.
Kenosha Unified School District
Location: Kenosha, Wisconsin
Breach date: September 2022
Info exposed: Employee records
Threat actors with the Snatch ransomware gang claimed a September 2022 cyberattack on the Kenosha, Wisconsin, school district, which announced it had become the targets of a “cybersecurity incident.”
The district disclosed the September attack to the public that same month, notifying employees that their personal information may have been exposed, officials said in a statement to DataBreaches.Net, a blog that tracks and reports on data breaches globally.
School officials couldn’t be reached for comment.
Lawrence Family Development Charter School
Location: Lawrence, Massachusetts
Breach date: May 2023
Threat actors with the Snatch ransomware group claimed in May 2023 a cyberattack on the Lawrence Family Development Charter School in Lawrence, Massachusetts.
When The 74 contacted the charter school for comment, a third-party communications firm hired by the Massachusetts Charter Public School Association said “someone opened an email with a [Trojan] malware virus,” but officials “were able to shut it down within 15 minutes.”
“The claim of an attack is bogus,” spokesperson Dominic Slowey wrote in the email. “Technically someone opened an email with malware, so he’s assuming this group is taking credit for a hack, because of that, but it was caught before it could do any damage.”
Ancillae-Assumpta Academy
Location: Wyncote, Pennsylvania
Breach date: October 2023
Threat actors with the Snatch ransomware group claimed in October 2023 a cyberattack on Ancillae-Assumpta Academy, a private Catholic school in Wyncote, Pennsylvania.
The 74 didn’t identify additional information about the incident. School officials couldn’t be reached for comment.
Montachusett Regional Vocational Technical School District
Location: Fitchburg, Massachusetts
Breach date: November 2023
Info exposed: Names, birth dates, Social Security Numbers
Threat actors with the Snatch ransomware gang claimed in November 2023 a cyberattack on the Montachusett Regional Vocational Technical School District in Fitchburg, Massachusetts.
In a breach notice submitted to state regulators a month later, in December 2023, officials disclosed that a “recent data security incident” had exposed sensitive information, including people’s names, birth dates and Social Security numbers.
School officials couldn’t be reached for comment.
Dooly County School System
Location: Vienna, Georgia
Breach date: December 2022
Threat actors with the UnSafe ransomware gang claimed in December 2022 a cyberattack on the Vienna, Georgia, school district.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Carthage R-9 School District
Location: Carthage, Missouri
Breach date: December 2021
Info exposed: Names, Social Security and phone numbers, addresses, tax records and bank account information
Threat actors with the Vice Society ransomware gang claimed in December 2021 a cyberattack on the Carthage, Missouri, school district, which officials initially called a “cyber event.”
A month later, in early January 2022, the district acknowledged it was the victim of a ransomware attack and that cybercriminals were threatening to publish stolen information on the dark web.
Stolen files published to the dark web contain the tax records of more than 1,000 district employees, including their Social Security numbers, according to a review by DataBreaches.Net, a blog that tracks and reports on data breaches globally. Outreach efforts to the district regarding the leak, however, “have gone unanswered.”
In a breach notice submitted in mid-January to Montana state regulators, the district disclosed that a “data security incident” had leaked individuals’ names, Social Security and phone numbers, addresses and bank account information.
School officials couldn’t be reached for comment.
Lufkin Independent School District
Location: Lufkin, Texas
Breach date: January 2022
When threat actors with the Vice Society ransomware gang claimed in January 2022 a cyberattack on the Lufkin, Texas, school district, its chief technology officer noted in a blog post the incident “really left us paralyzed” after the cybercriminals encrypted records and demanded a $1.5 million ransom.
The district was able to recover the data of 11,000 employees and students without paying the ransom demand, according to a Dell Technologies case study.
In the hack’s aftermath, Lufkin hired attorneys with BakerHostetler to investigate and respond, according to an insurance claim obtained by The 74 through a public records request.
The district’s insurance policy notes that covered services include any expenses it is “legally obligated to pay because of a regulatory proceeding” and breach response services including public relations and crisis management “directly related to mitigating harm.”
School officials couldn’t be reached for comment.
Manhasset Union Free School District
Location: Manhasset, New York
Breach date: September 2021
Info exposed: Names, Social Security numbers and financial account information
Threat actors with the Vice Society ransomware gang claimed in January 2022 to have caught the Manhasset, New York, school district in a cyberattack — an incident that school officials acknowledged leaked the sensitive records of thousands of people.
In a breach notice to the Maine attorney general’s office filed by an attorney with the law firm BakerHostetler, the district disclosed the “hacking” incident began in September 2021.
Yet it wasn’t until April 2022, seven months later, that victims were notified that their sensitive information had been exposed, including their names, Social Security numbers and financial account information.
School officials couldn’t be reached for comment.
San Luis Coastal Unified School District
Location: San Luis Obispo, California
Breach date: May 2022
Info exposed: Names, Social Security numbers and birth dates
Threat actors with the Vice Society ransomware group claimed in August 2022 a cyberattack on the San Luis Obispo, California, school district, an incident that school officials acknowledged a month later had exposed people’s sensitive information to the dark web.
In a breach notice filed with the California attorney general’s office in September, the district reported that the attack had actually begun in May, four months earlier, and compromised individual’s names, Social Security numbers and birth dates.
An editorial in a local newspaper, The Tribune, noted that the district never notified the press about the attack, which went unreported until an October 2022 story in EdSource. School officials couldn’t be reached for comment.
Whitehouse Independent School District
Location: Whitehouse, Texas
Breach date: June 2021
Info exposed: Students’ names, Social Security numbers, health records and birth dates
School district officials in Whitehouse, Texas, acknowledged in December 2021 that students’ personal information was compromised in a ransomware attack that transpired nearly six months earlier.
Threat actors with the Vice Society ransomware group took credit for the attack, listing the district on its dark web leak site. A review of the stolen data by The 74 turned up reams of sensitive information, including thousands of Social Security numbers, birth certificates, academic records and both student and employee disciplinary records.
In a December 2021 letter to parents, the district acknowledged that students’ information had been compromised, including their names, Social Security numbers, health records and birth dates.
In the attack’s immediate aftermath, the district acknowledged to the public that some sensitive information, including Social Security numbers, had been compromised in the breach. That notice came some three weeks after officials informed the district’s insurance provider, records reveal.
The insurance carrier required education officials to get its approval “prior to incurring any fees or expenses in connection with this matter,” and urged them to hire an attorney who specializes in privacy laws, according to records obtained by The 74 through a public records request.
In response, Whitehouse hired attorneys with the firm Mullen Coughlin to “investigate, provide legal advice and otherwise assist with response to a potential data security incident.”
A district spokesperson declined to provide additional records to The 74, noting in an email that aside from public statements posted to its website, district communications regarding the incident “went through a legal team and is confidential information.”
Frederick Public Schools
Location: Frederick, Oklahoma
Breach date: April 2021
Info exposed: Social Security numbers
Threat actors with the Vice Society ransomware gang took credit for an April 2021 cyberattack on the Frederick, Oklahoma, school district, an incident that district officials acknowledged to out-of-state regulars exposed thousands of sensitive records, including Social Security numbers.
In a breach notice filed with the Maine attorney general’s office by a third-party law firm, the district disclosed that 4,326 people were affected in a “hacking” incident. Victims weren’t notified, however, until July 2021 — nearly three months after the attack. School officials couldn’t be reached for comment.
Moon Area School District
Location: Moon, Pennsylvania
Breach date: August 2022
Info exposed: Student records
Threat actors with the Vice Society ransomware gang claimed a cyberattack on the Mars, Pennsylvania, school district just days before the start of a new academic year in August 2022.
A review by The 74 of the Vice Society leak site turned up students’ records and although the district announced it was hiring third-party consultants to investigate the breach, it remains unclear whether school officials notified victims that their information had been exposed. School officials couldn’t be reached for comment.
Elmbrook Schools
Location: Elmbrook, Wisconsin
Breach date: August 2022
Info exposed: Social Security numbers, passports
At the start of the school year in 2022, threat actors with the Vice Society ransomware gang claimed a cyberattack on the Elmbrook, Wisconsin, school district, posting troves of files to the group’s dark web leak site.
When the district disclosed the breach to the public, they offered an assurance: No Social Security numbers belonging to students were published by the hackers. Meanwhile, a review of the leaked files by The 74 turned up scanned copies of students’ and adults’ passports.
Asked by The 74 about the presence of childrens’ passports in the breach, district officials didn’t respond directly, instead noting that Elmbrook Schools “had significant security measures in place that limited the operational impact of the attack.”
“Over the past several months, we have devoted significant resources to reviewing the compromised data and have already begun to provide notifications to impacted individuals in accordance with data breach notification laws,” the district statement continues.
In Maine, attorneys with the firm McDonald Hopkins submitted a breach notice to the attorney general’s office on the district’s behalf in September 2022, disclosing that a “hacking” event in August exposed the sensitive information of 4,356 people — including their Social Security numbers.
The district spokesperson said in a November 2024 email that Elmbrook used its insurance policy for a cyber incident response team and attorneys with McDonald Hopkins, which “helped navigate the state filing requirements.”
“After securing our network and doing a deep scan of the employee files that were compromised, we engaged a third party to do a deep scan of all files that were posted to the dark web,” the spokesperson said. “This revealed a limited number of files containing student information. Based on those findings, appropriate notice was given.”
Los Angeles Unified School District
Location: Los Angeles, California
Breach date: September 2022
Info exposed: Names, addresses, birth dates and health, special education disciplinary and academic records
The Los Angeles Unified School District was ensnared by three high-profile cyberattacks in the last few years, each of which exposed reams of sensitive information online.
Three subsequent class-action lawsuits from parents accused the nation’s second-largest district of taking inadequate steps to protect their children’s personal records — and failing to tell them that sensitive information had been leaked. The district has since taken multiple steps to shield details about the incidents from public view.
The trio of events encompass a September 2022 ransomware attack that exposed students’ highly sensitive psychological evaluations among other records; a January 2022 cyberattack on education technology company Illuminate Education, which compromised sensitive information in Los Angeles and districts nationwide; and a massive June 2024 cyberattack on the cloud computing company Snowflake, a third-party vendor used by the district to store certain records.
Threat actors with the Vice Society cybergang took credit for the September 2022 ransomware attack on L.A. schools, posting the records to its dark web leak site after education officials did not pay its extortion demand. In the aftermath of the attack, Superintendent Alberto Carvalho sought to downplay its effect on students. An anonymous law enforcement source told the local press that students’ psychological evaluations were included in the leak, a revelation Carvalho refuted as “absolutely incorrect.”
“We have seen no evidence that psychiatric evaluation information or health records, based on what we’ve seen thus far, has been made available publicly,” said Carvalho, who acknowledged the hackers had “touched” the district’s massive student information system but said the “vast majority” of exposed student records involved their names, academic records and home addresses.
An investigation by The 74 into the leak uncovered that the breach had, in fact, exposed student psychological evaluations, which contain a startling degree of personally identifiable information about students receiving special education services, including their detailed medical histories, academic performance and disciplinary records. Just hours after the story published, the district acknowledged in a statement that “approximately 2,000” student psychological evaluations — including those of 60 current students — had been uploaded to the dark web.
In a statement to The 74, a district spokesperson said its cybersecurity response protocol “follows a clear, structured process that prioritizes swift internal assessment and adherence to all applicable state and federal data privacy regulations.” The process, the district said, is “designed with transparency, compliance and community trust in mind.”
Due to the sensitive nature of the information, students may have to “deal with this breach for the rest of their lives,” attorney Ryan Clarkson told The 74. Clarkson represents students and parents in a class-action lawsuit alleging LAUSD failed to act on known cybersecurity vulnerabilities and provided families insufficient notice that students’ personal records had been compromised.
“It’s hard to bury it, it’s hard to get away from it, it’s kind of part of who we are,” Clarkson said in an interview. “Your psychology as a child is always going to be your psychology as a child.”
While the parents of special education students had been left in the dark about the breach, so too were members of the district’s special education committee. Carvalho acknowledged at a September 2022 special education committee meeting that L.A. Unified was a “district under siege” and sought to “dispel rumors” about the incident, including one that multiple attacks had occurred. He didn’t make any statements regarding the impact on sensitive special education records.
Carl Petersen, who served on the committee at the time, told The 74 that Carvalho left the committee members without information about the attack’s ramifications on children with disabilities.
“At that point it was, ‘Oh, this was a very minor thing. We caught them in the system immediately and we shut it down,” said Petersen, who described Carvalho’s comments as part of a larger district effort to obfuscate.
In January 2023 — four months after the attack — L.A. school officials acknowledged in a submission to the California attorney general’s office that sensitive records had been exposed but only listed Social Security numbers included in payroll records and third-party contractor files swept up in the breach. It wasn’t until March 2023 that they disclosed to state regulators the leak had also compromised sensitive student records.
The letter submitted to the California AG’s office doesn’t make clear the types of student records that were affected but urges individuals to “keep a copy of this notice for your records in case of future issues with your child’s medical records.”
The 74 submitted a public records request for information related to the ransomware attack, including complaints submitted to a hotline LAUSD created in its wake, insurance claims, Carvalho’s communications with the FBI and the types of student records that were subject to disclosure. The district denied the requests, stating it could not locate any “non-privileged responsive records,” meaning that they didn’t have to provide any of the records that were responsive because they were legally protected from disclosure.
A week after it was discovered, the school board voted unanimously to grant Carvalho emergency spending powers to recover from the 2022 Labor Day weekend cyberattack, allowing the schools chief a year to “enter into any and all contracts” to address the incident “without advertising or inviting bids and for any dollar amount necessary.”
‘Shared with the world’
In August 2023, nearly a year after the attack, Carvalho made a high-profile appearance at the White House, where then-First Lady Jill Biden warned about the growing threat of cyberattacks on students and a need to do more to protect their sensitive data.
“If we want to safeguard our children’s futures, we must protect their personal data,” she said at the first-ever K-12 cybersecurity summit. “Every student deserves the opportunity to see a school counselor when they’re struggling and not worry that these conversations will be shared with the world.”
Carvalho said quick reaction time by the Los Angeles district and federal law enforcement officials set into motion a response plan that mitigated the attack, limited the number of files breached and avoided class cancellations. His remarks in the East Room didn’t touch on the leak of students’ mental health records but said the number of stolen files “could have been much worse” had officials not acted quickly to prevent the cybercriminals from encrypting additional district systems. One action they had no intention of doing, he said, was paying the undisclosed ransom demand because “we don’t negotiate with terrorists.”
Los Angeles parent Ariel Harman-Holmes, whose three children are in special education, said she’s worried that fallout from the data breach could divert money from the services her children with disabilities need.
“I would rather have those funds go back into the schools and special education rather than spending a ton on litigation or settlements about privacy issues,” said Harman-Holmes, while acknowledging it “would be very disturbing” if her own child’s psychological evaluations were leaked online.
As L.A. Unified’s response to the attack was being lauded by federal officials at the White House summit, its lawyers were in court with parents who alleged the district’s mitigation efforts weren’t just inadequate — they violated the law. Three separate lawsuits filed in Los Angeles County Superior Court charge the district had insufficient safeguards in place to secure students’ sensitive records and failed to provide enough notice to victims once that information was stolen.
An inspector general’s office audit two years before the ransomware attack highlighted cybersecurity vulnerabilities yet, the complaints allege, LAUSD failed to take the necessary steps to prevent the attack. Parents also charge the district failed to comply with state data breach notice requirements after it learned that students’ psychological records and other files were published online.
The most recent complaint was filed in September 2024 against the district and the company InfoSys, which built and manages the My Integrated Student Information System — the district’s primary student data portal. The district “has stated under oath in discovery responses” that InfoSys managed the student information system that was compromised, according to court records filed by the plaintiffs
Insufficient cybersecurity protocols allowed the intrusion to go unnoticed for more than two months, the lawsuit alleges, and, once it was discovered, L.A. school leaders failed to provide “prompt and accurate notice of the data breach.”
The breached portal “is currently the largest student data system in the United States,” the 162-page complaint notes, yet district officials “prioritized a race to incorporate technology in classrooms, with no regard for the risks of harboring troves of student data in online databases subject to cyberattacks.”
One district, three breaches
Months before the Vice Society ransomware attack began, Los Angeles student records were exposed in a cyberattack on ed tech vendor Illuminate Education, which affected districts nationwide. LAUSD submitted a breach notice to the California attorney general’s office in May 2022, some five months after the incident unfolded. The report doesn’t disclose the types of information that were exposed or the number of students who had been affected.
Then, in June 2024, a threat actor who goes by the name “the Satanic Cloud” posted a listing on a notorious dark web marketplace, seeking $1,000 in exchange for what they claimed was a trove of more than 24 million L.A. school district records. A second threat actor, known as “Sp1d3r” similarly posted a listing for records reportedly stolen from the district with a $150,000 price tag.
The district said school data maintained by a third-party vendor was caught up in a cyberattack on the cloud computing company Snowflake, but officials didn’t disclose the name of the vendor or the types of records that may have been compromised.
The district denied a public records request by The 74 seeking information related to the incident, saying that certain files were protected by attorney-client privilege.
The incident doesn’t appear in a California attorney general’s office database of data breaches.
Berkeley County Schools
Location: Berkeley, West Virginia
Breach date: February 2023
Info exposed: Special education and student disciplinary records, Social Security numbers and banking information
Threat actors with the Vice Society ransomware gang claimed in March 2023 a cyberattack on the Berkeley, West Virginia, school district, posting troves of records to the group’s dark web leak site.
In a breach notice that was published — and has since been removed — from the district’s website, officials acknowledged the attack had been carried out in February 2023 and that employees’ Social Security numbers and direct deposit information had been exposed.
A review of the Vice Society leak by The 74, however, suggests the attack was far more extensive than the district disclosed, encompassing a sizeable collection of sensitive records involving children, including special education and disciplinary records.
School officials couldn’t be reached for comment.
Affton School District
Location: Affton, Missouri
Breach date: February 2021
Info exposed: Social Security numbers
Threat actors with the Pysa ransomware group claimed a cyberattack on the Affton, Missouri, school district that officials acknowledged exposed the sensitive information of more than 1,000 people.
In February 2021, the district announced a virtual learning day due to an “unforeseen network outage” and, according to public records obtained by The 74, sought services a day later with the ransomware negotiation firm Arete Advisors and the law firm Mullen Coughlin.
In March, district officials informed their insurance provider about the breach, records show, and in April they filed a breach notice with the Maine attorney general’s office. The “sophisticated cyberattack,” the district disclosed, affected the Social Security numbers of 1,183 people.
The breach notice offered a reversal from earlier district communications. In the attack’s immediate aftermath, a district statement says school officials “do not believe” sensitive information had been compromised.
It goes on to reassure: “As a routine layer of protection this information is stored on offsite servers.”
In response to a public records request from The 74, a district official said it couldn’t provide a copy of breach notices submitted to individual victims because “they were handled by a third party.” Responding to a question about police involvement, the spokesperson said that while the FBI participated in a phone interview with district officials, “no report or case number was provided and they elected to not come on-site, local law enforcement was not contacted.”
School officials couldn’t be reached for comment.
Immanuel Lutheran Church and School
Location: Riverside, California
Breach date: September 2021
Threat actors with the Pysa ransomware gang claimed in September 2021 a cyberattack on the Immanuel Lutheran Church and School, posting the institution to its leak site.
The 74 didn’t identify additional Information about the incident and neither the church nor the school appear in a state data breach database maintained by the California attorney general’s office. School officials couldn’t be reached for comment.
Haverhill Public Schools
Location: Haverhill, Massachusetts
Breach date: April 2021
Info exposed: Social Security and driver’s license numbers and login credentials
Haverhill, Massachusetts, school officials canceled classes in April 2021, acknowledging the district experienced a ransomware attack but said it was caught early by its IT department “before large scale corruption of the system.”
Months later, in September 2021, threat actors with the Pysa ransomware gang claimed it carried out an attack on the district. It’s unclear whether the two incidents are connected.
In a breach notice filed with Massachusetts regulators in March 2022 — nearly a year later — the district acknowledged that the April 2021 incident exposed the sensitive records of 229 Massachusetts residents, including their Social Security and driver’s license numbers and login credentials.
In response to an inquiry from The 74, Superintendent Margaret Marotta-Smith said in an email the district’s IT team “did a fantastic job in controlling the Impact of the cyberattack in Haverhill and getting us safely back up in running quickly.”
Baltimore County Public Schools
Location: Baltimore, Maryland
Breach date: November 2020
Baltimore County Public Schools was the victim of a ransomware attack that disrupted virtual learning in November 2020. An inspector general’s report released in 2023 revealed it began when a phishing email was flagged to a district IT worker who “mistakenly opened the email on an unsecured domain.”
The district had been warned of its lax cybersecurity policies multiple times, the report notes, before the attack forced nearly $10 million in recovery costs. Among the expenses, district records cite, were $50,000 in public relations costs.
The district declined to comment.
Richland-Bean Blossom Community School Corporation
Location: Richland, Indiana
Breach date: June 2024
Threat actors with the BlackSuit ransomware gang claimed in June 2024 it carried out a cyberattack on the Richland, Indiana school district. School officials promptly refuted the claim. School officials couldn’t be reached for comment.
Goshen Central School District
Location: Goshen, New York
Breach date: July 2024
The Goshen, New York, school district announced in July 2024 it was the victim of a cyberattack. It remains unclear whether the attack led to the exposure of sensitive information. School officials couldn’t be reached for comment.
Newberg-Dundee School District
Location: Newberg, Oregon
Breach date: June 2024
The Newberg, Oregon, school district acknowledged it was the victim of a cyberattack in June 2024 but school officials declined to disclose whether ransomware was the culprit. School officials couldn’t be reached for comment.
Northern Bedford County School District
Location: Loysburg, Pennsylvania
Breach date: July 2024
Threat actors with Inc Ransom claimed a July 2024 cyberattack on the Loysburg, Pennsylvania, school district. School officials acknowledged the incident a month later.
In an interview with The 74 in November, Superintendent Todd Beatty said the district contacted the Cybersecurity & Infrastructure Security Agency and reported the attack but “the problem is there’s not enough funding and personnel for them to be able to be responsive to incidents.”
“There really is no value because they can’t handle the volume of attacks that are happening,” Beatty said. “This would be a good thing to spend taxpayer money on,” noting that schools have become frequent targets of hackers.
“If the government would beef this up and take this on, then I think it would be beneficial for every single person in the United States because it impacts businesses and it impacts individuals” who are the subject of data breaches, he continued.
As a result, he said, school districts who lack internal cybersecurity expertise are reliant on third-party firms to recover from attacks. He said the district submitted breach notices to people after an investigation determined their information was leaked.
The district also offered credit monitoring to victims — an overture that he said has grown so common that, “I don’t even think that many people sign up for” as their mailboxes are inundated with breach notices.
Township of Union Public Schools
Location: Union, New Jersey
Breach date: May 2024
Threat actors with the LockBit ransomware gang claimed a May 2024 cyberattack on the Union, New Jersey, school district, alleging it had access to reams of sensitive documents.
The district superintendent acknowledged the school system was hit by a hack that led to a “significant network disruption,” and was investigating whether the breach exposed sensitive records.
School officials couldn’t be reached for comment.
Center Line Public Schools
Location: Center Line, Michigan
Breach date: May 2024
The Center Line, Michigan, school district canceled classes in May 2024 and acknowledged it was the target of a ransomware attack that disabled telephones, security cameras, internet and other digital tools.
The district said it was working with the police and third-party cybersecurity consultants to investigate the attack but that there was no evidence that personal information had been compromised.
School officials couldn’t be reached for comment.
Escondido Union High School District
Location: Escondido, California
Breach date: November 2023
The Escondido, California, school district experienced a cyberattack in November 2023 that led to a data breach, according to a notice to state regulators.
District officials didn’t submit a breach notice to the California attorney general’s office until June 2024 — some seven months later.
It states that an investigation concluded in February 2022 revealed that “certain current and former employees, employee dependents and students” were affected by the data breach. However, the breach notice was redacted and it remains unclear what types of sensitive information fell into the hands of cybercriminals.
School officials couldn’t be reached for comment.
Fullerton Joint Union High School District
Location: Fullerton, California
Breach date: November 2023
Info exposed: Social Security numbers, names and addresses
The Fullerton, California, school district was the victim of a “sophisticated ransomware attack” in November 2023 that led to the exposure of “a limited amount of data on our network,” officials acknowledged in a letter to state regulators two months later.
The January 2024 breach notice was redacted and the specific types of information stolen weren’t disclosed publicly, but an article in a student newspaper notes that letters to victims outlined how the attack exposed employees’ Social Security numbers and other information about students, including their names and addresses.
During a February school board meeting, educators blasted the district for the delayed response and for withholding key information.
“The information, which was extremely limited, came to us nearly a month after the incident,” one educator said about Fullerton’s notice to school employees. “This delay conveys a profound disregard for the responsibility the district has to the stakeholders and community to keep their information secure or at the minimum provide us with the information in a timely manner, so that at the very least, individually we could take measures to best protect ourselves.”
Students echoed that sentiment in a January 2024 newspaper editorial, noting that while the attack “seems like a distant memory, questions about what caused it still lingered.”
“With students’ private information at stake, the delay in informing the community left students and families confused,” the editorial continued. “In an era of increasing cyber-attacks directed at school sites, such as the one that occurred in the Glendale Unified School District last December, clear communication between the school and its members is necessary to ensure safeguards for the future. Neither the superintendent nor anyone else in his cabinet should worry about what the media will do upon notifying the public immediately. They should worry about offering reassurance to the victims – in a sensitive manner.”
School officials couldn’t be reached for comment.
San Diego Unified School District
Location: San Diego, California
Breach date: October 2022
Info exposed: Names, Social Security numbers, health insurance and banking information
The San Diego, California, school district was the victim of an October 2022 cyberattack, officials acknowledged in a breach notice to state regulators in August 2023 — some 10 months after the incident.
The notice submitted to the California attorney general’s office discloses that the incident exposed victims’ names, Social Security numbers, health insurance and banking information.
In response to an inquiry from The 74, a district spokesperson said officials contacted law enforcement within 24 hours and hired third-party forensics experts to “rapidly shut down the incident as quickly as possible.”
“In the months and years that have followed,” the statement continues, “the district has engaged in a series of security changes and upgrades designed to strengthen the district’s IT system — work that is ongoing.”
Sweetwater Union High School District
Location: Sweetwater, California
Breach date: February 2023
Info exposed: Names, birth dates, Social Security numbers and addresses
When California’s Sweetwater Union High School District fell victim to a cyberattack in February 2023, its computer systems were encrypted and officials found a ransom note on dozens of servers and printers. To resolve the attack, the district paid the hackers a $175,000 ransom.
The payment, uncovered in a television news investigation, didn’t prevent a data breach involving more than 22,000 people, outcry from upset teachers or a class action lawsuit.
The cyberattack occurred after the district was “negligent or reckless” in securing students’ sensitive information, the July 2023 complaint alleges. Sweetwater then “failed and refused to fully and adequately notify victims” that their sensitive information was stolen, the complaint charges, leaving them “in the dark” about what they should do to protect themselves in the future.
The district didn’t notify victims that their personal information had been stolen for more than four months, according to a breach notice submitted to the California attorney general’s office in June 2023. The months-long delay “hardly seems to be with all deliberate speed,” attorney April Strauss, who represents the anonymous educator in the lawsuit, told The 74. She accused Sweetwater of downplaying the breach “to avoid exacerbating their liability, quite frankly,” in a way that prevents families and educators from being able to “assert their rights more competently.”
After the district initially described the cyberattack as an internet outage, officials quickly found themselves under pressure from residents to share more about what had transpired. During a March 2023 school board meeting a month after the event, angry residents accused the district of being misleading and cagey.
Even if officials did not acknowledge district records were being held for ransom, school counselor Michelle Beale said, school employees knew about the ransomware gang’s demands and had observed an uptick in malicious emails.
“Nothing in this district is confidential,” she said. “Staff knew about the ransomware emails, the ransom being requested” and that threat actors had shared samples of stolen records to prove their hack was successful.
Yet even after experiencing the computer connectivity issues firsthand, she said the district misled the public about the degree to which its servers had been crippled and the speed with which officials jumped into action.
Katina Rondeau, a parent and teacher in the district, questioned whether school officials took appropriate measures to secure sensitive information. For the last decade, she said, district IT officials knew Sweetwater was vulnerable to attack. When she mentioned her son, she began to cry.
“Identity theft happens for little guys, too, that are under 18,” she said.
Resident Kathleen Cheers questioned whether lawyers or public relations consultants had advised district officials to keep quiet.
“What brainiac recommended this?” asked Cheers, who wanted the district to create a presentation within a month outlining how the breach occurred, who “recommended the deceitful description,” a precise account of whose personal information had been stolen and details on the total recovery costs. Cheers addressed her comments to one school board member in particular: a former investigative journalist.
Board member and former journalist Marti Emerald said there’s still “a great deal of sensitivity about this because they’re pending legal issues,” and invited the district’s general counsel and superintendent to respond.
Neither divulged additional information. School officials didn’t respond to requests for comment for this story.
Months later, the June 2023 data breach notice the district submitted to state regulators failed to disclose publicly the specific records that were stolen. An “unauthorized party took some files from our network,” it states, and after reviewing “the files that may have been taken,” it determined that “your personal information was included in the potentially taken files.”
Strauss, the lawyer in the class action lawsuit, said the notice’s use of “hedge words” only served to further confuse breach victims.
“Well, was my information taken or not?” she asked in an interview with The 74. “The wording in notices is disheartening. It’s almost like revictimization.”
Lodi Unified School District
Location: Lodi, California
Breach date: October 2021
Info exposed: Names, Social Security and driver’s license numbers, financial information, login credentials and medical records
The Lodi, California, school district was the subject of an October 2021 cyberattack, according to a breach notice submitted to state regulators the following month.
The incident leaked the sensitive information of an undisclosed number of people, including their names, employees’ Social Security numbers and medical records.
A second breach notice, submitted to the California attorney general’s office in January 2022, was sent to victims after officials tracked down their contact information.
“We are therefore sending follow up communications to that limited group in order to ensure all potentially impacted individuals are made aware of this incident,” officials wrote in the notice.
In response to an inquiry from The 74, the district said in a statement an investigation confirmed on Oct. 13, 2021, that “a limited amount of information may have been accessed during this incident,” and it sent breach notice to affected individuals.
“Please note that student Social Security numbers were not impacted by this incident,” the district said in the statement. “The District notified the FBI and any applicable state regulators of this incident.”
Visalia Unified School District
Location: Visalia, California
Breach date: May 2021
Info exposed: Email addresses, driver’s license numbers, banking and health insurance information
The Visalia, California, school district acknowledged in a Dec. 30 2021 letter to data breach victims that district “email accounts were accessed without authorization” — half a year earlier.
The incident occurred between January and June 2021, according to the letter submitted to the California attorney general’s office. The letter didn’t disclose that the breach was the result of a cyberattack or the types of sensitive information that had been accessed.
However, the Visalia Times-Delta revealed in an investigative report the Ryuk ransomware gang had carried out an attack on the district in May 2021. A law firm working on behalf of the school system acknowledged the incident exposed students’ email addresses and for a limited number of people — about a dozen in total — their driver’s license numbers, banking and health insurance information.
School officials couldn’t be reached for comment.
Louisiana Special School District
Location: Baton Rouge, Louisiana
Breach date: May 2024
Info exposed: Names, addresses, Social Security numbers and medical information
Threat actors with the Akira ransomware gang lobbed a cyberattack in May 2024 on the Louisiana Special School District in Baton Rouge, Louisiana, which serves children with disabilities. Exposed information included names, addresses, Social Security numbers and medical information.
School officials couldn’t be reached for comment.
Concord Public Schools
Location: Concord, Massachusetts
Breach date: April 2024
Info exposed: Financial records, Social Security numbers, names and addresses
An April 2024 cyberattack on the Concord, Massachusetts, school district, exposed the sensitive records of more than 1,400 people, including their Social Security numbers and bank account information.
The district reported the data breach to Massachusetts regulators in May and to officials in Maine in June.
School officials couldn’t be reached for comment.
Scranton School District
Location: Scranton, Pennsylvania
Breach date: March 2024
The Scranton, Pennsylvania, school district was the victim of a ransomware attack, school officials acknowledged in a March 2024 statement.
In the aftermath of the attack, officials said they alerted the FBI. Officials declined to comment on whether the incident led to a breach of sensitive student information or if hackers sought a ransom, citing an ongoing investigation.
In late September, some six months later, district officials said they paid $100,000 to a forensics expert — and a $25,000 ransom.
It remains unclear whether the incident led to a data breach. School officials couldn’t be reached for comment.
The Peddie School
Location: Hightstown, New Jersey
Breach date: December 2023
Info exposed: Names and Social Security numbers
The Peddie School in Hightstown, New Jersey, fell victim to a cyberattack by the Cl0P ransomware gang, which listed the school on its leak site in February 2024. The private boarding and day school disclosed a data breach in a notice to regulators in Maine and Vermont.
In the breach notice to the Maine attorney general’s office, the school disclosed that 520 people lost sensitive information in the breach, which was the result of a December 2023 “hacking” incident. Regulators weren’t notified until May 2024 — five months after the attack unfolded.
Names and Social Security numbers were included in the stolen documents, the school disclosed in a letter written by attorneys at the law firm Mullen Coughlin.
School officials couldn’t be reached for comment.
Pulaski County Public Schools
Location: Pulaski, Virginia
Breach date: November 2023
Info exposed: Names, driver’s license and Social Security numbers, addresses and medical records
The Pulaski, Virginia, school district announced in a November 2023 Facebook post that they were the victim of a ransomware attack and had hired “some of the country’s leading experts in cybersecurity” to respond.
A month later, the district submitted its breach notices to victims to state regulators in Massachusetts, disclosing that the breach exposed names, driver’s license and Social Security numbers, addresses and medical records.
During a December 2023 school board meeting, district IT staff were recognized for their efforts to combat the hackers, according to a post on the district website.
“Fortunately, we successfully prevented the ransomware from compromising the physical security of our classrooms or otherwise disrupting the ongoing learning of our students,” according to the post, which acknowledges that the hackers were able to steal “certain data from our servers.”
“Generally, when this happens to school systems, they have to close for an extended period of time,” the post continues. “Pulaski County Schools did not have to do that.”
School officials couldn’t be reached for comment.
Pulaski Academy
Location: Little Rock, Arkansas
Breach date: April 2024
Threat actors with the group Inc Ransom claimed in April 2024 that it had carried out a cyberattack on Pulaski Academy in Little Rock, Arkansas.
The 74 didn’t identify additional information about the incident. School officials couldn’t be reached for comment.
Meredosia Chambersburg School District
Location: Meredosia, Illinois
Breach date: November 2023
School officials in Meredosia, Illinois, announced in 2023 that they fell victim to a ransomware attack. Employees’ computer monitors went dark and district leaders were emailed a ransom note.
School officials couldn’t be reached for comment.
Hermon School Department
Location: Hermon, Maine
Breach date: November 2023
Info exposed: Student names, birth dates, photographs, addresses, phone numbers and Social Security numbers
The superintendent told the Bangor Daily News he was in a “holding pattern” as he waited for a law firm to instruct the district on what information it could share about the attack. He said Hermon didn’t pay a ransom and that the breach appeared to be limited to directory information like names and addresses.
The Hermon, Maine, school district was hit by a ransomware attack in November 2023, according to a district report, and the attack was resolved “quickly” by a third-party cybersecurity firm.
A district investigation concluded the cyberattack leaked students’ names, identification numbers and evaluations, according to Fox 22. An investigation found the breach included data stored on a cloud-based server maintained by PowerSchool, an education technology company. Parents responded with anger, arguing the breach was far more extensive than what officials disclosed.
“PowerSchool holds kids’ pictures, their birthdays, their address, the parents’ phone number, potentially their Social Security number,” one parent told the news outlet.
School officials couldn’t be reached for comment.
Newfound Area School District
Location: Bristol, New Hampshire
Breach date: November 2023
The Bristol, New Hampshire, school district announced it was the victim of a ransomware attack in November 2023 but that a hacker never demanded any money.
Officials with a third-party cybersecurity firm said during a school board meeting that it found no evidence the incident breached any personally identifiable information.
School officials couldn’t be reached for comment.
Bayonne Board of Education
Location: Bayonne, New Jersey
Breach date: November 2023
Info exposed: Social Security numbers
Threat actors with the LockBit ransomware group posted the Bayonne, New Jersey, school district to its dark web leak site in December 2023.
A breach notice filed with the Maine attorney general’s office suggests the district waited more than six months to inform the community that the attack prompted a data breach. Filed by an attorney with the law firm McDonald Hopkins, the June 2024 notice states that a “hacking” incident in November 2023 exposed an undisclosed number of victims’ Social Security numbers.
School officials couldn’t be reached for comment.
Central Catholic High School of Lawrence
Location: Lawrence, Massachusetts
Breach date: January 2024
Info exposed: Social Security numbers
The Central Catholic High School of Lawrence in Massachusetts was the victim of a cyberattack in January 2024, according to a breach notice submitted to state regulators in Maine.
The “hacking” incident unfolded in January 2024, the breach notice states, and 574 people were notified in May 2024 that their Social Security numbers had been exposed.
School officials couldn’t be reached for comment.
Newton Public Schools
Location: Newton, Kansas
Breach date: March 2023
Info exposed: Names, Social Security and driver’s license numbers, financial and health insurance information; login credentials, birth dates and medical records
The Newton, Kansas, school district was forced to cancel classes for two days in March 2023 due to what officials called a “network security incident.”
“It appears no staff nor student data was compromised,” the district told local news outlet KSN. A data breach notice filed in Maine and on the district’s website — one year later — revealed otherwise. The “hacking” incident, according to the Maine notice submitted by the law firm McDonald Hopkins in March 2024, exposed the sensitive information of 10,545 people.
The records encompassed names, Social Security and driver’s license numbers, financial and health insurance information, login credentials, birth dates and medical records.
School officials couldn’t be reached for comment.
Bethel School District
Location: Spanaway, Washington
Breach date: February 2024
Info exposed: Names, Social Security numbers
The Bethel School District in Spanaway, Washington, was the victim of a February 2024 cyberattack — but didn’t notify the public for more than a month.
“Someone’s private information is very, very important,” one district parent, who said she received a letter about the breach at the end of March, told KOMO News.
Other parents and district employees told the news outlet they were the victims of identity theft when a malicious actor opened credit cards in their name — refuting a district breach notice that claimed officials were “unaware of misuse of information related to this event.”
A data breach notice filed in Maine and Washington offered insight into the extent of the attack. According to the March 2024 notice, filed on letterhead from the law firm Mullen Coughlin, the “hacking” incident exposed the names and Social Security numbers of 28,844 people.
School officials couldn’t be reached for comment.
Alliance College Ready Public Schools
Location: Los Angeles, California
Breach date: September 2023
Info exposed: Names, Social Security and driver’s license numbers, and medical records
Alliance College Ready Public Schools, a network of charter schools in Los Angeles, was the victim of a cyberattack in September 2023 that exposed the sensitive information of 8,793 people.
Threat actors with the Snatch ransomware gang posted one of its schools, the Alliance Virgil Roberts Leadership Academy, on its leak site a month later.
The charter network didn’t notify data breach victims, however, for five months. In a February 2024 breach notice that attorneys with the law firm Lewis Brisbois Bisgaard & Smith filed with the Maine attorney general’s office, the school network acknowledged the “hacking’ incident exposed individuals’ names, driver’s license and Social Security numbers, and medical records.
Although the incident was reported to regulators in Maine — on the opposite side of the country — a breach notice does not appear to have been submitted to the California attorney general’s office.
School officials couldn’t be reached for comment.
Butte School District
Location: Butte, Montana
Breach date: November 2023
Info exposed: Social Security numbers, names, birth dates, addresses and financial information
The Butte, Montana school district acknowledged in December 2023 that its computer system was infiltrated in a cyberattack a month earlier.
The superintendent told NBC Montana compromised student records and the personal information of some 900 employees, including their Social Security numbers. In a letter submitted that month to the Montana Office of Consumer Protection, the district said the breach also included names, birth dates, addresses and financial information.
In total, 2,658 people were affected in the hacking event, according to a breach notice submitted to the Maine attorney general’s office.
School officials couldn’t be reached for comment.
Des Moines Public Schools
Location: Des Moines, Iowa
Breach date: January 2023
Info exposed: Names, addresses, phone numbers, email addresses, birth dates, medical records, financial and health insurance information and Social Security and driver’s license numbers
After the Des Moines, Iowa, school district was hit by a ransomware attack that canceled classes for two days in January 2023, officials acknowledged there was a data breach.
The district waited six months, however, to tell the public about the types of information that had been compromised. It wasn’t until mid-February that school leaders acknowledged the disruptions were the result of a ransomware event.
“While we assumed from the beginning that this was a ransomware attack, I can confirm that this was, indeed, a ransomware attack,” the district interim superintendent said in an update. “However, as stated previously, this is an ongoing investigation and therefore I cannot provide specific details.”
Though officials said they did not receive a ransom request, the district investigated the attack in partnership with its cyber insurance provider and the FBI, according to the Des Moines Register. One parent told the newspaper that the district left her wondering what had caused the campus closures.
“I would expect to get at least a text OR voice mail regarding something this extreme,” she wrote in a message to the newspaper over social media. “I suppose that the communication systems were affected as well.”
In a June 2023 letter to the Iowa attorney general’s office, the district acknowledged it was a ransomware target that exposed the sensitive records of thousands of people, including their names, addresses, phone numbers, email addresses, birth dates, passports, medical records, financial and health insurance information and Social Security and driver’s license numbers.
In total, the breach leaked the information of 6,669 people, according to a disclosure filed with the Maine attorney general’s office by an attorney with the firm McDonald Hopkins.
In response to an inquiry from The 74, a district spokesperson said “the safety, privacy and trust of our students, staff and community were of utmost importance” in the aftermath of the attack.
On the day of the incident, the district contacted its cybersecurity insurance provider to “mobilize their expert incident response team” and notified the FBI.
“Our legal and insurance teams noted our approach as ‘radically transparent,’ reflecting our dedication to sharing information responsibly,” the statement continued. Still, the spokesperson said Des Moines Public Schools withheld certain details, “such as the nature of the ransomware attack,” to prevent the threat actors from further exploiting the district.
“Throughout the event there were multiple communications of increasing specificity including direct and detailed notification to those impacted.”
Pearland Independent School District
Location: Pearland, Texas
Breach date: November 2022
Info exposed: Names, birth dates, addresses, Social Security and driver’s license numbers, medical records and financial, login and health insurance information
The Pearland, Texas, school district was the victim of a cyberattack in November 2022 that exposed reams of sensitive information about students and district staff, according to a letter that was mailed to parents and employees in June 2023 — some seven months later.
In a video statement in November, the district superintendent told the community an ongoing investigation had found no evidence of a data breach but that “unauthorized actors” who carried out the attack may try to contact them.
Through an investigation being completed by third-party consultants, the superintendent said “we have learned the actors may attempt to contact Pearland ISD’s community as a form of harassment.”
“Should you be contacted by any unknown individual who refers to this incident,” the superintendent said, “please do not engage.”
The data breach was widespread, affecting 55,486 people, according to a June 2023 breach notice submitted to the Maine attorney general’s office by a third-party law firm.
A letter to parents obtained by Click2Houston discloses the range of information that had been stolen, including names, birth dates, addresses, Social Security and driver’s license numbers, medical records and financial, login and health insurance information.
School officials couldn’t be reached for comment.
Collegium Charter School
Location: Exton, Pennsylvania
Breach date: January 2023
Info exposed: Names and Social Security numbers
Collegium Charter School in Exton, Pennsylvania, was the victim of a ransomware attack that exposed Social Security numbers and other sensitive records, according to a breach notice sent to the Maryland attorney general’s office in May 2023.
A similar notice, filed with the Maine attorney general’s office by a lawyer with the firm Lewis Brisbois Bisgaard & Smith noted that the breach had occurred in January 2023 — four months before people were told about the event that exposed their names and Social Security numbers.
School officials couldn’t be reached for comment.
Val Verde Unified School District
Location: Perris, California
Breach date: Between January and May 2022
Info exposed: Names and Social Security numbers
After the Val Verde Unified School District in Perris, California, suffered a ransomware attack between January and May 2022, it brought in outside lawyers — and has sought to withhold details about what happened ever since.
A third-party lawyer hired by the school district cited attorney-client privilege when he declined to provide certain records about the cyberattack to The 74. But other records — including a breach notice to the Maine attorney general’s office and a report to the FBI — make clear that officials waited more than a year to inform thousands of people that their sensitive information had been stolen.
In an interview with The 74 in November 2024, Deputy Superintendent Mark LeNoir said the district notified the FBI and they “take over and you have to be careful sometimes about what you say” during an ongoing investigation because “you won’t really, clearly know the whole extent of things until that’s done.”
“You don’t want to be early out the gate to say something that could be inaccurate,” he said. Asked about the delayed notice to breach victims, LeNoir said “that investigation process takes some time” to ensure what happened and what information may have been taken.
In a notice to the FBI’s Internet Crime Complaint Center, an attorney with the firm Cipriani & Werner said the district “immediately retained” lawyers “to perform a full forensic analysis of the incident.”
The records the district withheld from The 74 citing attorney-client privilege involved bids, contracts and other documents between Val Verde Unified and third-party cybersecurity vendors, including Cipriani & Werner. “Investigative materials” and “any communications” between the district “its insurer, and its insurer’s retained counsel are protected under the tripartite attorney-client relationship,” the lawyer wrote.
An insurance policy obtained by The 74 through a public records request notes the insurance company was on the hook for cyberattack incident response expenses, including a “cyber incident response coach” hired to determine the cause and scope of the attack and a crisis communications firm for “the purpose of protecting or restoring the [district’s] reputation.”
Though the attack unfolded between January and May 2022, data breach victims weren’t notified that they were affected until May 2023, a year later, according to a notice submitted to the California attorney general’s office.
Investigators completed their review of the leaked files in January, according to the letter, but it took until March to locate accurate address information for the victims. The letter was sent out two months after that.
A similar notice submitted to the Maine attorney general’s office by Cipriani & Werner notes that the names and Social Security numbers of 20,333 people were breached.
The school district spent more than $28,000 on ransomware response services between November 2021 and December 2022, according to records included in the GovSpend government procurement database. They include spending on Cipriani & Werner and the consulting firm Charles River Associates. Purchase orders note the payments were for Val Verde Unified’s share of services covered by its insurance provider.
West Babylon Union Free School District
Location: West Babylon, New York
Breach date: July 2022
Info exposed: Names, addresses, driver’s license and phone numbers and students’ English as a New Language designation
The West Babylon, New York, school district fell victim to a ransomware attack in July 2022 that led to a data breach — after district officials initially said sensitive records had been kept secure.
While the district’s computer network was shut down by a “cyber incident,” the superintendent said in a letter to families “we are not aware of any access to student or staff personal information.”
District officials told Newsday that “an ongoing investigation” prevented it from discussing whether they had been the subject of a cyberattack or if it had paid a ransom demand.
The incident came into focus in September 2022, two months later, when the district’s outside attorneys submitted a breach notice in Maine. In total, 9,380 people had their sensitive information exposed, including their names and driver’s license numbers.
A breach notice in Maryland notes the incident exposed guardians’ contact information and students’ English as a New Language designation.
School officials couldn’t be reached for comment.
Shaker Heights City School District
Location: Shaker Heights, Ohio
Breach date: Between September 2021 and January 2022
Info exposed: Names and Social Security numbers
The Shaker Heights, Ohio, school district was the victim of a cyberattack between September 2021 and January 2022, according to a breach notice submitted to state regulators in Maine.
An attorney with the firm McDonald Hopkins submitted the disclosure in May 2022, at least four months after the attack. The “hacking” incident, the report notes, exposed the personal information of 3,725 people, including their names and Social Security numbers.
In response to an inquiry from The 74, Executive Director of Technology John Rizzo said that providing the public “with too much information too early on,” could have compromised an active investigation and lead to the spread of “unsubstantiated information that needs to be walked back later.”
“By not contacting your cyber insurance provider or law enforcement early in the incident response process you risk jeopardizing the ability to file a claim or capture necessary evidence,” Rizzo wrote in a statement. “Perhaps more importantly, you are potentially missing out on valuable cyber response resources and guidance that are provided per your cyber insurance policy or from federal and local law enforcement agencies.”
Bernards Township School District
Location: Basking Ridge, New Jersey
Breach date: April 2021
Info exposed: Financial information
The Bernards Township School District in Basking Ridge, New Jersey, waited a year to inform the public that an April 2021 cyberattack had exposed students’ sensitive information.
In an April 2022 post on the district’s website, officials said personal student data was “removed”during the attack a year earlier but that there was no apparent “misuse” of the information.
A data breach notice submitted to Maine regulators in April 2022 by an attorney with the firm McDonald Hopkins acknowledges that the Spring 2021 attack exposed the financial information of 6,966 people. The notice to Maine regulators claims the district didn’t discover the breach until February 2022.
School officials couldn’t be reached for comment.
Whitefish School District
Location: Whitefish, Montana
Breach date: March 2022
Info exposed: Names, addresses and Social Security numbers
The Whitefish, Montana, school district fell victim to a cyberattack in March 2022, according to a disclosure to state regulators a month later.
The April 2022 breach notice states that an unauthorized user gained access to an employee’s computer “through a social engineering scam,” compromising victims’ names, addresses and Social Security numbers.
A similar breach notice to the Maine attorney general’s office in Maine notes that 1,755 people were affected.
Data from the GovSpend government procurement database show the district hired Mullen Coughlin for “legal work following a cyber incident.”
School officials couldn’t be reached for comment.
Riverhead Central School District
Location: Riverhead, New York
Breach date: November 2021
Info exposed: Social Security numbers, names, addresses and birth dates
The Riverhead, New York, school district fell victim to a ransomware attack in November 2021 — but victims weren’t informed for four months that their information had been stolen.
The sensitive information of 22,050 people was exposed in the attack, according to a March 2022 breach notice submitted to the Maine attorney general’s office by the district’s third-party lawyer. Compromised files include Social Security numbers, names, addresses and birth dates.
“We respectfully pass on discussing our cyber security practices and protocols,” the district said in a statement to The 74.
Monroe Public Schools
Location: Monroe, Michigan
Breach date: June 2021
Info exposed: Social Security numbers
A “sophisticated cyber-security attack” targeted the Monroe, Michigan, school district in June 2021, the district acknowledged. Monroe Public Schools said it hired third-party consultants to investigate the breach and alerted the FBI.
“We cannot say for certain what information or data, if any, has been impacted as a result as our investigation is ongoing,” the district superintendent said in a statement to The Monroe News. “We will reach out to potentially impacted individuals directly, if necessary.”
Seven months later, in January 2022, attorney Dominic Paluzzi of the firm McDonald Hopkins submitted a breach letter on the district’s behalf to the Maine attorney general’s office. In total, 1,201 people had their Social Security numbers breached in the attack, it states.
School officials couldn’t be reached for comment.
Luxemburg-Casco School District
Location: Luxemburg, Wisconsin
Breach date: November 2021
Info exposed: Names, Social Security numbers and financial information
The Luxemburg, Wisconsin, school district fell victim to a cyberattack in November 2021 that exposed the sensitive information of 1,399 people.
The incident was disclosed in a December 2021 breach notice that third-party lawyers filed with the Maine attorney general’s office in Maine, citing that names, Social Security numbers and financial information had been compromised.
School officials couldn’t be reached for comment.
Spotswood Public Schools
Location: Spotswood, New Jersey
Breach date: September 2021
Info exposed: Names, Social Security and driver’s license numbers and financial information
The Spotswood, New Jersey, school district was the victim of a ransomware attack in September 2021, according to a breach notice filed with the Maine attorney general’s office.
The November 2021 breach notice, filed by an attorney with the firm BakerHostetler, discloses that 424 people had their information exposed, including their names, Social Security and driver’s license numbers and financial information.
School officials couldn’t be reached for comment.
Stonington Public Schools
Location: Mystic, Connecticut
Breach date: September 2021
Info exposed: Names, birth dates, mailing addresses, phone and Social Security numbers and health insurance and financial information
When a ransomware attack targeted Stonington Public Schools in Mystic, Connecticut, in September 2021, educators offered reason for optimism.
Less than a week after the hack, the district said in a letter to parents that student data stored on the cloud-based server PowerSchool had not been compromised. The attack, according to The Westerly Sun, had been isolated quickly.
Two months later, in November 2021, the district notified 1,765 people that their personal information had been exposed, according to a breach notice to the Maine attorney general’s office.
Compromised records, the notice acknowledges, include names, birth dates, mailing addresses, phone and Social Security numbers and health insurance and financial information.
School officials couldn’t be reached for comment.
Dallas Independent School District
Location: Dallas, Texas
Breach date: August 2021
Info exposed: Names, Social Security numbers, birth dates and student medical records
A month after an August 2021 cyberattack on the Dallas, Texas, school district — and a year after being warned of its “severe inability” to defend itself against such incursions — district leaders disclosed the breach to the public.
What they didn’t reveal was that the cyberattack was carried out by two students and that the district’s chief information security officer quit his job because of it, according to a WFAA investigation.
“I am afraid the details of the breach will become public at some point, and Dallas ISD will lose credibility,” the cybersecurity chief wrote in a resignation letter obtained by the news outlet. “I am now convinced that Dallas ISD IT cannot keep our data safe.”
Two months later, in an October 2021 breach notice submitted to the Maine attorney general’s office by a third-party lawyer, the district notified 795,497 people that their sensitive information had been compromised. Exposed information includes names, Social Security numbers, birth dates and student medical records.
In response to an inquiry from The 74, a district spokesperson said it is “committed to securing the district’s information and resources.”
“The confidentiality, privacy, and security of information in our care is one of our highest priorities,” the statement continued. “In the event of any cyber incident, the district will follow all federal and state laws and school district policies, and procedures.”
Carmel Clay Schools
Location: Carmel, Indiana
Breach date: February 2021
Info exposed: Names, addresses, medical information and Social Security numbers
The Carmel, Indiana, school district was the target of a cyberattack in February 2021, but thousands of data breach victims weren’t notified for nearly seven months.
In a September 2021 notice to the Indiana attorney general’s office, Carmel Clay Schools acknowledged the breach compromised the personal information of 15,817 people.
An attorney with the law firm Mullen Coughlin submitted a breach notice to the Maine attorney general’s office on the district’s behalf, disclosing the hack exposed names, addresses, medical information and Social Security numbers.
School officials couldn’t be reached for comment.
St. Bernard’s School, Inc.
Location: New York, New York
Breach date: May 2021
Info exposed: Names and Social Security numbers
The private St. Bernard’s School in New York City was the target of a cyberattack in May 2021, according to a breach notice submitted to the Maine attorney general’s office.
The September 2021 notice, submitted to Maine regulators by an attorney with the law firm Lewis Brisbois Bisgaard & Smith four months after the breach, acknowledges the hack disclosed the names and Social Security numbers of 267 people.
School officials couldn’t be reached for comment.
Guilderland Central School District
Location: Guilderland Center, New York
Breach date: April 2021
Info exposed: Names and Social Security numbers
Students in Guilderland Center, New York, were forced into remote learning in April 2021 after the district announced it hired consultants to investigate “technical interruptions.”
School officials acknowledged cybercriminals had encrypted district files, according to NEWS10, but claimed that no sensitive data had been compromised.
A breach notice submitted to the Maine attorney general’s office acknowledges the district was hit by a ransomware attack that exposed the sensitive information of 367 people. The notice letters were sent in August 2021, four months after the breach, and state the attack exposed names and Social Security numbers.
School officials couldn’t be reached for comment.
Rockwood School District
Location: Eureka, Missouri
Breach date: Between April and June 2021
Info exposed: Names, addresses, student records, Social Security numbers and financial information
The Rockwood School District in Eureka, Missouri, was the victim of “a criminal ransomware attack” between April and June 2021 that exposed the sensitive records of thousands of people, school officials acknowledged in a notice to regulators in Maine.
The breach notice was sent to 77,294 victims in August 2021, at least two months after the breach unfolded. Exposed records include names, addresses, student records, Social Security numbers and financial information.
School officials couldn’t be reached for comment.
Clover Park School District
Location: Lakewood, Washington
Breach date: May 2021
Info exposed: Names, addresses, birth dates, Social Security numbers, medical records and financial and health insurance information
The Clover Park School District in Lakewood, Washington, experienced a “system outage,” a district spokesperson told a local television station in May 2021 after a “tipster” sent the news outlet a screenshot of a ransom note.
Weeks later, in early June 2021, threat actors leaked district files, according to KIRO, including sensitive records on educator disciplinary incidents — prompting a district statement that they were “working with third-party specialists to complete our ongoing investigation to determine the full nature and scope of this incident.”
“If we determine that the event impacted personal information,” the statement continued, “we will move as quickly as possible to notify individuals.”
In mid-June 2021, the district sent breach notices to 1,586 people, according to a filing with the Maine attorney general’s office. Exposed records include names, addresses and Social Security numbers.
An October 2021 letter, submitted to the Washington attorney general’s office by an attorney at the law firm Mullen Coughlin, acknowledges the breach was more extensive than previously disclosed. The breach affected an additional 4,398 Washington residents, the letter reveals, and includes their birth dates, medical records and financial and health insurance information.
School officials couldn’t be reached for comment.
Clark County School District
Location: Las Vegas, Nevada
Breach date: August 2020 and October 2023
Info exposed: Student names, pictures, birth dates, home addresses, special education records, Social Security numbers and academic records
After cybercriminals claimed they stole the sensitive information of some 200,000 students in an October 2023 cyberattack on the Las Vegas, Nevada, school district, throwing the country’s fifth-largest school district into a crisis, Clark County’s top information technology official went to Disney World.
Just weeks after hackers leveraged in-your-face tactics in their extortion bid — including direct outreach to Las Vegas parents — Chief Information Officer Marilyn Delmont spent nearly $2,500 in district money to attend a tech conference at the Florida resort, an investigation by the Las Vegas Review-Journal found.
The revelation came after a former district employee claimed in a lawsuit he was subjected to hostility and discrimination when he worked in Clark County’s IT department. Another former district IT official told the newspaper Delmont’s trip to the conference was poorly timed and she was “absent from the district when she was needed most.”
The incident marked the second cyberattack at the Las Vegas school district in just three years.
A separate class action lawsuit, filed in November 2023 by two Las Vegas parents, alleges the district failed to protect students’ sensitive information and should have taken additional proactive steps to prevent the attack from happening in the first place. After Clark County fell victim to a “ransomware attack,” the parents allege, officials failed to acknowledge the data breach and that the hacker known as SingularityMD “may still have access to all of the District’s information.”
In June, a Clark County judge denied the district’s motion to dismiss the lawsuit.
When district officials first acknowledged that something was up, they told the public of a “cybersecurity incident impacting its email environment.” The attack was distinct from the ransomware attacks often leveraged against school districts, with the threat actor claiming it used weak passwords — in this case students’ birth dates — and flimsy Google Workspace file-sharing practices to gain access to reams of sensitive files, including students’ special education records.
For years, the 325,000-student district reportedly reset all students’ passwords to their birth date at the beginning of each academic year. Hackers claim they learned about, and exploited, the password policy to gain access to its systems.
As parents accused Clark County of failing to disclose key details about the attack and its impact on them and their children, much of the information being revealed about the extent of the data breach came directly from the hackers.
The hackers used the email address of a California student’s compromised email account as a “burner” to contact Las Vegas data breach victims directly in a bid to publicize the breach and coerce a district payment,
Among those who received such direct outreach was Brandi Hecht, a mother of three who woke up to an alarming email purporting to be from the California student whom she’d never met.
“I’m sorry to tell you this but unfortunately your private information has been leaked,” read the email, including attached PDFs with her daughters’ names, photographs and the home address where they’d just spent the night asleep. Some 200,000 similar student profiles had been exposed, the threat actor claimed.
The incident was the second cyberattack on the Clark County district in the last several years. Just three days after schools reopened for pandemic-era in-person learning in August 2020, it fell victim to a ransomware attack. Hackers released reams of sensitive information, including Social Security numbers and other sensitive student files, after the district did not pay a ransom demand,
After a Wall Street Journal investigation outlined the 2020 breach, school officials said they would notify breach victims individually and that the district “values openness and transparency and will keep parents, employees and the public informed as new, verified information becomes available.”
School officials couldn’t be reached for comment.
Fairfax County Public Schools
Location: Fairfax, Virginia
Breach date: Between August and September 2020
Info exposed: Social Security numbers, health insurance information, birth dates and addresses
When threat actors with the Maze ransomware group claimed a cyberattack on the Fairfax, Virginia, school district, educators acknowledged in a statement — since removed from its website — that it had been hacked.
“We currently believe we may have been victimized by cyber criminals who have been connected to dozens of ransomware attacks in other school systems and corporations worldwide,” the district said in September 2020, and that sensitive records had been exposed.
Four months later, in January 2021, Fairfax Public Schools submitted a breach notice to the Maine attorney general’s office, acknowledging the hack had unfolded between August and September 2020 and had exposed the sensitive records of 172,128 people. Information posted to the dark web, the notice states, includes Social Security numbers, health insurance information, birth dates and addresses.
“In this case, a sophisticated group of cyber criminals, known as the Maze group, is claiming responsibility for the attack,” officials wrote in the notice. “In the midst of the challenges associated with virtual learning and the pandemic, cyber criminals have targeted educational systems around the country in an attempt to disrupt their operations.”
School officials couldn’t be reached for comment.
Perth Amboy School District
Location: Perth Amboy, New Jersey
Breach date: Between April and June 2020
Info exposed: Names and Social Security numbers
The Perth Amboy, New Jersey, school district was the target of a “phishing incident” between April and June 2020 that exposed thousands of sensitive records, officials acknowledged in a breach notice to regulators in Maine.
At least seven months after the attack, in January 2021, attorney Dominic Paluzzi of the firm McDonald Hopkins submitted the breach notice on the district’s behalf acknowledging that the sensitive records of 3,872 people had been exposed. Hackers gained unauthorized access “to a limited number of Perth Amboy employees’ email accounts,” according to the letter to breach victims, that gave hackers access to their Social Security numbers.
School officials couldn’t be reached for comment.
Mascoutah School District 19
Location: Mascoutah, Illinois
Breach date: October 2020
Info exposed: Financial information
The Mascoutah, Illinois, school district was the target of a cyberattack in October 2020, according to a breach notice submitted to regulators in Maine.
Three months later, in January 2021, the district notified 1,383 people their financial information had been stolen.
School officials couldn’t be reached for comment.
Canterbury School
Location: Fort Myers, Florida
Breach date: May 2020
Info exposed: Financial information
The Canterbury School in Fort Myers, Florida, was the victim of a cyberattack in May 2020, according to a breach notice submitted to regulators in Maine.
The “hacking” incident, the district reported seven months later — in December 2020 — exposed the financial information of 2,922 people.
School officials couldn’t be reached for comment.
Columbus City Schools
Location: Columbus, Ohio
Breach date: February 2020
Info exposed: Social Security numbers
The Columbus, Ohio, school district fell victim to a phishing attack in February 2020, according to a breach notice submitted to the Maine attorney general’s office.
The incident was reported eight months later — in October 2020 — in a breach notice submitted to Maine regulators by an attorney with Lewis Brisbois Bisgaard & Smith. In total, 3,178 people had their sensitive information exposed, including their Social Security numbers.
The government procurement database GovSpend reveals the district spent $472,000 between September 2022 and July 2024 for cybersecurity incident services, including to the consulting firm Charles River Associates and the law firm BakerHostetler.
School officials couldn’t be reached for comment.
Indianapolis Public Schools
Location: Indianapolis, Indiana
Breach date: January 2020
Info exposed: Financial information
It was a Sunday morning in spring 2020, just months after the pandemic forced schools nationwide into online-only instruction, when school district technology leadership in Indianapolis, Indiana, got a “ping.”
In a case study for the education technology company PowerSchool, the district’s director of student information systems explained how a bot pinged the district server, which was hosted on-premises, every five minutes. The pinging was an alert to officials that the district had become the target of a ransomware attack, allowing them to respond quickly, he said. The district turned to PowerSchool, the case study notes, “as soon as IPS staff discovered that their server drives had been wiped clean by a cybersecurity breach.”
“Literally within two hours, we were [back] up in an emergency cloud-hosted server based on the Saturday morning data pull,” the district cybersecurity official said in the post. Though district officials never identified the source of the ransomware attack, it cost the district millions of dollars, according to the case study.
The case study and data breach notices submitted to state regulators nationwide make clear the ransomware attack struck the district around the same time the Indianapolis school district experienced a massive data breach. But when The 74 reached out for records on the attack — including insurance claims, law enforcement reports and public notices — district officials claimed the ransomware attack never happened.
“The incident was not a ransomware attack or a breech (sic.) in information,” the district told The 74, adding that an internal and external review by a third-party cybersecurity firm validated that nothing had been taken from the system.
In January 2020, a data breach exposed the personal information of 20,942 people, according to a breach notice the district submitted to the Indiana attorney general’s office in December 2020 — nearly a year later.
A similar notice was submitted to the Maine attorney general’s office, which discloses a “hacking” incident targeting the school district between January and May 2020 exposed people’s financial information.
A breach notice submitted to New Hampshire regulators includes letterhead for the law firm Mullen Coughlin. In August 2020, the district paid the firm Charles River Associates $905,000 for “cyber security incident response services,” according to records maintained by the government procurement database GovSpend.
Though the school district declined to fulfill some public records requests related to the cyberattack, including reports to federal law enforcement officials and specific cybersecurity vendors, officials furnished copies of Indianapolis Public Schools’ cyber insurance policies. In 2020, the district paid a premium of about $40,000, records show. A year later, the premium doubled to nearly $80,000.
Springfield Public Schools
Location: Springfield, Massachusetts
Breach date: October 2020
Info exposed: Financial information
At the height of the pandemic, the Springfield, Massachusetts, school district was forced to pause remote learning when it was hit by a ransomware attack — one the district told the press in October 2020 was a new virus undetected by firewalls or the police.
Two months later, in December 2020, Springfield hired a third-party law firm to notify the Maine attorney general’s office of the breach, which exposed the financial account information of more than 1,000 people.
School officials couldn’t be reached for comment.
Toledo Public Schools
Location: Toledo, Ohio
Breach date: September 2020
Info exposed: Students’ and parents’ names; addresses, phone numbers, Social Security and driver’s license numbers; special education records and student demographic and financial information
A September 2020 cyberattack on the Toledo, Ohio, school district carried out by threat actors with Maze Cartel led to a massive data breach — exposing to the dark web reams of sensitive information, including students’ Social Security numbers and records about children in foster care.
In a statement to 13abc, which published an investigation into the breach, the district said it notified “our legal team and cyber security experts to investigate the full scope of the incident” and that it would “follow all processes as required by law.”
Three months after the attack, in December 2020, Toledo Public Schools acknowledged the breach exposed the financial records of 66,280 people. A sample notice submitted to the Maine attorney general’s office states the breach disclosed a wide range of personally identifiable information, including students’ and parents’ names; addresses, phone numbers, Social Security and driver’s license numbers; special education records and student demographic and financial information.
School officials couldn’t be reached for comment.
Panama-Buena Vista Union School District
Location: Bakersfield, California
Breach date: January 2020
In the first week of January 2020, the school district in Bakersfield, California, was the target of a ransomware attack, telling parents a week later there was no evidence the hack exposed any personal information.
School officials couldn’t be reached for comment.
Mountain View Los Altos Union High School District
Location: Los Altos, California
Breach date: January 2020
California’s Mountain View Los Altos Union High School District was the victim of a ransomware attack in January 2020, which district officials told the Los Altos Town Crier, has “not been a terrible disruption to our teaching and learning.”
The district said hackers didn’t appear to gain access to sensitive information but they were working with their cybersecurity insurance provider and consultants with Kroll to investigate the breach.
Deciding whether to pay the hackers a ransom, the district’s IT director said, would be up to district leaders “based on the advice that Kroll will be giving us.”
In response to an inquiry from The 74 in November 2024, Superintendent Eric Volta said the school system did not pay a ransom “and as far as anyone knows no data was shared.”
Crystal Lake School District 155
Location: Crystal Lake, Illinois
Breach date: January 2020
The Crystal Lake, Illinois, school district was the target of a ransomware attack in January 2020 — and within a week school officials announced they had launched an investigation with third-party consultants “immediately,” and that sensitive information had not been exposed.
School officials couldn’t be reached for comment.
Carpinteria Unified School District
Location: Carpinteria, California
Breach date: January 2020
The school district announced in January 2020 it would submit an insurance claim after a ransomware attack that temporarily shut down its computer network caused $90,000 in damages.
School officials couldn’t be reached for comment.
Spartanburg School District 1
Location: Campobello, South Carolina
Breach date: February 2020
The Campobello, South Carolina, school district was the victim of a cyberattack in February 2020 that shut down computers for three days — and although there was no reported data breach, the system faced criticism for its delayed notice to the public.
Officials “didn’t think it was necessary to notify parents” of the attack, according to an article in the local news outlet GoUpstate. Spartanburg schools determined that no personal information had been compromised, saying it was therefore not necessary to notify families about what had happened.
“The biggest thing was inconvenience,” a district spokesperson said. “It was inconvenience more than anything.”
School officials couldn’t be reached for comment.
South Adams Schools
Location: Berne, Indiana
Breach date: February 2020
The South Adams School District in Berne, Indiana, acknowledged it was the victim of a ransomware attack in February 2020.
School officials couldn’t be reached for comment.
Nacogdoches Independent School District
Location: Nacogdoches, Texas
Breach date: February 2020
The Nacogdoches, Texas, school district was the victim of a ransomware attack in February 2020 that locked officials out of files.
But the hackers, the district said in a news release, did not gain access to any sensitive information.
In response to an inquiry from The 74, officials said in a statement they notified stakeholders about the ransomware attack the same day it unfolded, and that the FBI assisted.
Havre Public Schools
Location: Havre, Montana
Breach date: February 2020
The Havre, Montana, school district announced in February 2020 its computer system had been “crippled” by a ransomware attack carried out by Ryuk cybercriminals.
Hackers were ultimately unable to gain access to sensitive information, the district superintendent told the Havre Herald.
School officials couldn’t be reached for comment.
Sheldon Independent School District
Location: Houston, Texas
Breach date: March 2020
Info exposed: Names and Social Security numbers
The Sheldon Independent School District in Houston paid threat actors a ransom of more than $200,000 after it suffered a ransomware attack in March 2020.
The district’s insurance company contributed another $100,000 for a total of $306,931 to cover the ransom demand, district officials told ABC13.
“After consulting with state and federal entities and our cybersecurity firm, paying was the best option to continue district operations effectively,” the district said in a statement.
While paying the ransom may have allowed the school district to resume business as normal, records suggest it didn’t prevent a breach of sensitive records.
A July 2020 data breach notice was submitted to state regulators in Massachusetts.
The letter, which was sent to data breach victims four months after the attack, notes the incident exposed names and Social Security numbers.
School officials couldn’t be reached for comment.
Mitchell County Public Schools
Location: Bakersville, North Carolina
Breach date: March 2020
Mitchell County Public Schools in Bakersville, North Carolina, announced in March 2020 it was the victim of a cyberattack — but that no personal information was exposed in the hack.
The district superintendent told the Mitchell News-Journal that pending investigations by federal law enforcement and third-party contractors prevented school officials from sharing specific information about the incident.
School officials couldn’t be reached for comment.
Fort Worth Independent School District
Location: Fort Worth, Texas
Breach date: March 2020
The Fort Worth, Texas, school district acknowledged in March 2020 it was the victim of a ransomware attack — but it refused to pay the hackers.
A district spokesperson told KERA News that third-party contractors hired to investigate the incident hadn’t identified a breach of sensitive information.
School officials couldn’t be reached for comment.
Burke County Public Schools
Location: Morganton, North Carolina
Breach date: March 2020
The Morganton, North Carolina, school district announced in March 2020 it was the target of a ransomware attack — but that pending investigations by the police and third-party consultants prevented it from sharing details about what happened.
School officials couldn’t be reached for comment.
Surry County Schools
Location: Dobson, North Carolina
Breach date: July 2020
Surrey County Schools in Dobson, North Carolina, was the target of a ransomware attack in July 2020 that caused “some inconveniences,” it announced in a press release.
“Due to the nature of the investigation, we are not allowed to share specific details regarding the attack,” it states. “However, at this time, we have no indication that any sensitive data was accessed inappropriately.”
School officials couldn’t be reached for comment.
Somerset Berkley Regional School District
Location: Somerset, Massachusetts
Breach date: July 2020
Info exposed: Social Security numbers, driver’s license numbers and credit card numbers
When a ransom note landed in the inboxes of high school leaders in Somerset, Massachusetts, the district hired consultants to negotiate — unsuccessfully — with the hackers.
The district wound up paying a ransom to resolve the July 2020 cyberattack, according to documents obtained by The 74 through public records requests. In the eyes of the cybersecurity company, the school system got a good deal.
The hacker, who used an encrypted email service and the name Kristina D Holm, threatened to leak 50 gigabytes of data if the district didn’t hand over 60 bitcoin which, at the time, was worth about $660,000.
“If we don’t reach an agreement we will start leaking your private data,” the hacker wrote, noting that for bitcoin they would offer “a list of security measures” to prevent future breaches. The note also provided documents to prove the writer had infiltrated district servers.
Emails reveal that Coveware, a cybersecurity company that specializes in negotiating with hackers, got the ransom down to $200,000 after the firm made a $170,000 counteroffer. An invoice obtained by The 74 describes the ransom payment as being for “technical consultant services and remediation.”
“Typically in situations where they drop very significantly and within range of our budget, we would recommend accepting the offer as we have seen these groups take offers away if they think we are nickel and diming them on the price,” Coveware incident response director Garron Negron wrote in a July 30 email ahead of the payment.
The district didn’t respond to requests for comment for this story.
Records show that Beazley, the school district’s cybersecurity insurance provider, approved the ransom payment and was a key player in selecting third-party vendors like Coveware for Somerset Berkeley’s incident response.
Six days after the attack, school officials contacted lawyers with the firm BakerHostetler to assess the cyberattack’s impact and its data breach reporting obligations, but it wasn’t until November — four months later —that the firm told them a “programmatic review of the files” had been completed.
“Baker reviewed a sample of documents for each of the largest hit counts and helped narrow the scope for manual review,” staff attorney Damon Durbin wrote, adding that the preliminary review uncovered at least two Social Security numbers. Once the district approved a statement of work, Durbin wrote, consultants would “conduct the review and produce a notification list that Baker will review with the District in order to determine notification obligations.”
The school district reported the hack to local and federal law enforcement, records show, but not until after lawyers were on the scene.
William Tedford, then the Somerset Police Department’s technology director, requested in a July 31 email that the district furnish the threat actor’s bitcoin address “as soon as possible,” so he could share it with a Secret Service agent who “offered to track the payment with the hopes of identifying the suspect(s).”
“There will be no action taken by the Secret Service without express permission from the decision-makers in this matter,” Tedford wrote, adding that officials with the state police cybersecurity program had also offered to help.
“All are aware of the sensitive nature of this matter, and information is restricted to only [the officers] directly involved,” said Tedford, who was promoted to department chief in August 2024.
While law enforcement seemed willing to follow the school district’s lead, the incident did open the Somerset Berkeley to police scrutiny. In early August, Tedford pressed school officials about sexual misconduct allegations that the threat actor claimed to have stumbled upon and attempted to use as leverage during ransom negotiations.
The hacker wrote: “I am somewhat shocked with the contents of the files because the first file I chose at random is about a predatory/pedophilia incident described by young girls in one of your schools. This is very troubling even for us. I hope you have investigated this incident and reported it to the authorities, because that is some fucked up stuff. If the other files are as good, we regret not making the price higher.”
Tedford asked if the accusation was legitimate and if the police had been notified.
“I need to cover these bases now that we have been made aware of this claim,” Tedford wrote in an Aug. 3 email. “It’s clear the attorneys don’t want law enforcement involved, and that’s fine, but this is a different issue.”
In an emailed response, district Superintendent Jeffrey Schoonover said the police department is “well aware of that situation,” which was related to an incident during an out-of-town show choir event.
“After a thorough investigation, no charges were filed,” Shoonover wrote, adding in a later email that an officer “interviewed dozens of kids” in response to “this entire unfortunate event.”
In August 2020, the district was working on its talking points to the public and it’s clear the consultants weren’t far away. The 74 obtained a draft FAQ in which school officials were crafting their answer to the question: Why was the community not advised when this cyberattack first happened?
They answered that they would “have preferred to notify the public earlier” but couldn’t “to ensure the privacy of student records,” that they were unsure what, if any, records may have been compromised and that they were encouraged to “wait to release any information until the investigation” was further along. In red italics next to the text are the words: Pending revisions from consultants.
Somerset Berkley was “unable to provide any further information” about whether the district paid a ransom, the document also notes.
The public wasn’t notified of the July attack until September, when Schoonover wrote in a letter that data breach victims would be contacted once its investigation was finalized — but he didn’t divulge the $200,000 ransom payment.
The district submitted a breach notice to Massachusetts regulators in December 2020 — five months after the incident — and disclosed that 85 commonwealth residents had their information exposed. Stolen records include Social Security, driver’s license and credit card numbers.
Athens Independent School District
Location: Athens, Texas
Breach date: July 2020
The Athens, Texas, school board agreed to pay $50,000 to threat actors to resolve a July 2020 ransomware attack.
The attack blocked access to data on encrypted district servers, KETK reported, but no sensitive information was taken, district officials said.
“We can’t afford to not pay it,” school board President Alicea Elliott said during a July 2020 board meeting. “It would take us months to rebuild all that data so that we could start school.”
School officials couldn’t be reached for comment.
Selma Unified School District
Location: Selma, California
Breach date: August 2020
The Selma, California, school district was hit with an overnight ransomware attack in August 2020, district officials announced in a statement, but the threat actors “do not appear to have stolen any data.”
School officials couldn’t be reached for comment.
Rialto Unified School District
Location: Rialto, California
Breach date: August 2020
The Rialto, California school district was the victim of an August 2020 cyberattack that forced officials to suspend remote classes for more than 25,000 students.
School officials couldn’t be reached for comment.
Ponca City Public Schools
Location: Ponca City, Oklahoma
Breach date: August 2020
The Ponca City, Oklahoma, school district was the target of an August 2020 ransomware attack that delayed the first day of the new academic year. Data was encrypted, officials said, but sensitive information wasn’t exposed.
School officials couldn’t be reached for comment.
Haywood County Schools
Location: Waynesville, North Carolina
Breach date: August 2020
Info exposed: Sensitive student and teacher records
A ransomware attack forced the Waynesville, North Carolina, school district to cancel remote learning in August 2020 — right at the start of a new pandemic-era academic year.
Threat actors with SunCrypt Ransomware took credit for the attack, according to Bleeping Computer, an online news site that covers cybersecurity and provides tech advice. The hackers published 5 gigabytes of data, including sensitive records about students and teachers, when the district didn’t pay the ransom.
“As a school system that works to be transparent, it can be difficult to share disturbing news,” the district said in a Sept. 1, 2020 post on its website, which was archived but has since been removed. “In announcing the ransomware attack on Monday, we wanted everyone to understand a data breach was possible. We have now confirmed a data breach occurred.”
However, the post didn’t disclose what type of information was taken. School officials couldn’t be reached for comment.
Gosnell School District
Location: Gosnell, Arkansas
Breach date: August 2020
The Gosnell, Arkansas, school district announced in August 2020 it was the victim of a ransomware attack, but officials said they didn’t believe the incident led to a data breach.
School officials couldn’t be reached for comment.
Somerset Hills School District
Location: Bernardsville, New Jersey
Breach date: September 2020
The Somerset Hills School District in Bernardsville, New Jersey, canceled classes in September 2020 due to what it described as an “unexpected network disruption,” but acknowledged was the result of ransomware.
Attackers were able to “encrypt a very limited portion of the network,” the district reported, and there was “no evidence of any information being exfiltrated from our network or misused by the threat actor.”
School officials couldn’t be reached for comment.
Skidmore-Tynan Independent School District
Location: Skidmore, Texas
Breach date: September 2020
The Skidmore, Texas, school district was forced to cancel classes in September 2020 after it suffered “network issues due to a cyberattack of unknown origin,” leaders said in a letter to parents.
Any breach of sensitive information appeared to be limited, the superintendent told the Caller Times.
School officials couldn’t be reached for comment.
Newhall School District
Location: Valencia, California
Breach date: November 2020
The Newhall School District in Valencia, California, canceled virtual classes in November 2020 after it became the target of a ransomware attack.
School officials couldn’t be reached for comment.
King George County Schools
Location: King George, Virginia
Breach Date: September 2020
Just three days into the new academic year, the King George, Virginia, school district canceled virtual classes after it suffered a ransomware attack.
The district superintendent told the Free Lance Star there was “no indication of any damage or breach of information or data.”
School officials couldn’t be reached for comment.
Hartford Public Schools
Location: Hartford, Connecticut
Breach date: September 2020
The first day of school was postponed in Hartford, Connecticut, in September 2020 after the district fell victim to a ransomware attack.
Then-Mayor Luke Bronin said at a news conference that officials did not believe any personal information was exposed in the attack, according to The New York Times.
School officials couldn’t be reached for comment.
Great Falls Public Schools
Location: Great Falls, Montana
Breach date: September 2020
After a week of computer network outages, Great Falls, Montana, school district officials acknowledged in September 2020 it was the target of a ransomware attack.
Officials cited an active investigation as their reason for withholding information, according to the Great Falls Tribune, including the amount of the ransom demand.
School officials couldn’t be reached for comment.
Floral Park-Bellerose School District
Location: Floral Park, New York
Breach date: September 2020
School district officials in Floral Park, New York, announced in September 2020 the district was the target of a ransomware attack but they had “no reason to believe” any sensitive information was stolen.
School officials couldn’t be reached for comment.
Yorktown Central School District
Location: Yorktown, New York
Breach date: October 2020
The Yorktown, New York, school district fell victim to a cyberattack in October 2020, district officials acknowledged, but there was no evidence of a data breach.
School officials couldn’t be reached for comment.
Yazoo County School District
Location: Yazoo City, Mississippi
Breach date: October 2020
The Yazoo City, Mississippi, school district paid $300,000 in October 2020 to unlock encrypted files that were the target of a ransomware attack.
District officials said they hired third-party cybersecurity consultants in response and that federal law enforcement officials had been notified.
The superintendent wouldn’t tell news outlet WLBT what information was stolen, however, or why the payment was necessary. Providing such information, the district said, would jeopardize an ongoing investigation.Law enforcement generally advises against paying ransoms, believing it emboldens future attacks.
School officials couldn’t be reached for comment.
Winters Independent School District
Location: Winters, Texas
Breach date: October 2020
Info exposed: Students’ names, birth dates, birth certificates, law enforcement records and Social Security numbers
Threat actors with the Pysa ransomware gang took credit in October 2020 for a cyberattack on the Winters, Texas school district.
The incident exposed a small collection of students’ personally identifiable information, according to a review of the leaked files by DataBreaches.Net, a blog that tracks and reports on data breaches globally. Records included students’ names, birth dates, birth certificates, law enforcement records and Social Security numbers.
School officials couldn’t be reached for comment.
Walled Lake Consolidated School District
Location: Walled Lake, Michigan
Breach date: October 2020
Info exposed: Social Security numbers, students’ login credentials, contact information and birth dates
In a late-night email to parents, district officials in Walled Lake, Michigan, acknowledged in October 2020 their servers were brought down by a cyberattack.
“Attackers were successful in gaining access to our system and that there is the possibility that credential and other information was available to them,” the email states. “Unfortunately, we do not have any specifics at this point.”
Threat actors with the DopplePaymer ransomware gang were responsible for the attack, according to the Detroit Free Press, and the district superintendent wrote in a letter to parents that the “threat actor who perpetrated this incident acted in bad faith and released some personal information of current and former” teachers. But students’ information was not included, the superintendent said.
The leak site, however, included files with Social Security numbers, students’ login credentials, contact information and birth dates, according to the Detroit Free Press.
School officials couldn’t be reached for comment.
Pascagoula-Gautier School District
Location: Pascagoula, Mississippi
Breach date: October 2020
Info exposed: Student data
Threat actors with the DoppelPaymer ransomware gang took credit for an October 2020 cyberattack on the Pascagoula, Mississippi school district.
In a statement on the district website, officials said a joint investigation by the school district and the Mississippi Army National Guard’s cybersecurity unit “determined servers containing financial and child nutrition records were not compromised or extracted.”
“The investigation did determine that a server containing student data was comprised (sic), but did not include any social security numbers,” the district said. “The investigation was inconclusive as to whether any student data was taken or whether other data was taken from the PGSD network, and no ransom was paid.”
School officials couldn’t be reached for comment.
Croton-Harmon School District
Location: Croton-on-Hudson, New York
Breach date: October 2020
School district officials in Croton-on-Hudson, New York, acknowledged in October 2020 that their computer network was compromised by a ransomware attack.
Paying a ransom “was never considered by our district” because it was able to restore its servers from backups, the superintendent said in a letter to parents, and there was no evidence of a data breach.
School officials couldn’t be reached for comment.
Avoyelles Parish School District
Location: Marksville, Louisiana
Breach date: October 2020
School officials woke up to a surprise in October 2020 when the Avoyelles Parish, Louisiana, district fell victim to a ransomware attack.
“Got to work this morning, powered up my computer and the first message I got was you’ve been encrypted,” the superintendent told local news outlet KALB. “Basically, you know, the same old thing … you’ll have to pay us in bitcoin, we’re holding your data ransom, you need to contact this email address. Of course, we didn’t do any of that.”
School officials couldn’t be reached for comment.
Spring Independent School District
Location: Houston, Texas
Breach date: November 2020
Threat actors with the Egregor ransomware gang claimed in November 2020 a cyberattack on Houston’s Spring Independent School District.
The ransomware attack was further disclosed in a case study by the information technology company Cohesity, which states the incident was resolved without paying a ransom and without disruptions to learning or payroll.
School officials couldn’t be reached for comment.
Oglethorpe County School System
Location: Lexington, Georgia
Breach date: November 2020
Classes were canceled for two days in November 2020 just before the Thanksgiving holiday after a ransomware attack focused on the Oglethorpe County School System in Lexington, Georgia. The rural district called in the FBI for help.
School officials couldn’t be reached for comment.
K12, Inc. (Stride, Inc.)
Location: Online
Breach date: November 2020
Info exposed: Student records
The for-profit online learning giant K12 Inc., now known as Stride, Inc, paid a ransom to hackers after falling victim to a pandemic-era ransomware attack.
The company announced the ransom payment in November 2020, Marketwatch reported, stating the payment of an unspecified amount was made with the advice of its insurance provider to prevent information from being released publicly.
“While there is always a risk that the threat actor will not adhere to negotiated terms, based on the specific characteristics of the case, and the guidance we have received about the attack and the threat actor, we believe the payment was a reasonable measure to take in order to prevent misuse of any information the attacker obtained,” K12 said in a statement.
Threat actors with the Ryuk ransomware gang carried out the attack, according to Bleeping Computer, an online news site that covers cybersecurity threats and provides tech advice. The gang was able to gain access to back-office systems with student information.
A K12 representative initially responded to an inquiry by The 74, wanting to know more about the story, but didn’t provide a response.
Huntsville City Schools
Location: Huntsville, Alabama
Breach date: November 2020
Info exposed: Student records, contact information and Social Security numbers
The Huntsville, Alabama, school district was forced to cancel classes in November 2020 after a cyberattack compromised its computer network.
District officials confirmed the incident was a ransomware attack, according to AL.com, and hired third-party cybersecurity consultants to investigate the breach.
A month later, in December 2020, the Huntsville school officials acknowledged that sensitive information was exposed in the attack, including student records, contact information and Social Security numbers.
School officials couldn’t be reached for comment.
Gardiner Public Schools
Location: Gardiner, Montana
Breach date: November 2020
Info exposed: Student special education records
Threat actors with the DoppelPaymer ransomware group carried out a cyberattack in November 2020, on the Gardiner, Montana. school district.
The district said it hired third-party cybersecurity experts to determine if sensitive information was exposed in the attack in a statement to DataBreaches.Net, a blog that tracks and reports on data breaches globally. The district doesn’t appear in a data breach database maintained by the Montana Office of Consumer Protection.
School officials couldn’t be reached for comment.
Weslaco Independent School District
Location: Weslaco, Texas
Breach date: December 2020
Info exposed: Names, birth dates, Social Security numbers, student demographic information and special education records
The Weslaco, Texas, school district announced in December 2020 it was the target of a ransomware attack, which led to a data breach after officials declined to pay a ransom.
“We do not know the extent of the attack, and we are working to contain the threat,” school officials said in a statement.
A report by cybersecurity group, The K12 Security Information eXchange, found a trove of sensitive information had been leaked online.
“One of those files, still posted online, is an Excel spreadsheet titled ‘Basic student information’ that has a list of approximately 16,000 students, roughly the combined student population of Weslaco’s 20 schools last year,” the report noted. “It lists students by name and includes entries for their date of birth, race, Social Security number and gender, as well as whether they’re an immigrant, homeless, marked as economically disadvantaged and if they’ve been flagged as potentially dyslexic.”
School officials couldn’t be reached for comment.
Socorro Independent School District
Location: El Paso, Texas
Breach date: December 2020
The Socorro Independent School District in El Paso, Texas, was the target of a cyberattack in December 2020, and it hired third-party consultants to investigate the breach.
But district officials declined to call the incident a ransomware attack, KVIA reported, and “as of right now, there’s no sign that any data has been compromised.”
School officials couldn’t be reached for comment.
Victor Central School District
Location: Victor, New York
Breach date: January 2021
A ransomware attack in January 2021 forced the school district in Victor, New York, school district to cancel classes, but district officials said “no personal or financial information” was compromised.
School officials couldn’t be reached for comment.
Somerset Independent School District
Location: Somerset, Texas
Breach date: February 2020
Info exposed: Names, special education records, medical and demographic information
Threat actors with the Avaddon ransomware gang took credit in February 2020 for a cyberattack on the Somerset, Texas, school district.
The incident exposed a significant amount of sensitive information online after the attack, including student demographic information that contained their names; medical information and special education records, according to an analysis by DataBreaches.Net, a blog that tracks and reports on data breaches globally.
School officials couldn’t be reached for comment.
Victor Valley Union High School District
Location: Victorville, California
Breach date: February 2021
Info exposed: Names and Social Security numbers
The Victor Valley Union High School District in Victorville, California, was the target of a cyberattack in February 2021 that exposed sensitive information.
Four months later, in June 2021, the district submitted a data breach notice to the California attorney general’s office, disclosing that names and Social Security numbers were compromised in the attack.
School officials couldn’t be reached for comment.
Park Hill School District
Location: Kansas City, Missouri
Breach date: March 2021
The Park HIll School District in Kansas City, Missouri, was forced to cancel classes in March 2021 after it was targeted by a ransomware attack.
District officials, who declined for a week to acknowledge that the disruptions were caused by a ransomware attack, said there was no evidence that sensitive information was stolen.
School officials couldn’t be reached for comment.
Woodlake Unified School District
Location: Woodlake, California
Breach date: April 2021
Info exposed: Social Security numbers, special education records, login credentials, disciplinary records and injury reports
Threat actors with the Pysa ransomware gang took credit for an April 2021 cyberattack on the Woodlake Unified School District in Woodlake, California.
In a Facebook post that month, the district said it notified local and federal law enforcement of the attack and that they were working with third-party cybersecurity consultants on the recovery, according to DataBreaches.Net, a blog that tracks and reports on data breaches globally. Months later, in September 2021, the district appeared on the Pysa ransomware gang’s leak site.
A review of the records turned up reams of sensitive information, including Social Security numbers, special education records, login credentials, disciplinary records and injury reports.
The district doesn’t appear in a database of data breach incidents maintained by the California attorney general’s office. School officials couldn’t be reached for comment.
Hillsborough Township Public Schools
Location: Hillsborough, New Jersey
Breach date: April 2021
Threat actors with the Ryuk ransomware gang claimed an April 2021 cyberattack on the Hillsborough, New Jersey, school district.
In an hour-by-hour account of the attack published in July 2023 on techlearn.com, the district’s technology director explains how educators looped in the police, contacted its insurance provider and decided to cancel in-person classes. With a stable backup of district data, Hillsborough schools didn’t consider paying the ransom, the tech director said.
Still, the attack cost hundreds of thousands of dollars, according to GovSpend government procurement data analyzed by The 74. Among the recovery expenses was $310,000 to Arete Advisors, a cybersecurity firm that specializes in hostage negotiations and that facilitates ransom payments.
School officials couldn’t be reached for comment.
Consolidated High School District 230
Location: Orland Park, Illinois
Breach date: October 2021
Threat actors with the Pysa ransomware gang claimed in October 2021 a cyberattack on the Consolidated High School District 230 in Orland Park, Illinois.
The 74 didn’t identify additional information about the incident. School officials couldn’t be reached for comment.
Centennial School District
Location: Portland, Oregon
Breach date: April 2021
Classes were canceled for two days at the Centennial School District in Portland, Oregon, after the school system fell victim to an April 2021 ransomware attack and its data were “encrypted by an unknown actor.”
Threat actors with the Babuk ransomware gang took credit for the attack, noting on its leak site that “negotiations with another organization from the USA failed.”
“It’s a shame, it’s a shame, you always try to find a workaround and not pay, but it doesn’t work,” the group chastised.
Three months later, in July 2021, the district disclosed the data breach that followed Babuk’s April attack to the state justice department’s consumer protection office.
School officials couldn’t be reached for comment.
Broward County Public Schools
Location: Fort Lauderdale, Florida
Breach date: Between November 2020 and March 2021
Info exposed: Names, Social Security numbers, birth dates, health insurance and employee benefits information
When threat actors with the Conti ransomware gang carried out a cyberattack on the school district in Fort Lauderdale, Florida, between November 2020 and March 2021, officials said they had no plans to pay the extortion demand — and there was no evidence any sensitive information had been leaked.
After demanding a $40 million ransom, the ransomware gang posted reams of sensitive information online, the district acknowledged in notices to data breach victims and federal regulators eight months later.
District staff took steps in the attack’s aftermath to withhold information about what happened from the public, an investigation by the Sun Sentinel found. After leaving his role as district superintendent, Robert Runcie helped write a white paper for a private security company — created by his former Broward County Public School colleagues — on how to respond when “cyber warfare comes to school.” The report outlined response details the district had previously withheld.
Threat actors encrypted 2,000 district servers and more than 150,000 student and staff laptops, according to the Safer School Solutions white paper, which was obtained by the Florida newspaper. But 130,000 other district laptops distributed to students during the pandemic were not affected and were critical to maintaining operations.
The white paper is congratulatory to some extent about how successful Broward County was in keeping the public in the dark for so long.
“By the time the crisis made the national press two months later, nearly all issues had been resolved with no ransom paid to the attackers and relatively minimal impact to the District,” according to the white paper. “Many within the Broward community had no idea of the scope and scale of the attack until myriad public records requests and voluminous press coverage shed light on just how serious it had been.”
At the same time, the report blames an “active criminal investigation underway by multiple law enforcement agencies” for preventing educators from being able to tell their “side of the story” once the public did become aware and controversy ensued.
The district “found itself in the position of trying to do the work to secure students and staff,” the document notes, “while being subject to criticism by those who didn’t have all the facts or information.”
Meanwhile, Broward County waited three weeks to disclose the ransomware attack to employees and parents — after the hackers posted failed ransom negotiations online — and eight months to notify data breach victims and federal regulators that sensitive information had been compromised.
In November 2021, the district announced it would send notices to some 50,000 people that their personal data had been leaked online, including their names, Social Security numbers, birth dates, health insurance and employee benefits information.
District officials disclosed they learned in late June that hackers had gained access to employee’s health insurance information but waited five additional months — until the end of November — to report the breach to state and federal regulators.
School officials couldn’t be reached for comment.
Vicksburg Warren School District
Location: Vicksburg, Mississippi
Breach date: May 2021
A year after threat actors with the Grief ransomware gang took credit for an attack on the Vicksburg, Mississippi, school district, officials acknowledged sensitive records had been stolen.
The ransomware attack unfolded in May 2021, when the gang listed the district on its leak site and a district spokesperson said they were “working to determine what information might have been affected.”
Even then, district employees told Mississippi Today, their bosses waited two weeks to loop them in on the attack and the superintendent said in a letter there was “no evidence that employee sensitive information was accessed or misused.”
One year later, in May 2022, Vicksburg Warren sent letters to breach victims informing them that their information had been compromised.
A lawyer representing the district told the Vicksburg Daily News that educators “complied with all notification requirements.”
“Due to the sophistication of the data sets and information, the processing of data for identifying potentially-affected individuals was complex and required additional time to resolve,” the statement continued.
That same month, a breach notice was submitted to regulators in Montana, though details about the types of information that were exposed were excluded.
School officials couldn’t be reached for comment.
Tigerton School District
Location: Tigerton, Wisconsin
Breach date: May 2021
A cyberattack forced the Tigerton, Wisconsin, school district to close for three days in May 2021 as district officials worked with third-party cybersecurity consultants to fend off the hackers.
School officials couldn’t be reached for comment.
Rockland Public Schools
Location: Rockland, Massachusetts
Breach date: May 2021
Info exposed: Names and Social Security numbers
The Rockland, Massachusetts, school district was the target of a ransomware attack in May 2021, which led to a breach of sensitive information including Social Security numbers.
Four Homeland Security investigators responded to the district to coach it through the recovery process, the Patriot Ledger reported, and the Rockland schools superintendent portrayed the hack as an inevitability.
“We were told there was nothing we could have done to avert this,” he told the news outlet. “Our systems were much more than adequate, we have excellent systems, and this type of breach is, as we know, happening across the country and across the world.”
Six months after the attack, in November 2021, district officials submitted a breach notice to state regulators. In total, the names and Social Security numbers of 259 people were compromised, the notice discloses.
School officials couldn’t be reached for comment.
Lancaster Independent School District
Location: Lancaster, Texas
Breach date: June 2021
Info exposed: Names, Social Security numbers and birth dates
After the Lancaster, Texas, school district fell victim to a ransomware attack in June 2021, hackers posted 9 gigabytes of stolen documents, including personal information about teachers, to the dark web.
In its initial communications, the district wouldn’t tell local reporters whether it paid a ransom but said it “immediately took affirmative steps to contain the threat,” and hired third-party cybersecurity consultants to investigate the attack.
“The District takes seriously its responsibility to protect the personal information it maintains and is continuing to enhance its existing security protocols,” Lancaster Independent said in a statement.
Focus Daily News reported on the subsequent data breach, revealing that the hack exposed payroll information with names, Social Security numbers and birth dates.
The district declined to comment.
Judson Independent School District
Location: Live Oak, Texas
Breach date: June 2021
Info exposed: Names, birth dates, addresses, Social Security numbers, medical records and financial and health insurance information
After San Antonio’s Judson Independent School District paid hackers to stop a ransomware attack in June 2021, a local media outlet accused officials of using “worn-out platitudes and scripted lines” to downplay the incident.
In an initial statement on its website, which has since been removed, the district said its systems were compromised by a “suspected but unconfirmed ransomware attack.” Judson Independent officials said they contacted law enforcement and hired third-party cybersecurity consultants “who are working around the clock, in cooperation with law enforcement, to determine the nature and extent of this attack.”
It was unclear, officials said, what information may have been stolen. They also declined to say whether they paid a ransom or whether it would be covered by insurance.
A month later, in July 2021, the district acknowledged it paid an undisclosed ransom to regain access to district technology. That amount was later revealed to be more than half a million dollars — $547,000 — according to a “large loss report” by the Maryland-based insurance company United Educators highlighting damage awards and settlements nationally exceeding $500,000.
The payment was made, the report notes, after hackers “stole personal information of thousands of teachers and students” to prevent “sensitive identifiable information from being posted.”
Still, the six-figure ransom didn’t stop a data breach, records show, which officials disclosed to state regulators in Montana.
In September 2022 — 15 months after the attack — the Montana notice states that the June 2021 ransomware attack and an investigation into the breach was concluded in April. Exposed information includes names, birth dates, addresses, Social Security numbers, medical records and financial and health insurance information.
School officials couldn’t be reached for comment.
George County School District
Location: Lucedale, Mississippi
Breach date: June 2021
When the George County School District in Lucedale, Mississippi, disclosed in June 2021 it was the target of a ransomware attack, officials said the district did not pay a ransom and that sensitive documents were kept secure.
School officials couldn’t be reached for comment.
Centinela Valley Union High School District
Location: Lawndale, California
Breach date: June 2021
Info exposed: Names, Social Security numbers, medical records and financial and health insurance information
The Centinela Valley Union High School District in Lawndale, California, was the target of a cyberattack in June 2021, according to a notice sent four months later to data breach victims.
In an October 15 letter submitted to the California attorney general’s office, the district acknowledged an unauthorized threat actor gained access to names, Social Security numbers, medical records and financial and health insurance information.
School officials couldn’t be reached for comment.
Booneville School District
Location: Booneville, Mississippi
Breach date: June 2021
Info exposed: Student records
Threat actors with the Grief ransomware gang claimed in June 2021 a cyberattack on the Booneville, Mississippi, school district.
The attack resulted in a data breach, which includes a limited number of students’ personally identifiable information, according to a review by DataBreaches.Net, a blog that tracks and reports on data breaches globally.
School officials couldn’t be reached for comment.
Batesville School District
Location: Batesville, Arkansas
Breach date: July 2021
The Batesville, Arkansas, school district was the victim of a ransomware attack in July 2021.
School information technology staff successfully stopped the attack, the district said, and no sensitive information was compromised.
School officials couldn’t be reached for comment.
Allen Independent School District
Location: Allen, Texas
Breach date: September 2021
Info exposed: Contact and vendor information and student and employee records
When cybercriminals targeted the Allen, Texas, school district in September 2021, they knew exactly who they were messing with.
“Howdy,” the hackers wrote in an email to teachers, parents and students, using the familiar Texas greeting to demand the district pay them to halt the release of sensitive information. “WE give you five days to collect money,”
The district had previously warned the community of the cyberattack, according to the local NBC TV affiliate, but claimed the attack was a failure.
Allen Independent initially said it was working with law enforcement and third-party cybersecurity consultants to investigate the incident but they hadn’t seen “any credible evidence” that personal information was exposed.
In February 2022 — five months after the attack — the district changed its story. An investigation by third-party consultants, Allen Independent said, found the attack exposed the personal information of three students and 550 current and former employees, as well as the email addresses of current and former employees and parents.
School officials couldn’t be reached for comment.
Washington Central Unified Union School District
Location: Montpelier, Vermont
Breach date: October 2021
Info exposed: Names, addresses, birth dates, education and medical records, health and financial information and Social Security numbers
When the Washington Central Unified Union School District in Montpelier, Vermont, announced in October 2021 it was the target of a suspected ransomware attack, officials notified law enforcement and hired third-party contractors to investigate.
A month later, in November 2021, the district acknowledged in a statement on its website that sensitive information had been exposed, including names, addresses, birth dates, education and medical records, health and financial information and Social Security numbers.
School officials couldn’t be reached for comment.
Janesville School District
Location: Janesville, Wisconsin
Breach date: October 2021
Threat actors with the Hive ransomware gang claimed in October 2021 a cyberattack on the Janesville, Wisconsin, school district.
No sensitive information was accessed or destroyed, the district stated on its website, and officials had not received a “ransom note indicating any demands.”
School officials couldn’t be reached for comment.
Corry Area School District
Location: Corry, Pennsylvania
Breach date: October 2021
Info exposed: Names, addresses, Social Security and phones numbers and students’ academic records
When the Corry, Pennsylvania, school district fell victim to a ransomware attack in October 2021, officials first said sensitive information had been kept secure.
A week later, however, the district acknowledged on its website that reams of information were stolen, including names, addresses, Social Security and phones numbers and students’ academic records dating back to 1995.
School officials couldn’t be reached for comment.
Beaverhead County High School District
Location: Dillon, Montana
Breach date: November 2021
Threat actors with the AvosLocker ransomware gang claimed in November 2021 a ransomware attack on the Beaverhead County High School District in Dillon, Montana.
After the attack, a blogger at DataBreaches.Net, which tracks and reports on data breaches globally, contacted the cybercriminals and asked why they would target such a small district. Hackers responded that the district “was given a free decryptor and their data was removed from our page.”
School officials couldn’t be reached for comment.
Shelley School District
Location: Shelley, Idaho
Breach date: December 2021
When the Shelley, Idaho, school district disclosed in December 2021 it was the target of a ransomware attack, officials said the FBI was notified and third-party cybersecurity consultants were hired to investigate.
Student information and district financial records were not disclosed in the attack, district officials said.
School officials couldn’t be reached for comment.
Eldon School District
Location: Eldon, Missouri
Breach date: December 2021
A cyberattack on the Eldon, Missouri, school district forced officials to cancel classes in December 2021.
The district hired third-party cybersecurity consultants to resolve the attack, district officials noted in a letter to employees, but sensitive information was not exposed.
School officials couldn’t be reached for comment.
Neenah School District
Location: Neenah, Wisconsin
Breach date: January 2022
When the Neenah, Wisconsin, school district fell victim to a ransomware attack in January 2022 by “a known international group,” officials canceled classes for what they called a “technology security situation.”
Yet when local reporters started asking questions about whether it paid a ransom, school leaders declined to provide answers.
“The attorneys have been pretty clear,” a district spokesperson told the Appleton Post-Crescent. “They don’t want to get into whether we paid or not, kind of out of threats of future attacks.”
District insurance provider Aegis directed Neenah schools to hire the law firm FisherBroyles, the news outlet reported, but the district said they “have found no evidence of any student or family information being compromised.”
In response to an inquiry from The 74, the district said it notified local and federal law enforcement “immediately upon discovering the issue.”
An initial notice to families about the incident said “there was no evidence at that time that personal information had been compromised,” but an investigation “later discovered that some staff members’ personal information may have been accessed,” according to the statement.
Officials promptly notified educators whose information was stolen, according to the statement.
Albuquerque Public Schools
Location: Albuquerque, New Mexico
Breach date: January 2022
After teachers at the Albuquerque, New Mexico, school district were flooded with phishing emails in January 2022, school officials reached out to the FBI for help.
“Multiple guys have clearly been after us for a while,” Richard Bowman, the district’s chief technology officer, wrote in an email to the federal law enforcement agency. “From my unpracticed eye, there seem to be a few different people: The Nigerians look to be the most recent, and highest volume.”
The email exchange, which The 74 obtained through a public records request, was among the early signs of a ransomware attack against New Mexico’s largest school district — an attack that forced schools to close for two days and prompted a massive incident response. Yet, years later, details of that investigation remain closely guarded, locked behind the cloak of attorney-client privilege.
The FBI was the district’s first contact, Scott Elder, who was superintendent at the time and retired in June 2024, told The 74 in an interview. Records show federal law enforcement officials collaborated with Albuquerque’s communications office on its “media position” regarding the attack. They also offered advice, Elder said, on how to react if cybercriminals demanded a ransom.
It’s guidance that would soon come in handy after the attackers made a January demand for some $400,000 in bitcoin.
“Your network has been successfully hacked and encrypted!” the cybercriminals wrote in a ransom note obtained by The 74. “The price depends on how fast you contact us :)”
The district never paid, Elder said, and officials were able to resolve the attack with the help of law enforcement, cybersecurity attorneys and forensics investigators. In March 2022, two months after the attack, the district announced it closed an investigation into the incident that “did not identify unauthorized access to or exfiltration of any data.”
Yet, records obtained by The 74 suggest at least one parent was contacted directly by the hackers, who placed a “strange call demanding money for ransoming their child.”
Although Elder said third-party consultants produced a report for the school system about the attack, the district cited attorney-client privilege when it denied The 74’s public records request for the information
Within two days of Bowman’s email to the FBI about the cyberattack, Albuquerque Public Schools turned to its cybersecurity insurance provider and sought cyber response services from the company Tracepoint. IT also retained the law firm Mullen Coughlin to “establish an attorney-client relationship” and have its lawyers take a lead role in the recovery, including the selection of “any consultants or investigators to be hired after notice to and consultation” with the district, according to a Jan. 12 contract between Albuquerque schools and the law firm.
Elder told The 74 its decision to withhold certain information about the incident, including about the district systems that were affected, wasn’t just about liability, but also about protecting itself from future attacks.
“The cyber audit gave us a good indication of what had been removed and what had not been removed and that’s about all I’m going to say,” he said, adding that the report left officials confident that the school system’s cybersecurity prevented the threat actors from taking sensitive data. “We’re being advised not to share a lot of information because, if I tell you what we did to respond, and I give you too much detail, I’m telling the hackers what we did.”
Hays Unified School District 489
Location: Hays, Kansas
Breach date: February 2022
After the Hays, Kansas, school district fell victim to a cyberattack in February 2022, parents expressed alarm. District officials, they told KWCH, had kept them out of the loop for weeks.
“When we enroll our kids, we are entering credit card numbers to pay enrollment fees and book fees and everything else,” one parent told the news outlet, but district statements failed to address whether sensitive information had been exposed.
“There is a lot of frustrated and upset parents that [were] not being told exactly what is going on, what may or may not be compromised,” the parent said. “There’s just, there’s no transparency between the school district and parents.”
School officials couldn’t be reached for comment.
Fleetwood Area School District
Location: Fleetwood, Pennsylvania
Breach date: March 2022
The Fleetwood, Pennsylvania, school district was the target of a ransomware attack in March 2022, officials acknowledged in a letter to parents.
The district announced it was working with the FBI and third-party cybersecurity consultants to resolve the attack but that sensitive information had not been exposed.
School officials couldn’t be reached for comment.
North Merrick Union Free School District
Location: North Merrick, New York
Breach date: April 2022
The North Merrick, New York, school district was the subject of a cyberattack in April 2022 when hackers broke into its surveillance system.
The ransomware compromised video servers, disabled lockdown systems and impacted badge access. Some of the systems were down for more than a week before district officials discovered the breach, News12 reported. The district told the news outlet no personal data was compromised.
School officials couldn’t be reached for comment.
Merrick Union Free School District
Location: Merrick, New York
Breach date: April 2022
The Merrick, New York, school district was the subject of a cyberattack in April 2022 when hackers broke into its surveillance system.
“The district is in a continuous cycle of improving the various technologies that we use and improving technology training. This includes updates that improve cybersecurity,” the district said in a statement to News12. “Costs for cybersecurity improvements cannot be parsed from overall technology expenditures. The district maintains cyber insurance.”
School officials couldn’t be reached for comment.
Fort Sumner Municipal Schools
Location: Fort Sumner, New Mexico
Breach date: May 2022
Info exposed: Sensitive information about students, parents and educators
Threat actors with the Cl0p ransomware gang took credit for a May 2022 cyberattack on the Fort Sumner, New Mexico, school district.
The gang uploaded sensitive information to its leak site, according to The Record, including sensitive information about parents, students and staff.
In a statement to the cybersecurity media outlet, Fort Sumner said it hired third-party cybersecurity consultants to negotiate with the hackers but “unfortunately the threat actor acted in bad faith and has released the information.”
School officials couldn’t be reached for comment.
Washington Local Schools
Location: Toledo, Ohio
Breach Date: May 2022
Washington Local Schools in Toledo, Ohio, announced they were working with third-party cybersecurity consultants to resolve a ransomware attack that targeted the district in May 2022
Two months later, in July 2022, officials said an investigation revealed that no sensitive information had been compromised in the ransomware attack.
In response to an inquiry from The 74, the district said in a statement its technology director notified federal law enforcement “shortly after the Cyber Incident Investigation Company confirmed it was indeed a cyber attack.” The company conducted an investigation and “multiple points of evidence showed that none of our data was exfiltrated.”
Through the assistance of our Cyber Insurance Carrier, a Cyber Incident Investigation Company, and one of our local technology support vendors, we were able to (a) clean, repair, and restore our systems, (b) verify that no data had been exfiltrated, and (c) construct a series of recommendations to strengthen our security,” the statement continued.
Tenafly Public Schools
Location: Tenafly, New Jersey
Breach date: June 2022
School officials in Tenafly, New Jersey, were forced to cancel final exams in June 2022 after a ransomware attack crippled its computer network. The district brought in cybersecurity consultants to help restore its systems.
School officials couldn’t be reached for comment.
Whitman-Hanson Regional School District
Location: Whitman, Massachusetts
Breach date: July 2022
Info exposed: Employee records
When the Whitman-Hanson Regional School District in Hanson, Massachusetts, announced in July 2022 it was investigating a data security breach after “external actors” attacked its computer network, officials offered an assurance.
“There is no current indication of any student, academic or household information being compromised as a result of the incident,” a communications firm representing the district announced in an August 2022 press release.
The statement didn’t make mention of employees’ records.
Nearly a year later, in June 2023, Whitman-Hanson acknowledged it had been the target of a ransomware attack that exposed unspecified information about employees.
“The District began notifying impacted individuals by mail on January 6, 2023, however, the District was unable to locate addresses for some individuals and is therefore making this public notice,” according to a press release.
School officials couldn’t be reached for comment.
Mattituck-Cutchogue School District
Location: Mattituck, New York
Breach date: July 2022
The Mattituck-Cutchogue School District in Mattituck, New York, was the target of a ransomware attack, officials acknowledged in July 2022.
In a statement, district officials said they contacted law enforcement and their insurance carrier to “determine the viability of this potential breach” and whether any sensitive information had been exposed.
Middlesex County Public Schools
Location: Saluda, Virginia
Breach date: June 2023
Info exposed: Names and Social Security numbers
Threat actors with the Akira cybergang claimed a June 2023 attack on Middlesex County Public Schools in Saluda, Virginia, threatening to release more than 500 gigabytes of data if it did not pay a ransom.
The superintendent said in a statement that it was working with the FBI and was providing information “that will hopefully prevent other schools from dealing with this issue in the future.”
“In order not to interfere with any current law enforcement efforts,” the statement continued, “we cannot provide any additional information.”
In a breach notice submitted that month to Maryland regulators, the district acknowledged it was the victim of a ransomware attack that exposed names and Social Security numbers.
School officials couldn’t be reached for comment.
Los Alamos Public Schools
Location: Los Alamos, New Mexico
Breach date: August 2022
Four months after the Los Alamos, New Mexico, school district fell victim to a ransomware attack in August 2022, the acting superintendent leaned on holiday cheer to bury the news of a subsequent data breach.
“I want to thank you all for a successful fall semester!” the schools chief said in a December 2022 letter expressing how “it has been wonderful to spend time in schools this week and see so many students thriving.”
“I am already looking forward to the start of 2023!” according to the letter, which was obtained by The 74 through a public records request.
The bombshell began in paragraph three: “One important update you need to be aware of [is that the district] experienced a cyber security incident” that exposed “certain files containing information relating to individuals.”
Los Alamos Public Schools said it would notify data breach victims directly. The types of information that were exposed and the number of affected breach victims remains unclear.
The December missive offered a vague reassurance: “If you do not receive a letter, your personal information is likely not contained within the downloaded files.”
School officials couldn’t be reached for comment.
Little Rock School District
Location: Little Rock, Arkansas
Breach date: December 2022
The Little Rock, Arkansas, school board voted in December 2022 to pay a ransom after it fell victim to a cyberattack. A school board member accidentally revealed the $250,000 price tag of the payout during a school board meeting.
“You weren’t supposed to say that, but that’s OK,” another board member said in response to the public revelation.
In a letter that month on the district’s website — which has since been removed —the school board president wrote that it hired “cyber firms and legal teams with expertise in these situations” and, on their advice, “we were told to minimize the public messaging regarding the incident, as it could cause drastic and harmful actions by the Threat Actors.”
The district was allowed to withhold records under an exemption to the state public records law, the letter said, if their release were deemed “to be detrimental to the public safety.”
A closed-door school board meeting in November “eroded public trust,” the letter states, but was necessary so the cybercriminals didn’t “act irrationally,” and to protect sensitive district cybersecurity safeguards from being further compromised.
Though the letter didn’t specify the types of information that had been stolen, it noted that data breach victims would be notified directly.
“Based on all the guidance we were given from a number of experts in the field, we were as transparent as we could be without incurring additional risks,” the letter continued. “There will always be some facts that we cannot share with the public because the release of those facts could jeopardize or impair the security, confidence and integrity of our school district.”
Bound Brook School District
Location: Bound Brook, New Jersey
Breach date: June 2023
Threat actors with the LockBit ransomware gang claimed in June 2023 that it had carried out a cyberattack on the school district in Bound Brook, New Jersey.
The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Reeds Spring School District
Location: Reeds Spring, Missouri
Breach date: June 2023
Info exposed: Names, Social Security numbers, email addresses and login credentials
Threat actors with the Karakurt ransomware gang claimed in June 2023 it carried out a cyberattack on the Reeds Spring, Missouri, school district and threatened to release 155 gigabytes of stolen information, including medical and financial records.
“The data will be uploaded during upcoming summer leaks,” the cybergang claimed on its leak site.
Four months later, in October 2023, the district notified students and staff that the cyberattack exposed their personal information, including names, Social Security numbers and email addresses.
In response to an inquiry from The 74, the district said in a statement that “when we respond to potential security incidents, our focus is on accuracy and compliance, not downplaying the severity.”
“Data breaches are complex, so we rely on cybersecurity professionals and legal advisors to ensure our response is both responsible and transparent,” a district spokesperson said in the statement. “We also consult law enforcement when appropriate, always adhering to relevant laws and keeping our community’s best interests at the forefront.”
Franklin County School District
Location: Winchester, Tennessee
Breach Date: January 2024
Spending records reveal the Franklin County School District in Winchester, Tennessee, was the target of a cyberattack in January 2024.
Five months later, in May 2024, the district paid $54,721 to the technology vendor Cybertek Solutions for the cyberattack recovery services, according to spending records obtained through the GovSpend government procurement database.
School officials couldn’t be reached for comment.
Nantucket Public Schools
Location: Nantucket, Massachusetts
Breach date: January 2023
The Nantucket, Massachusetts, school district was forced to cancel classes in January 2023 after a ransomware attack compromised the school system’s computer network.
School officials couldn’t be reached for comment.
Northport-East Northport Union Free School District
Location: Northport, New York
Breach date: August 2022
The Northport-East Northport Union Free School District in Northport, New York, was the victim of a cyberattack, spending records reveal.
In August 2022, the district paid $12,500 to the law firm Lewis Brisbois Bisgaard & Smith, which specializes in data breach response, for “legal services in connection with cyberattack incident,” according to district financial records included in the GovSpend government procurement database.
School officials couldn’t be reached for comment.
Greene County Tech School District
Location: Paragould, Arkansas
Breach Date: November 2022
The Greene County Tech School District in Paragould, Arkansas, acknowledged in November 2022 it was the target of a ransomware attack that caused phone outages but did not pose any “safety concerns.”
“We have power. We have water. And we will have a hot meal at lunch,” district leaders reassured families on social media the day of the event.
School officials couldn’t be reached for comment.
Commack School District
Location: East Northport, New York
Breach date: November 2022
The Commack School district in East Northport, New York, acknowledged in November 2022 it was the victim of a ransomware attack.
The district announced it was working closely with its cybersecurity insurance provider and had reported the attack to federal and local law enforcement.
“Ransomware such as this is a criminal act, and an investigation is currently underway,” a district spokesperson told News 12. “There is no evidence at this time that any student or staff information has been accessed.”
School officials couldn’t be reached for comment.
Plymouth School District
Location: Plymouth, Wisconsin
Breach date: January 2023
The school district in Plymouth, Wisconsin, announced in January 2023 it was the victim of a “cybersecurity incident,” backtracking on an earlier statement that it suffered a “cybersecurity breach.”
“Over the weekend, we detected a cybersecurity incident that required us to temporarily take some of our computer systems offline,” a district spokesperson told the Plymouth Review. “Until that investigation is complete and they know what actually happened, the correct term is ‘cybersecurity incident,’ which may or may not have been a breach.”
The district declined to release further information, with the spokesperson acknowledging “we are following the advice of our legal and forensic consultants with regard to the release of information.”
School officials couldn’t be reached for comment.
Swansea Public School District
Location: Swansea, Massachusetts
Breach date: January 2023
The Swansea, Massachusetts, school district was forced to cancel classes in January 2023 after a ransomware attack shut down the district’s computer network.
A third-party cybersecurity company was able to end the attack in minutes, the district said in a media release, and the superintendent said a “preliminary investigation” revealed the hack didn’t expose sensitive records.
School officials couldn’t be reached for comment.
Jefferson County Schools
Location: Birmingham, Alabama
Breach date: April 2023
Jefferson County Schools in Birmingham, Alabama, was the target of a ransomware attack in April 2023, with the district announcing it “took immediate steps” to stop the breach. A preliminary investigation did not reveal a breach of sensitive information, district officials said. School officials couldn’t be reached for comment.
Rochester Public Schools
Location: Rochester, Minnesota
Breach date: April 2023
On the same morning that school district technology officials in Rochester, Minnesota, discovered an April 2023 ransom note and a cyberattack on its computer network, education leaders turned to the school system’s $2 million cybersecurity liability insurance plan.
District emails obtained by the Post Bulletin reveal the plan covered a wide range of expenses, including legal services, crisis communications, data breach management, regulatory fines and court fees.
That same morning, the district also contacted local law enforcement and the FBI but waited for an OK from a “cyber liability insurance incident response team” to bring its systems back online “so we don’t make things worse and put us down longer.”
The district notified families the next day of “irregular activity on its network” — but only after accepting input from the public relations firm FleishmanHillard, including an edit that they refrain from using the word “cyberattack.”
“‘Cyberattack’ is severe language that we prefer to avoid when possible,” a communications firm representative wrote in an email obtained by the Post Bulletin.
School officials couldn’t be reached for comment.
Effingham County Schools
Location: Springfield, Georgia
Breach date: July 2024
Threat actors with RansomHub claimed a July 2024 cyberattack on Effingham County Schools in Springfield, Georgia, which the district confirmed on its website before removing the post.
A screenshot of the announcement by the technology consumer website Comparitech notes the district technology team “took immediate steps,” including outreach to third-party cybersecurity consultants “to terminate the unauthorized access and secure our network.”
School officials couldn’t be reached for comment.
Tuloso-Midway Independent School District
Location: Corpus Christi, Texas
Breach date: March 2022
Info exposed: Names, Social Security and driver’s license numbers, financial and health insurance information and medical records
The Tuloso-Midway Independent School District in Corpus Christi, Texas, was the target of a ransomware attack in March 2022, yet it wasn’t until November — eight months later — when it informed state regulators it suffered a data breach.
In a notice to the Texas attorney general’s office, the district disclosed that 2,311 Texas residents had their personal information compromised in the breach. Records exposed names, Social Security and driver’s license numbers, financial and health insurance information and medical records.
A notice uploaded to the district website discloses the “data security incident” occurred after an unauthorized person gained access to an employee’s email account.
The district paid $21,592 to the law firm McDonald Hopkins between June 2022 and January 2023 for “services rendered on ransomware incident,” according to records in the GovSpend government procurement database.
District insurance plans obtained by The 74 note the school system had $100,000 in cybersecurity coverage in 2022 with a $1,000 deductible. The policy covered expenses for digital forensics, legal reviews, public relations and regulatory fines and penalties.
A year later, according to its 2023 insurance policy, Tuloso-Midway got $1 million in cyber loss and liability insurance coverage with a $25,000 deductible. Coverage included forensics, identity monitoring, extortion costs and “breach coaching.”
School officials couldn’t be reached for comment.
Huffman Independent School District
Location: Huffman, Texas
Breach date: 2021
School leaders in Huffman, Texas, spent more than $57,000 in 2021 for services related to a “cybersecurity incident,” district spending records show.
Between March and September 2021, the district made eight purchases for incident response and recovery services, according to district procurement data in the GovSpend database. The 74 didn’t identify additional Information about the incident. School officials couldn’t be reached for comment.
Menominee Area Public Schools
Location: Menominee, Michigan
Breach date: 2020
Spending records suggest the Memominee, Michigan, school district suffered a ransomware attack in 2020, yet The 74 has been unable to identify additional information about the incident.
In November 2020, the district paid a cybersecurity consulting firm $10,606 for “professional services” related to ransomware, according to district spending included in the GovSpend government procurement database. That same month, it paid $1,405 to the law firm McDonald Hopkins for a “ransomware incident.” Several months later, in May 2021, the district paid $290 to McDonald Hopkins for a legal analysis and risk assessment related to the attack.
School officials couldn’t be reached for comment.
Truth or Consequences Municipal Schools
Location: Truth or Consequences, New Mexico
Breach date: December 2021
When the former superintendent of New Mexico’s Truth or Consequences Municipal Schools wrote a New Year’s letter to the school community in January 2022, she buried the news of a cyberattack.
“I hope you all had a great winter break with your families and friends,” Channell Segura, who is now a senior administrator at Albuquerque Public Schools, wrote in an email to students and obtained by The 74 through a public records request. “I am excited to see all of your faces,” she continued before pivoting to share “a few challenges that have come our way.”
First, she wrote, was the resignation of a high school principal for “personal reasons.”
“The second challenge that we are facing is that our district’s servers were hacked and encrypted by ransomware,” she wrote. The attack “has caused a major disruption to our internet access and technology platforms.”
What officials didn’t disclose publicly, records obtained by The 74 reveal, was a $42,000 ransom payment to satisfy the hacker’s extortion demands.
School officials provided 2,268 documents to The 74 in response to its public records request, excluding district files that “contain tactical response plans or procedures.” The information offers insight into the cyberattack itself and district leaders’ decision to pay off the hackers.
School officials couldn’t be reached for comment.
Beazley, the district’s cybersecurity insurance provider, was notified on December 30, 2021, of the ransomware attack, records show, and the company consented in March 2022 to the district’s “request to make a ransom payment in the amount of $42,000 to terminate the Extortion Threat.”
The type of district records the hackers may have gained access to remains unclear. But the attack caused technology problems for months, records suggest. In February, district IT staff were notified that a student was trying to use a school computer when “a ransomware notice about encryption came up.” The teacher was advised to unplug the computer from the internet and add a note that it was out of service. At the middle school, emails reveal, “entire labs were filled with sticky notes that simply read ‘doesn’t work.’”
Records show the cybersecurity insurance company played a key role in the district’s response to the ransomware attack — and at times expressed frustration with district administrators who failed to submit a “proof of loss” before a January 1, 2023, deadline. The district blamed the lapse on “turnover in our IT department.”
The insurance company recommended Truth or Consequences hire privacy lawyers from the “Beazley-approved” Polsinelli Law Firm, records show, to evaluate the district’s “obligations pursuant to Breach Notice Laws,” and services from a “Beazley-approved computer security expert” at the cybersecurity company Palo Alto Networks, “to determine the existence, causes and scope of the data breach.”
In total, the insurance company covered $227,000 in recovery expenditures, including “breach response costs” to cybersecurity lawyers, $64,000 to an incident response company for “data recovery costs” and $54,000 for the “cyber extortion loss” to Coveware, a company that negotiates with hackers and facilitates ransom payments.
Denver Public Schools
Location: Denver, Colorado
Breach date: January 2023
Info exposed: Names, Social Security numbers, employee fingerprints and health insurance and financial information
Two months after the Denver, Colorado, school district learned in January 2023 it was the target of a “cybersecurity incident,” it sent out notices informing people their sensitive information had been compromised.
The district disclosed in a March 2023 news release that an “unauthorized actor” had acquired the personally identifiable information of all district staff. Exposed records include names, Social Security numbers, employee fingerprints and health insurance and financial information.
Between March 2023 and January 2024, Denver Public Schools paid the consulting firm Kroll Associates more than $1.4 million for ransomware services and legal fees, according to district spending data included in the GovSpend government procurement database.
A statement of work obtained by The 74 through a public records request shows that Kroll was hired to analyze data related to the “potential security incident,” for lawyers to use “in providing legal advice to” the district regarding its data breach notice obligations and “in anticipation of adverse regulatory actions and litigation.”
Kroll’s services, the statement of work notes, were to be “performed at the direction” of the third-party law firm BakerHostetler “and is subject to the attorney-client privilege and/or the work product doctrine.”
School officials couldn’t be reached for comment.
Copiague Union Free School District
Location: Copiague, New York
Breach date: November 2020
The school district in Copiague, New York, was the target of a cyberattack in November 2020, records show.
A district technology official discovered while “working on a scheduled holiday” that an unauthorized threat actor had gained access to the district’s computer network, according to a data incident report to state education officials obtained by Newsday.
In June 2021, the district paid a cybersecurity firm $8,795 for “cyber attack incident response” services and $4,012 to the law firm Lewis Brisbois Bisgaard & Smith for cyberattack legal services, according to district spending records included in the GovSpend government procurement database.
School officials couldn’t be reached for comment.
Oysterponds Union Free School District
Location: Orient, New York
Breach Date: June 2020
Info exposed: Social Security numbers, addresses and financial information
Social Security numbers were exposed by cybercriminals after the Oysterponds Union Free School District in Orient, New York, was hacked in June 2020, records show.
Eight days after the attack, the district submitted a data incident report to state education officials, which was obtained by Newsday. The “hacking” incident, officials reported, resulted in fraudulent unemployment claims being filed to the Labor Department.
In total, the incident exposed the sensitive information of 12 people, according to the notice, including their Social Security numbers, addresses and financial information.
School officials couldn’t be reached for comment.
Shore Regional High School District
Location: West Long Branch, New Jersey
Breach date: April 2023
Info exposed: Names, birth dates, Social Security and driver’s license numbers, medical records and financial and health insurance information
Officials at the Shore Regional High School District in West Long Branch, New Jersey, waited more than a year to notify people that their personal information had been exposed in an April 2023 cyberattack.
In a statement on the district website, officials said they “experienced unauthorized access to our network” in April 2023 but didn’t determine until March 2024 that sensitive information had been compromised.
Exposed data include names, birth dates, Social Security and driver’s license numbers, medical records and financial and health insurance information.
School officials couldn’t be reached for comment.
Skokie-Morton Grove School District 69
Location: Skokie, Illinois
Breach date: September 2023
Info exposed: Names and Social Security numbers
The LockBit ransomware gang claimed on its leak site in September 2023 that it carried out a cyberattack on the Skokie-Morton Grove School District 69 in Skokie, Illinois.
The district acknowledged six months later — in a March 2024 breach notice to state regulators in Massachusetts — that sensitive information was compromised, including names and Social Security numbers.
In a letter to breach victims, the district said it suffered “a recent incident that may impact the privacy of certain information provided to us,” without mentioning that it had been the target of a cyberattack.
School officials couldn’t be reached for comment.
Francis Howell School District
Location: O’Fallon, Missouri
Breach date: February 2024
The Francis Howell School District in O’Fallon, Missouri, was forced to cancel classes in February 2024 after officials announced they discovered “unexpected activity” on its computer network and that cybercriminals had used malware to “encrypt certain systems.”
More than two months later, in April 2024, the district submitted a breach notice to Indiana state regulators acknowledging that the sensitive information of 6,879 people had been exposed.
School officials couldn’t be reached for comment.
Grape Creek Independent School District
Location: San Angelo, Texas
Breach Date: October 2022
The Grape Creek Independent School District in San Angelo, Texas, was the target of a cyberattack in October 2022 that led to the exposure of sensitive information, records show.
Ten months after the incident — in August 2023 — the district submitted a breach notice to state regulators in Montana, informing data breach victims that an investigation that ended in April had uncovered their personal information was exposed. However, the types of information that were stolen were redacted from the notice. School officials couldn’t be reached for comment.
New Glarus School District
Location: New Glarus, Wisconsin
Breach date: July 2022
Info exposed: Names and Social Security numbers
The New Glarus, Wisconsin, school district suffered a cyberattack in July 2022 that exposed sensitive information, including Social Security numbers, records show.
In March 2023 — some eight months after the incident — the district submitted a breach notice to Massachusetts state regulators. It includes a letter to an unknown number of victims acknowledging New Glarus had suffered a “recent data security incident” and had hired third-party cybersecurity consultants “experienced in handling these types of incidents.”
In response to an inquiry from The 74, the district said in a statement it notified local and state law enforcement and its insurance provider “on the day we learned of the attack.”
“At one point we had all of them on site, along with a representative of the Department of Public Instruction and two members of the National Guard,” according to the statement.
Peters Township School District
Location: McMurray, Pennsylvania
Breach date: Between February and April 2022
Info exposed: Names and Social Security numbers
The Peters Township School District in McMurray, Pennsylvania, became the target of a cyberattack between February and April 2022 that exposed the sensitive information of thousands of people.
In June 2023, the district disclosed the “hacking” incident to the Maine attorney general’s office, noting that the names and Social Security numbers of 12,692 people had been compromised.
School officials couldn’t be reached for comment.
Ranney School
Location: Tinton Falls, New Jersey
Breach date: August 2024
Threat actors with the Rhysida ransomware gang claimed in August 2024 that it had carried out a cyberattack on the Ranney School in Tinton Falls, New Jersey. School officials couldn’t be reached for comment.
Ringgold School District
Location: New Eagle, Pennsylvania
Breach date: November 2021
Info exposed: Names, Social Security numbers and financial information
The Ringgold School District in New Eagle, Pennsylvania, was the victim of a ransomware attack in November 2021 that exposed sensitive information, records show.
Five months later, in April 2022, an attorney with the law firm BakerHostetler submitted a breach notice on the district’s behalf to the Maryland attorney general’s office.
“Certain devices in its network had been encrypted with ransomware,” the notice to breach victims states. Exposed files include names, Social Security numbers and financial information.
School officials couldn’t be reached for comment.
Salesianum School
Location: Wilmington, Delaware
Breach date: November 2020 and September 2021
Info exposed: Names, addresses and Social Security numbers
Threat actors with the Pysa ransomware gang claimed in September 2021 that it carried out a cyberattack on the Salesianum School in Wilmington, Delaware.
The dark-web listing came several months after the all-boys Catholic school acknowledged — in June 2021 — it was the target of a ransomware attack that exposed names, addresses and Social Security numbers. The school disclosed the incident to the Maryland attorney general’s office.
In a letter submitted to Maryland regulators, a third-party attorney working for Salesianum said it was the target of a ransomware attack in November 2020 that led to a data breach.
School officials couldn’t be reached for comment.
Middleton-Cross Plains Area School District
Location: Middleton, Wisconsin
Breach date: February 2024
The Middleton-Cross Plains Area School District in Middleton, Wisconsin, was forced to cancel classes in February 2024 after experiencing what it initially called a “network interruption.”
In an update to the community later that month, officials said there was no evidence that any sensitive information had been breached.
Five months later, in July 2024, the district submitted a breach notice to Montana’s Office of Consumer Protection, acknowledging that sensitive information had been disclosed in the attack.
However, the type of information that was exposed was redacted from the notice.
In response to an inquiry from The 74, officials said it followed a “carefully crafted Incident Response Plan” created with the help of a third-party cybersecurity firm. After the district’s IT department determined it was the target of “a cyber security event,” officials contacted the district’s insurance company.
“Notices to the individuals affected were sent within the legal timeline for such matters,” the statement continued. “These notices were specific about the potentially impacted information for each person.”
Novato Unified School District
Location: Novato, California
Breach date: September 2022
Hackers used a phishing attack to gain access to the email account of a Novato Unified School District psychologist that was then “used to launch additional” attacks both inside and outside the district, school officials acknowledged in September 2022.
The breach was disclosed in an email that same month to the California attorney general’s office. However, the notice doesn’t disclose what, if any, sensitive information was stolen. School officials couldn’t be reached for comment.
Portageville School District
Location: Portageville, Missouri
Breach date: August 2021
Info exposed: Names, Social Security and driver’s license numbers, financial information and medical records
Sensitive records were compromised in an August 2021 cyberattack on the Portageville, Missouri, school district, records reveal.
Eight months later, in April 2022, the district disclosed in a notice on its website that an “unknown actor” had gained access to district technology and downloaded certain records. Breached records, the letter states, affected both current and former students, including their names, Social Security and driver’s license numbers, financial information and medical records.
School officials couldn’t be reached for comment.
Duneland School Corporation
Location: Chesterton, Indiana
Breach date: October 2021
Info exposed: Names, birth dates, Social Security and driver’s license numbers and health insurance information
The Chesterton, Indiana, school district was the target of a “data security incident” in October 2021 that exposed sensitive records, officials acknowledged.
Two months after the attack, in December 2021, the district acknowledged in a statement on its website that an “unauthorized person” gained access to records that include names, birth dates, Social Security and driver’s license numbers and health insurance information.
School officials couldn’t be reached for comment.
Monterey Peninsula Unified School District
Location: Monterey, California
Breach date: November 2021
Info exposed: Names, Social Security numbers, medical records and financial information
The Monterey, California, school district was the target of a cyberattack in November 2021 that led to what the local newspaper described as a “minor breach in data.”
In December 2021, a month after the attack, the district announced in a statement that its computer network had been accessed by an unauthorized person, exposing names, Social Security numbers, medical records and financial information.
School officials couldn’t be reached for comment.
Chester Upland School District
Location: Chester, Pennsylvania
Breach date: December 2022
Info exposed: Names, birth dates, Social Security numbers and health insurance information
Federal prosecutors accused a Nigerian thief of deploying a “romance scam” on a Florida woman and using her as a “money mule” in a cyberattack to steal and launder $13 million in state aid from the Chester, Pennsylvania, school district.
“Thanks to the quick action” of the Pennsylvania Treasurer’s Office, “this audacious attempt to steal from the school children of Chester and the taxpayers of the Commonwealth was thwarted,” Delaware County District Attorney Jack Stollsteimer said in an August 2022 news release.
Still, the fraudster made off with some $3 million, officials acknowledged, and the district was forced to report a data breach.
After the school district was hacked in December 2022, prosecutors said, a Nigerian hacker created a spoof email account for a district employee. The hacker used the email address to redirect state funds meant for Chester Upland School District into a fraudulent bank account.
The hacker allegedly used the dating website eHarmony to convince the Florida woman — a recent widow — to launder the stolen funds through her bank accounts into overseas accounts and through cryptocurrency transactions.
“The love interest was nothing more than a fictitious personality with a narrative that snared the widow on an online dating platform,” according to the press release.
Seven months later, in July 2021, the district acknowledged a data breach to state regulators in Massachusetts and Maryland, including names, birth dates, Social Security numbers and health insurance information.
The school district first observed “suspicious activity related to an employee email account” in February 2021, according to a letter submitted by an attorney with the firm Cipriani & Werner to the Maryland attorney general’s office on Chester Upland’s behalf.
An investigation found that eight employee email accounts had experienced unauthorized access over a three-month period, according to the letter, and were used to gain access to the sensitive information.
School officials couldn’t be reached for comment.
Coffeyville Unified School District 445
Location: Coffeyville, Kansas
Breach date: July 2020
Info exposed: Names and Social Security numbers
The Coffeyville, Kansas, school district experienced a cyberattack in July 2020, according to a data breach notice submitted to Montana state regulators.
Seven months later, in February 2021, the district acknowledged the incident exposed individuals’ names and Social Security numbers, according to a letter submitted to Montana’s Office of Consumer Protection.
School officials couldn’t be reached for comment.
James Irwin Charter Schools
Location: Colorado Springs, Colorado
Breach date: April 2020
James Irwin Charter Schools in Colorado Springs was the target of a cyberattack in April 2020 that led to the “unauthorized encryption of our network files,” according to a data breach notice submitted three months later to Montana regulators.
In its July 2020 data breach notice, the school said they were able to restore their network from system backups but it was “conceivable” that sensitive data was “acquired by an unauthorized third-party.”
School officials couldn’t be reached for comment.
Canton Public Schools
Location: Canton, Massachusetts
Breach date: October 2020
The Canton, Massachusetts, school district was the target of a “clear cyber event” in October 2020, according to district emails and other records obtained by The 74 through a public records request.
“FYI, We got hit with Ransomware over the weekend,” district technology administrator Michael Wentland wrote in an Oct. 13 email to his colleagues.
Just one day later, a Massachusetts-based cybersecurity company salesperson emailed the superintendent and solicited business: “Schools are quickly becoming the top target for hackers because they are easier to attack than a large corporation and the hackers can attack 10-1 schools to large corporations,” according to the sales pitch. “I find that time is of the essence after the attack.”
The district instead turned to its insurance provider, Hiscox, which confirmed it would cover most of the cyber response costs, including services from a major national consulting firm and a leading law firm.
When he heard the news, Wentland offered a sigh of relief.
“Whew !!” he wrote in an email to the district’s business administrator. “Thank God !!!”
But which companies the district was allowed to hire, records show, were subject to the insurance company’s approval.
“Please note, Sophos is not an approved vendor under your policy,” a Lewis Brisbois attorney wrote in an October 13, 2020, email to Wentland.
The district insurance policy, obtained by The 74, offered a range of cybersecurity protections, including computer forensics, breach notifications, identity protection costs and media liability.
Records obtained by The 74 did not include details on what type of district records may have been caught up in the “clear cyber event.” School officials couldn’t be reached for comment.
Hazelwood School District
Location: Florissant, Missouri
Breach date: November 2021
School district procurement records show the Hazelwood School District in Florissant, Missouri, was the target of a cyberattack in the fall of 2021.
In November 2021, the district paid a cloud service provider $5,805 for its role in Hazelwood’s “recovery for cyber attack,” according to district spending records included in the GovSpend government procurement database. School officials couldn’t be reached for comment.
Sag Harbor Union Free School District
Location: Sag Harbor, New York
Breach date: June 2020
The Sag Harbor, New York, school district was the target of a 2020 “cyber incident,” spending records show.
Records included in the GovSpend government procurement database show the district incurred costs in June 2020 for “legal services” from the law firm Nelson Mullins Riley & Scarborough to respond to the incident. School officials couldn’t be reached for comment.
Bath Local School District
Location: Lima, Ohio
Breach date: December 2020
Info exposed: Employee records
The Bath Local School District in Lima, Ohio, was the target of a ransomware attack in 2020 that likely exposed employees’ personal information, district spending records show.
In December 2020, the district paid $783 for identity theft protection services “for employees after cyber attack ransomware incident,” according to a district purchase order included in the GovSpend government procurement database. School officials couldn’t be reached for comment.
Grain Valley R-V School District
Location: Grain Valley, Missouri
Breach date: January 2023
Records suggest the Grain Valley, Missouri school district fell victim to a cyberattack and turned to a leading cybersecurity law firm for help.
In January 2023, the district paid more than $30,000 to the law firm Mullen Coughlin for “cyber security professional services,” according to district spending data included in the GovSpend government procurement database.
School officials couldn’t be reached for comment.
Robbinsville Township School District
Location: Robbinsville, New Jersey
Breach date: November 2023
The Robbinsville, New Jersey, school district was the subject of a “ cyber incident” in November 2023, district spending records show.
In January 2024, the district paid $55,000 to the law firm BakerHostetler and the consulting group Kroll Associates for “professional legal services” for the cyber incident and for “professional IT services,” according to district spending records included in the GovSpend government procurement database.
School officials couldn’t be reached for comment.
Round Lake-Brewster School District
Location: Brewster, Minnesota
Breach date: September 2022
The Brewster, Minnesota, school district spent $12,000 in fall 2022 for legal services after it fell victim to a “cyber security breach” in September, records show.
Round Lake-Brewster made the payment to the law firm Lewis Brisbois for “cyber security breach legal fees,” according to district spending records included in the GovSpend government procurement database.
School officials couldn’t be reached for comment.
Highline Public Schools
Location: Seattle, Washington
Breach date: September 2024
A ransomware attack on Highline Public Schools in Seattle, Washington, forced district leaders to cancel classes for three days in September 2024.
Students and staff returned to school but were barred from using Wi-Fi or district-issued devices for a time as the district tried to eliminate the threat, The Seattle Times reported.
School officials couldn’t be reached for comment.
Providence Public Schools
Location: Providence, Rhode Island
Breach date: September 2024
Info exposed: Names, addresses, Social Security numbers, health insurance information and disciplinary, special education and health records
After the Providence, Rhode Island, school district fell victim to a September 2024 cyberattack by the Medusa ransomware gang, school officials said an ongoing investigation found “no evidence that any personal information for students has been impacted.”
An investigation by The 74, including a review of stolen files captured in the 217-gigabyte leak, indicates otherwise. Sexual misconduct allegations involving both students and teachers, children’s special education records and their vaccine histories were posted online after Providence Public Schools did not pay the cybercriminals’ $1 million ransom demand.
The district’s failure to acknowledge that students’ records had been exposed — even after being informed otherwise by The 74 — means that parents and students are likely unaware that their private affairs have entered the public domain.
In October 2024, Providence schools notified 12,000 current and former employees that their personal information, such as their names, addresses and Social Security numbers, had been compromised. But the letter never makes mention of students’ sensitive records.
In response to The 74’s findings in mid-October 2024, a district spokesperson didn’t acknowledge that students’ sensitive information was compromised. He said the district “has been able to confirm that some [its] files” were accessed by an “unauthorized, third party,” and that “security consultants are going through a comprehensive review” to determine whether the leaked files contain personal information “for individuals beyond current and former staff members.”
Meanwhile, in an unsolicited phone call to The 74, a state education department spokesperson said that “no one had actually gone in to see the files.”
Included in the leak is the 2024-25 Individualized Education Program for a 4-year-old boy who pre-K educators observed had “significant difficulty sustaining attention to task” and who “wandered around the classroom setting without purpose.” Another special education plan notes a 3-year-old boy “randomly roamed the room humming the tune to ‘Wheels on the Bus,’ pushed chairs and threw objects.”
A single spreadsheet lists the names of some 20,000 students and their demographic information, including disability status, home addresses, contact information and parents’ names. Another contains information about their race and the languages spoken at home.
A “termination list” included in the breach notes the names of more than 600 district employees who were let go between 2002 and 2024, including an art teacher who “retired in lieu” of being fired and a middle school English teacher who “resigned per agreement.” Another set of documents reveals a fifth-grade teacher’s request — and denial — for workplace accommodations for obsessive compulsive disorder, anxiety and panic attacks that make her “less effective as an educator if I am not supported with the accommodations because I can not sleep at night.”
In one leaked April 2024 email, a senior central office administrator sought a concealed handgun permit from the state attorney general, noting they “have a safe at work as well as one at home.”
Following an investigation published by The 74 and The Boston Globe in October, the district sent a letter to families acknowledging that students’ personal information, such as vaccine records and special education details, were exposed in the attack.
In response to an inquiry from The 74, a district spokesperson said in a November statement that educators remain “committed to transparency and the security of personal information.”
“During these types of incidents, districts typically start with limited information on what occurred and then gain more information over the course of the investigation,” the statement continues. “As we navigated the initial uncertainty of the situation, PPSD prioritized taking real-time action and communicating with all stakeholders as we gathered more information.”
Huntington Beach Union High School District
Location: Huntington Beach, California
Breach date: May 2020
District spending records suggest the Huntington Beach, California, school district fell victim to a cyberattack in early 2020.
In May 2020, the district spent $34,000 for “district wide cyber incident remediation” services, according to district purchase orders included in the GovSpend government procurement database.
School officials couldn’t be reached for comment.
Winnebago Public Schools
Location: Winnebago, Nebraska
Breach date: October 2024
The school district in Winnebago, Nebraska, was forced to cancel classes in October 2024 after it suffered a cyberattack.
Threat actors with the Interlock ransomware gang took credit for the attack, claiming on its leak site it stole 223 gigabytes of district data.
School officials couldn’t be reached for comment.
Mastery Schools
Location: Philadelphia
Breach date: September 2024
Threat actors with the DragonForce ransomware group took credit in October 2024 for a cyberattack on Mastery Schools in Philadelphia.
In September, charter school leaders disclosed what it first called a “system disruption” but initially declined to elaborate on its cause.
They eventually disclosed that the system disruptions were the result of “suspicious activity attributed to an unauthorized external source.”
School officials couldn’t be reached for comment.
Cape Cod Academy
Location: Barnstable, Massachusetts
Breach date: September 2024
Cape Cod Academy in Massachusetts was the target of a ransomware attack in September 2024, the private K-12 school acknowledged in a data breach notice submitted to the state attorney general’s office.
After a month-long forensic investigation, officials determined that sensitive information had been the subject of a breach, according to a notice submitted to state regulators by the law firm Lewis Brisbois Bisgaard & Smith.
However, the types of sensitive information stolen in the attack were redacted from the notice. School officials couldn’t be reached for comment.
Marysville Schools
Location: Marysville, Ohio
Breach date: October 2024
The Marysville, Ohio, school district was forced to cancel classes after it was the target of what officials called a “cybersecurity incident” in October 2024 that caused technology disruptions.
Marysville Schools launched its incident response plan, reported the incident to federal law enforcement and sought the help of third-party cybersecurity consultants to investigate the incident, according to The Columbus Dispatch.
School officials couldn’t be reached for comment.
Floyd County Public Schools
Location: Floyd, Virginia
Breach date: August 2024
Info exposed: Employment benefit records, names, addresses, birth dates, driver’s license and Social Security numbers, health insurance and financial information and medical records
A law firm hired by the Floyd, Virginia, school district disclosed in October 2024 it was the target of a cyberattack two months earlier that forced campus closures — and that it was police who first alerted them to the suspicious activity.
A breach notice submitted to the Vermont attorney general’s office notes that the district “has unfortunately become the victim of a cybersecurity incident,” and that employees’ benefits information had been compromised by cybercriminals.
Affected information, the notice discloses, also involves records about educators and their family members, including names, addresses, birth dates, driver’s license and Social Security numbers, health insurance and financial information and medical records.
Medical records, the letter says, include “if a teacher mentioned that they were sick with the flu in a substitute teacher request.”
School officials couldn’t be reached for comment.
Henry County Schools
Location: Paris, Tennessee
Breach date: October 2024
Threat actors with the Rhysida ransomware gang claimed in October 2024 that it had carried out a cyberattack on Henry County Schools in Paris, Tennessee. School officials couldn’t be reached for comment.
Joliet Public Schools
Location: Joliet, Illinois
Breach date: May 2024
Info exposed: Names, birth dates and Social Security numbers
Threat actors with the LockBit ransomware gang claimed in July 2024 that it had carried out a cyberattack on the Joliet, Illinois, school district.
The attack began in May 2024, according to a letter submitted to data breach victims in October, some five months after the incident. The notice, submitted to the Vermont attorney general’s office, discloses that exposed information includes names, birth dates and Social Security numbers.
School officials couldn’t be reached for comment.
Fremont City School District
Location: Fremont, Ohio
Breach date: May 2024
School officials in Fremont, Ohio, disclosed in May 2024 that the district was the target of a cyberattack and that they were working with law enforcement to investigate the breach.
Local police connected the district with the FBI and the Department of Homeland Security, WTOL11 reported.
School officials couldn’t be reached for comment.
Tri-City College Prep
Location: Prescott, Arizona
Breach date: June 2024
Info exposed: Student transcripts, Social Security numbers and other “sensitive personal information”
Threat actors with the Medusa ransomware gang took credit in June 2024 for a cyberattack on Tri-City College Prep in Prescott, Arizona.
In an August 2024 data breach notice on its website, Tri-City officials disclosed a security breach involving the information of students enrolled between 2003 and 2009, including transcripts, Social Security numbers and other “sensitive personal information.”
School officials couldn’t be reached for comment.
EAGLE School
Location: Madison, Wisconsin
Breach date: September 2024
Threat actors with the Qilin ransomware gang claimed in September 2024 that it had carried out a cyberattack on the EAGLE School, a private institution in Madison, Wisconsin.
School officials couldn’t be reached for comment.
North Ridgeville City School District
Location: North Ridgeville, Ohio
Breach date: October 2024
Threat actors with the BlackSuit ransomware gang claimed in October 2024 that it had carried out a cyberattack on the North Ridgeville, Ohio, school district. School officials couldn’t be reached for comment.
Jordan Public Schools
Location: Jordan, Minnesota
Breach date: October 2024
Threat actors with the Fog ransomware gang claimed in October 2024 that it had carried out a cyberattack on the school district in Jordan, Minnesota, school district. School officials couldn’t be reached for comment.
Cottonwood Union School District
Location: Cottonwood, California
Breach date: May 2024
The Cottonwood, California, school district disclosed it was the target of a “potential network disruption” in May 2024 that gave an unauthorized third party access to sensitive records.
Data breach victims were notified five months later, according to a October 2024 data breach notice submitted to the California attorney general’s office.
The notice was redacted and the types of personally identifiable information stolen in the attack is unknown. School officials couldn’t be reached for comment.
When breaches go unspoken
The 74’s investigation into the behind-the-scenes decision-making that determines what, when and how school districts reveal cyberattacks is based on thousands of documents obtained through public records requests from more than two dozen districts and school spending data that links to the law firms, ransomware negotiators and other consultants hired to run district responses. It also includes an analysis of millions of stolen school district records uploaded to cybergangs’ leak sites.
Some of students’ most sensitive information lives indefinitely on the dark web, a hidden part of the internet that’s often used for anonymous communication and illicit activities. Other personal data can be found online with little more than a Google search — even as school districts deny that their records were stolen and cyberthieves boast about their latest score.
The 74 tracked news accounts and relied on its own investigative reporting in Los Angeles, Minneapolis, Providence, Rhode Island and St. Landry Parish, Louisiana, which uncovered the full extent of school data breaches, countering school officials’ false or misleading assertions. As a result, district administrators had to publicly acknowledge data breaches to victims or state regulators for the first time, or retract denials about the leak of thousands of students’ detailed psychological records.
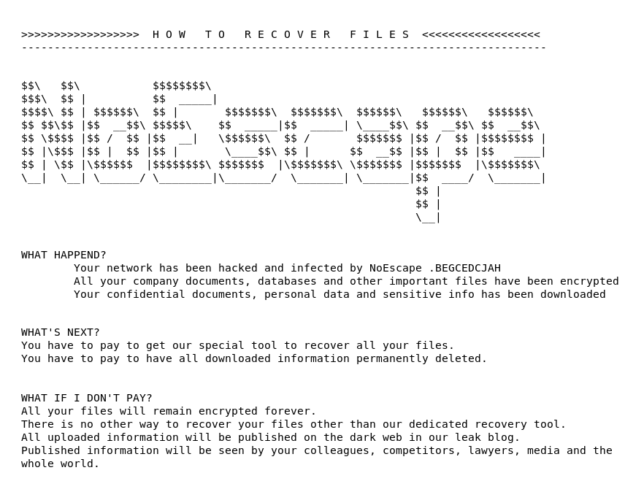
In many instances, The 74 relied on mandated data breach notices that certain states, like Maine and California, report publicly. The notices were sent to residents in these states when their personal information was compromised, including numerous times when the school that suffered the cyberattack was hundreds, and in some cases thousands, of miles away. The legally required notices repeatedly revealed discrepancies between what school districts told the public early on and what they disclosed to regulators after extensive delays.
Some schools, meanwhile, failed to disclose data breaches, which they are required to do under state privacy laws, and for dozens of others, The 74 could find no information at all about alleged school cyberattacks uncovered by its reporting — suggesting they had never before been reported or publicly acknowledged by local school officials.
Education leaders who responded to The 74’s investigation results said any lack of transparency on their part was centered on preserving the integrity of the investigation, not self-protection. School officials in Reeds Spring, Missouri, said when they respond “to potential security incidents, our focus is on accuracy and compliance, not downplaying the severity.” Those at Florida’s River City Science Academy said the school “acted promptly to assess and mitigate risks, always prioritizing the safety and privacy of our students, families and employees.”
In Hillsborough County Public Schools in Tampa, Florida, administrators in the nation’s seventh-largest district said they notified student breach victims “by email, mail and a telephone call” and “set up a special hotline for affected families to answer questions.”
Hackers have exploited officials’ public statements on cyberattacks to strengthen their bargaining position, a reality educators cite when endorsing secrecy during ransom negotiations.
“But those negotiations do not go on forever,” said Doug Levin, who advises school districts after cyberattacks and is the co-founder and national director of the nonprofit K12 Security Information eXchange. “A lot of these districts come out saying, ‘We’re not paying,’” the ransom.
“All right, well, negotiation is over,” Levin said. “You need to come clean.”

Confidentiality is king
The paid professionals who arrive in the wake of a school cyberattack are held up to the public as an encouraging sign. School leaders announce reassuringly that specialists were promptly hired to assess the damage, mitigate harm and restore their systems to working order.
This promise of control and normality is particularly potent when cyberattacks suddenly cripple school systems, forcing them to shut down for days and disable online learning tools. News reports are fond of saying that educators were forced to teach students “the old-fashioned way, with books and paper.”
But what isn’t as apparent to students, parents and district employees is that these individuals are not there to protect them — but to protect schools from them.
The extent to which this involves keeping critical information out of the public’s hands is made clear in the advice that Jo Anne Roque, vice president of risk services account management at Poms & Associates Insurance Brokers, gave to leaders of New Mexico’s Gallup-McKinley County Schools after a 2023 cyberattack.

The district had hired Kroll, which conducts forensic investigations and intelligence gathering. Contracting with a privacy attorney was also necessary, Roque wrote, to shield Kroll’s findings from public view.
“Without privacy counsel in place, public records would be accessible in the event of an information leak,” she wrote in an email to school leaders that was obtained by The 74 through a public records request. School districts routinely denied The 74’s requests for cyberattack information on the very same grounds of attorney-client privilege.
Records obtained by The 74 reveal Gallup-McKinley officials never notified the school community, state regulators or law enforcement about the attack, even after threat actors with the Hunters International ransomware gang listed the New Mexico district on its leak site in January 2024.
In California’s Sweetwater Union High School District, administrators told the public at first that a February 2023 attack was an “information technology system outage” — and then went on to pay a $175,000 ransom to the hackers who encrypted their systems. The payoff didn’t stop the leak of data for more than 22,000 people, nor did the district’s initially foggy phrasing allay public suspicion for very long.

During a March 2023 school board meeting, angry residents accused Sweetwater of being misleading and cagey. One, Kathleen Cheers, questioned whether lawyers or public relations consultants had advised school leaders to keep quiet.
“What brainiac recommended this?” asked Cheers, who wanted the district to create a presentation within 30 days outlining how the breach occurred and who “recommended the deceitful description.”
It wasn’t until June 2023 — four months after the attack — that Sweetwater notified thousands of people their records were compromised. But the district’s breach notice never says what specific records had been taken, refers to files that “may have been taken” and tells those receiving the notice that their “personal information was included in the potentially taken files.”
“Well, was my information taken or not?” April Strauss, an attorney representing current and former employees in a class action lawsuit against Sweetwater, asked The 74.
Strauss, whose clients are also suing the Las Vegas district in a similar lawsuit, accused school officials of downplaying cyberattacks “to avoid exacerbating their liability, quite frankly,” in a way that prevents families from being able to “assert their rights more competently.”
Districts’ vaguely worded breach notification letters to victims serve more to confuse than inform, she said.
“The wording in notices is disheartening,” Strauss told The 74. “It’s almost like revictimization.”
Who’s in charge
Such hedged language used in required breach notices echoes the hazy descriptions districts give the public right after they’ve been hacked. Cyberattacks were called an “encryption event” in Minneapolis; a “network security incident” in Blaine County, Idaho; “temporary network disruptions” in Chambersburg, Pennsylvania, and “anomalous activity” in Camden, New Jersey.
In several cases, consultants advised educators against using words like “breach” and “cyberattack” in their communications to the public. Less than 24 hours after school officials in Rochester, Minnesota, discovered a ransom note and an April 2023 attack on the district’s computer network, they notified families but only after accepting input from the public relations firm FleishmanHillard.
“ ‘Cyberattack’ is severe language that we prefer to avoid when possible,” the firm’s representative wrote in an email obtained by the Post Bulletin.
The district called it “irregular activity” instead.
In cases where schools are being attacked, threatened and extorted by some of the globe’s most notorious cybergangs — many with known ties to Russia — federal law enforcement officials have claimed several recent victories in arresting and indicting some of the masterminds. Yet The 74 identified instances where police took a secondary role.
In positioning themselves at the helm of cyberattack responses, attorneys have advised districts they should contact law enforcement only “in conjunction with qualified counsel.”
In some cases, including one involving the Sheldon Independent School District in Texas, insurers have approved and covered costs associated with ransom payments, often harder-to-trace bitcoin transactions that have come under law enforcement scrutiny.
The insurance companies are constantly playing catch-up trying to figure out how they can offer this protection. They see dollar signs — that everybody wants this protection — but they’re losing their butts on it.
Chester Wisniewski, Sophos Director of Global Field CTO
Biden’s Deputy National Security Advisor Anne Neuberger, writing in an October op-ed in the Financial Times, said insurers are right to demand their clients install better cybersecurity measures, like multi-factor authentication, but those who agree to pay off hackers have incentivized “payment of ransoms that fuel cyber crime ecosystems.”
“This is a troubling practice that must end,” she wrote.
Records obtained by The 74 show that in Somerset, Massachusetts, Beazley, the school district’s cybersecurity insurance provider, approved a $200,000 ransom payment after a July 2020 attack. The insurer also played a role in selecting other outside vendors for the district’s incident response, including Coveware, a cybersecurity company that specializes in negotiating with hackers.
If police were disturbed by the district’s course of action, they didn’t express it. In fact, William Tedford, then the Somerset Police Department’s technology director, requested in a July 31 email that the district furnish the threat actor’s bitcoin address “as soon as possible,” so he could share it with a Secret Service agent who “offered to track the payment with the hopes of identifying the suspect(s).”
But he was quick to defer to the district and its lawyers.

“There will be no action taken by the Secret Service without express permission from the decision-makers in this matter,” Tedford wrote. “All are aware of the sensitive nature of this matter, and information is restricted to only [the officers] directly involved.”
While ransom payments are “ethically wrong because you’re funding criminal organizations,” insurers are on the hook for helping districts recover, and the payments are a way to limit liability and save money, said Chester Wisniewski, a director at cybersecurity company Sophos.
“The insurance companies are constantly playing catch-up trying to figure out how they can offer this protection,” he told The 74. “They see dollar signs — that everybody wants this protection — but they’re losing their butts on it.”
Similarly, school districts have seen their premiums climb. In a 2024 survey of education leaders by the nonprofit Consortium for School Networking, more than half said their cyber insurance costs have increased. One Illinois school district reported its premium spiked 334% between 2021 and 2022.
Many districts told The 74 that they were quick to notify law enforcement soon after an attack and said the police, their insurance companies and their attorneys all worked in concert to respond. But a pecking order did emerge in the aftermath of several of these events examined by The 74 — one where the public did not learn what had fully happened until long after the attack.
When the Medusa ransomware gang attacked Minneapolis Public Schools in February 2023, it stole reams of sensitive information and demanded $4.5 million in bitcoin in exchange for not leaking it. District officials had a lawyer at Mullen Coughlin notify the FBI. But at the same time school officials were refusing to acknowledge publicly that they had been hit by a ransomware attack, their attorneys were telling federal law enforcement that the district almost immediately determined its network had been encrypted, promptly identified Medusa as the culprit and within a day had its “third-party forensic investigation firm” communicating with the gang “regarding the ransom.”
Mullen Coughlin then told the FBI that it was leading “a privileged investigation” into the attack and, at the school district’s request, “all questions, communication and requests in connection with this notification should be directed” to the law firm. Mullen Coughlin didn’t respond to requests for comment.
Minneapolis school officials would wait seven months before notifying more than 100,000 people that their sensitive files were exposed, including documents detailing campus rape cases, child abuse inquiries, student mental health crises and suspension reports. As of Dec. 1, all schools in Minnesota are now required to report cyberattacks to the state but that information will be anonymous and not shared with the public.
One district took such a hands-off approach, leaving cyberattack recovery to the consultants’ discretion, that they were left out of the loop and forced to issue an apology.
When an April 2023 letter to Camden educators arrived 13 months after a ransomware attack, it caused alarm. An administrator had to assure employees in an email that the New Jersey district wasn’t the target of a second attack. Third-party attorneys had sent out notices after a significant delay and without school officials’ knowledge. Taken by surprise, Camden schools were not “able to preemptively advise each of you about the notice and what it meant.”
Other school leaders said when they were in the throes of a full-blown crisis and ill-equipped to fight off cybercriminals on their own, law enforcement was not of much use and insurers and outside consultants were often their best option.
“In terms of how law enforcement can help you out, there’s really not a whole lot that can be done to be honest with you,” said Don Ringelestein, the executive director of technology at the Yorkville, Illinois, school district. When the district was hit by a cyberattack prior to the pandemic, he said, a report to the FBI went nowhere. Federal law enforcement officials didn’t respond to requests for comment.
District administrators turned to their insurance company, he said, which connected them to a breach coach, who led all aspects of the incident response under attorney-client privilege.
Northern Bedford County schools Superintendent Todd Beatty said the Pennsylvania district contacted the federal Cybersecurity & Infrastructure Security Agency to report a July 2024 attack, but “the problem is there’s not enough funding and personnel for them to be able to be responsive to incidents.”
Meanwhile, John VanWagoner, the schools superintendent in Traverse City, Michigan, claims insurance companies and third-party lawyers often leave district officials in the dark, too. Their insurance company presented school officials with the choice of several cybersecurity firms they could hire to recover from a March 2024 attack, VanWagoner said, but he “didn’t know where to go to vet if they were any good or not.”
He said it had been a community member — not a paid consultant — who first alerted district officials to the extent of the massive breach that forced school closures and involved 1.2 terabytes — or over 1,000 gigabytes — of stolen data.
“We were literally taking that right to the cyber companies and going, ‘Hey, they’re finding this, can you confirm this so that we can get a message out?’ ” he told The 74. “That is what I probably would tell you is the most frustrating part is that you’re relying on them and you’re at the mercy of that a little bit.”
The breach coach
Breach notices and other incident response records obtained by The 74 show that a small group of law firms play an outsized role in school cyberattack recovery efforts throughout the country. Among them is McDonald Hopkins, where Michigan attorney Dominic Paluzzi co-chairs a 52-lawyer data privacy and cybersecurity practice.
Some call him a breach coach. He calls himself a “quarterback.”
It’s not a time to make assumptions, to say, ‘We think this data has been compromised,’ until we know that.
Dominic Paluzzi, McDonald Hopkins attorney
After establishing attorney-client privilege, Paluzzi and his team call in outside agencies covered by a district’s cyber insurance policy — including forensic analysts, negotiators, public relations firms, data miners, notification vendors, credit-monitoring providers and call centers. Across all industries, the cybersecurity practice handled 2,300 incidents in 2023, 17% of which involved the education sector — which, Paluzzi noted, isn’t “always the best when it comes to the latest protections.”
When asked why districts’ initial response is often to deny the existence of a data breach, Paluzzi said it takes time to understand whether an event rises to that level, which would legally require disclosure and notification.
“It’s not a time to make assumptions, to say, ‘We think this data has been compromised,’ until we know that,” Paluzzi said. “If we start making assumptions and that starts our clock [on legally mandated disclosure notices], we’re going to have been in violation of a lot of the laws, and so what we say and when we say it are equally important.”
He said in the early stage, lawyers are trying to protect their client and avoid making any statements they would have to later retract or correct.
“While it often looks a bit canned and formulaic, it’s often because we just don’t know and we’re doing so many things,” Paluzzi said. “We’re trying to get it contained, ensure the threat actor is not in our environment and get up and running so we can continue with school and classes, and then we shift to what data is potentially out there and compromised.”
A data breach is confirmed, he said, only after “a full forensic review.” Paluzzi said that process can take up to a year, and often only after it’s completed are breaches disclosed and victims notified.
“We run through not only the forensics, but through that data mining and document review effort. By doing that last part, we are able to actually pinpoint for John Smith that it was his Social Security number, right, and Jane Doe, it’s your medical information,” he said. “We try, in most cases, to get to that level of specificity, and our letters are very specific.”
Targets in general that respond to cyberattacks without the help of a breach coach, according to a 2023 blog post by attorneys at the firm Troutman Pepper Locke, often fail to notify victims and, in some cases, provide more information than they should. When entities over-notify, they increase “the likelihood of a data breach class action [lawsuit] in the process.” Companies that under-notify “may reduce the likelihood of a data breach class action,” but could instead find themselves in trouble with government regulators.
For school districts and other entities that suffer data breaches, legal fees and settlements are often among their largest expenses.
Law firms like McDonald Hopkins that manage thousands of cyberattacks every year are particularly interested in privilege, said Schwarcz, the University of Minnesota law professor who wonders whether lawyers are necessarily best positioned to handle complex digital attacks.
In his 2023 Harvard Journal report, Schwarcz writes that the promise of confidentiality is breach coaches’ chief offering. By elevating the importance of attorney-client privilege, the report argues, lawyers are able to “retain their primacy” in the ever-growing and lucrative cyber incident-response sector.
Similarly, he said lawyers’ emphasis on reducing payouts to parents who sue overstates schools’ actual exposure and is another way to promote themselves as “providing a tremendous amount of value by limiting the risk of liability by providing you with a shield.”
Their efforts to lock down information and avoid paper trails, he wrote, ultimately undermine “the long-term cybersecurity of their clients and society more broadly.”

Who gets hurt
School cyberattacks have led to the widespread release of records that heighten the risk of identity theft for students and staff and trigger data breach notification laws that typically center on preventing fraud.
Yet files obtained by The 74 show school cyberattacks carry particularly devastating consequences for the nation’s most vulnerable youth. Records about sexual abuse, domestic violence and other traumatic childhood experiences are found to be at the center of leaks.
Hackers have leveraged these files, in particular, to coerce payments.
In Somerset, Massachusetts, a hacker using an encrypted email service extorted school officials with details of past sexual misconduct allegations during a district “show choir” event. The accusations were investigated by local police and no charges were filed.
“I am somewhat shocked with the contents of the files because the first file I chose at random is about a predatory/pedophilia incident described by young girls in one of your schools,” the hacker alleges in records obtained by The 74. “This is very troubling even for us. I hope you have investigated this incident and reported it to the authorities, because that is some fucked up stuff. If the other files are as good, we regret not making the price higher.”
The exposure of intimate records presents a situation where “vulnerable kids are being disadvantaged again by weak data security,” said digital privacy scholar Danielle Citron, a University of Virginia law professor whose 2022 book, The Fight for Privacy, argues that a lack of legal protections around intimate data leaves victims open to further exploitation.
“It’s not just that you have a leak of the information,” Citron told The 74. “But the leak then leads to online abuse and torment.”
Meanwhile in Minneapolis, an educator reported that someone withdrew more than $26,000 from their bank account after the district got hacked. In Glendale, California, more than 230 educators were required to verify their identity with the Internal Revenue Service after someone filed their taxes fraudulently.
In Albuquerque, where school officials said they prevented hackers from acquiring students’ personal information, a parent reported being contacted by the hackers who placed a “strange call demanding money for ransoming their child.”
Blood in the water
Nationally, about 135 state laws are devoted to student privacy. Yet all of them are “unfunded mandates” and “there’s been no enforcement that we know of,” according to Linnette Attai, a data privacy compliance consultant and president of PlayWell LLC.
All 50 states have laws that require businesses and government entities to notify victims when their personal information has been compromised, but the rules vary widely, including definitions of what constitutes a breach, the types of records that are covered, the speed at which consumers must be informed and the degree to which the information is shared with the general public.
It’s like you’re living in different privacy realities based on the state that you live in.
Anthony Hendricks, Crowe & Dunlevy attorney
It’s a regulatory environment that breach coach Anthony Hendricks, with the Oklahoma City office of law firm Crowe & Dunlevy, calls “the multiverse of madness.”
“It’s like you’re living in different privacy realities based on the state that you live in,” Hendricks said. He said federal cybersecurity rules could provide a “level playing field” for data breach victims who have fewer protections “because they live in a certain state.”
By 2026, proposed federal rules could require schools with more than 1,000 students to report cyberattacks to the Cybersecurity and Infrastructure Security Agency, a division of the Department of Homeland Security. But questions remain about what might happen to the rules under the new Trump administration and whether they would come with any accountability for school districts or any mechanism to share those reports with the public.
Companies that are accused of misleading investors about the extent of cyberattacks and data breaches can face Securities and Exchange Commission scrutiny, yet such accountability measures are lacking for public schools.
The Family Educational Rights and Privacy Act, the federal student privacy law, prohibits schools from disclosing student records but doesn’t require disclosure when outside forces cause those records to be exposed. Schools that have “a policy or practice” of routinely releasing students‘ records in violation of FERPA can lose their federal funding, but such sanctions have never been imposed since the law was enacted in 1974.
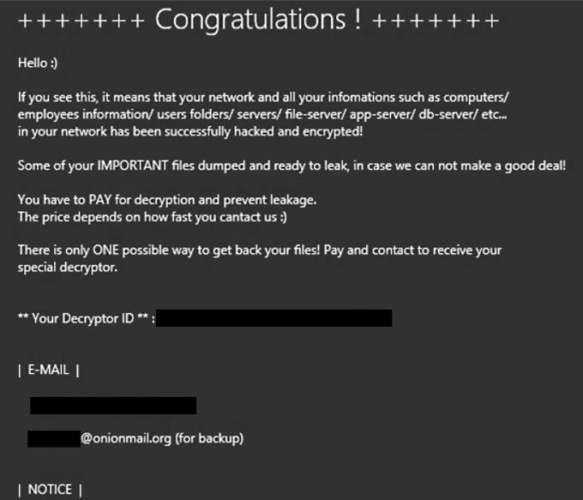
The patchwork of data breach notices are often the only mechanism alerting victims that their information is out there, but with the explosion of cyberattacks across all aspects of modern life, they’ve grown so common that some see them as little more than junk mail.
Schwarcz, the Minnesota law professor, is also a Minneapolis Public Schools parent. He told The 74 he got the district’s September 2023 breach notice in the mail but he “didn’t even read it.” The vague notices, he said, are “mostly worthless.”
It may be enforcement against districts’ misleading practices that ultimately forces school systems to act with more transparency, said Attai, the data privacy consultant. She urges educators to “communicate very carefully and very deliberately and very accurately” the known facts of cyberattacks and data breaches.
“Communities smell blood in the water,” she said, “because we’ve got these mixed messages.”
This story was supported by a grant from the Fund for Investigative Journalism.
Development and art direction by Eamonn Fitzmaurice. Illustrations by Daniel Zender for The 74.
Get stories like these delivered straight to your inbox. Sign up for The 74 Newsletter












